Abstract
Objectives
This study seeks to further strengthen extant knowledge regarding terrorist group involvement in organized criminal activity through two means. First, it measures a set of environmental and organizational characteristics for a sample of well-known terrorist organizations based on the crime-terror literature. Second, it illustrates the utility of inductive research designs for examining patterns in the criminal behavior of terrorist groups for theory building and the potential risk classification of new terrorist organizations in the future.
Methods
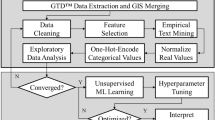
The authors utilize a random forest classification algorithm to examine three sources of information about a broad set of environmental and organizational factors determined to be of potential importance in predicting when a terrorist organization will engaged in organized criminal behavior. First, it examines out-of-sample accuracy through bootstrap cross-validation estimation. Second, it quantifies the predictive efficacy/importance of each measured factor. Finally, it utilizes partial dependence functions to examine the relational trend between the most important predictive factors and variation in the presence of organized criminal behavior.
Results
The study finds three results. First, predictive accuracy using readily quantifiable factors about the criminal behavior of terrorist organizations is good but could be improved upon. Second, organizational factors such as group size, ideology and attack behavior out perform environmental factors in terms of predictive performance. Third, it finds that the most important predictor variables have a predominately non-linear relationship with whether the algorithm would classify a group as engaging in organized criminal behavior or not.
Conclusions
The study finds that theory building should seek to examine temporal variation in the organizational structure of terrorist groups as a fruitful way forward for further understanding when a group is likely to engage in organized criminal behavior. It also suggests that scholars should seek to engage more critically with concepts surrounding the potential non-linear pathways in which groups end up engaging in organized crime. Finally, the results illustrate the utility of modern machine learning algorithms and inductive research processes for both academic and practitioner needs alike. Especially when dealing with a complex phenomenon with imperfect data.




Similar content being viewed by others
Notes
Some terrorist groups do not only carry out attacks but also have a broader functional repertoire. Hezbollah, for example, has a political wing and provides social services to their supporters (Berman and Laitin 2008).
To sell arms internationally an end-user certificate is required. It certifies that the buyer is in fact the final recipient of the arms. It is meant to ensure that arms and ammunition are not sold to an unnamed third party or embargoed states. Forging or altering end-user certificates allows shipments of arms to be transported via official channels and routes.
As discussed later in the paper, weak states support the development of criminal actors as well as terrorism. Their interaction is more likely due to their co-existence (Freeman 2011).
We include the results of a logistic regression “Appendix A” for comparison by the reader.
Within the quantitative study of terrorism, logistic regression remains the workhorse methodology for analyzing binary dependent variables. We argue that the random forest method is likely to be better for the analysis of complex problems due to its ensemble methodology and the absence of strict functional form assumptions.
There are two different types of organized crime. There are those activities that provide goods and those that provide protection. Often, the same actor provides both types of criminal activity. The Italian Mafia, for example, is providing a range of criminal activities that generates funds and deals contraband on the black market (Europol 2013). The FARC in Columbia, for example, is engaged in the production and distribution of drugs, but also provides protection to the local population against other violent actors in the area (Felbab-Brown 2010).
Cited in Forest (2013: 175).
These two examples especially highlight the puzzling nature of crime-terror cooperation. The Taliban have an explicit moral agenda that is embodied by Shari’a law yet aids the production and trade of narcotics that are considered forbidden in Islam. In Colombia, the FARC seek to establish a socialist state that would conduct land and wealth reform to aid marginalized socio-economic groups (agriculture and urban labor) yet cooperates with extremely violent and destructive drug trafficking organizations that often inflict harm on the poorest of Colombian citizens.
On the resource extraction in short-term collaborations see Saab and Taylor (2009), or Williams (2002). Of course, short-term collaboration can be a repeated event, thus resulting in long-term collaborations. The logic, however, is still operational, not motivational.
In contrast to develop causal processes underlying the terrorist group’s behavior.
Cited in Costigan and Gold (2007: 29).
Put into practice we use, for example: National Socialist Council of Nagaland + (trafficking or production) + (drugs or weapons or humans or money laundering).
For information on the operationalization of both the organizational and environmental variables see Gaibulloev and Sandler (2013).
Because our predictors are aggregated from panel measures into cross-sections, it is possible that important variation is lost during the aggregation. “Appendix B” compares the panel means and variance to the cross-sectional measures. Only transnational casualties/attack substantively deviates from the panel measure. We believe that on a whole, our aggregation procedure does not fundamentally change the distributional structure of the measures used here.
The authors practiced measurement by re-coding randomly selected cases from Kilberg’s data. This was meant to ensure coding consistency.
By aggregating organizational and environmental measures at the group level, we concede a loss of temporal information. This is problematic in that we cannot parse out time-serial structures that may be important for understanding engagement with organized crime and may mask a problem of reverse causality or a temporal lag structure that characterizes engagement. While these limitations must be acknowledged, there are two reasons for which it does not decrease the merit of this study. First, multiple indicators at the panel level are essentially time invariant in their original measurements for the group’s entire history or sizable amounts of their history (group ideology, group size, structure, etc.). Even if it was feasible to produce true time series measures of engagement, these problems would not necessarily be solved by maintaining the original panel structure. The second reason concerns our strategy. We make no attempt to estimate causal effects and instead focus on how aggregated factors at the group level may be used to accurately predict engagement between different groups and not when groups adopt or discard engagement opportunities. While these questions are important, we believe that the results here could aid in the formulation of more nuanced theories of engagement by focusing first on between group variation on engagement.
References
Asal V, Rethemeyer KR (2008) The nature of the beast: organizational structures and the lethality of terrorist attacks. J Politics 70(2):437–449
Asal V, Milward HB, Schoon EW (2014) When terrorists go bad: analyzing terrorist organizations’ involvement in drug smuggling. Int Stud Quart 59:1–12
Berk RA, Bleich J (2013) Statistical procedures for forecasting criminal behavior: a comparative assessment. Criminol Public Policy 12:513–544
Berman E, Laitin DD (2008) Religion, terrorism and public goods: testing the club model. J Public Econ 92:1942–1967
Bovenkerk F, Chakra BA (2005) Terrorism and organized crime. Forum Crime Soc 4(1&2):3–16
Breiman L (2001) Random forests. Mach Learn 45(1):5–32
Brennan T, Oliver WL (2013) Emergence of machine learning techniques in criminology: implications of complexity in our data and in research questions. Criminol Public Policy 12(3):551–562
Cairns RB, Bergman LR, Kagan J (eds) (1998) Methods and models for studying the individual. Sage Publications Inc., Thousand Oaks CA
Chenoweth E (2013) Terrorism and democracy. Annu Rev Polit Sci 16:355–378
Colaresi M, Mahmood Z (2017) Do the robot: lessons from machine learning to improve conflict forecasting. J Peace Res 54(2):193–214
Conrad J, Greene K (2015) Competition, differentiation, and the severity of terrorist attacks. J Politics 77(2):546–561
Cornell SE (2007) Narcotics and armed conflict: interaction and implications. Stud Confl Terror 30:207–227
Costigan SS, Gold D (2007) Terrornomics. Routledge, Milton Park
Crenshaw M (1981) The causes of terrorism. Comp Politics 13:379–399
Dandurand Y, Chin V (2004) Links between terrorism and other forms of crime. University of British Columbia, Vancouver
Dishman C (2001) Terrorism, crime, and transformation. Stud Confl Terror 24(1):43–58
Eccarius-Kelly V (2012) Surreptitious lifelines: a structural analysis of the FARC and the PKK. Terror Political Violence 24(2):235–258
Efron B, Tibishirani R (1997) Improvements on cross-validation: the 632+ bootstrap method. J Am Stat Assoc 92(438):548–560
Eilstrup-Sangiovanni M, Jones C (2008) Assessing the dangers of illicit networks: why Al-Qaida may be less threatening than many think. Int Secur 33(2):7–44
Eubank WL, Weinberg L (1994) Does democracy encourage terrorism? Terror Political Violence 6(4):417–435. https://doi.org/10.1080/09546559408427271
Europol (2013) Threat assesment. Italian Organized Crime, The Hague
Felbab-Brown V (2010) Shooting up: counterinsurgency and the war on drugs. Brookings Institution Press, Washington DC
Fiedler R (2008) Links Between Terrorism and Transnational Crime Groups. Books on Demand GmgH, Norderstedt
Flanigan ST (2012) Terrorists next door? A comparison of Mexican drug cartels and Middle Eastern terrorist organizations. Terror Political Violence 24(2):279–294
Forest JJF (2012) Criminals and terrorists: an introduction to the special issue. Terror Political Violence 24(2):171–179
Forest JJF (ed) (2013) Criminals and terrorists: an introduction. In: Intersections of Crime and Terror. Routledge, Milton Park, pp 1–9
Freeman M (2011) The sources of terrorist financing: theory and typology. Stud Confl Terror 34(6):461–475
Gaibulloev K, Sandler T (2013) Determinants of the demise of terrorist organizations. South Econ J 79(4):774–792
Galeotti M (2019) Hard times—organized crime and the financial crisis. Jane’s Intell Rev 21
Geltzer J-A (2011) Taking hand-outs or going it alone: nationalization versus privatization in the funding of Islamist terrorist groups. Stud Confl Terror 34(2):144–170
Giraldo J, Trinkunas H (2007) The political economy of terrorism financing. In: Giraldo J, Trinkunas H (eds) Terrorism financing and state responses. Stanford University Press, Stanford, pp 7–20
Gottfredson SD, Moriarty LJ (2006) Statistical risk assessment: old problems and new applications. Crime Delinq 52(1):178–200
Greenberg R (2010) The godfather of terror. NBC News. http://www.nbcnews.com/id/38489721/ns/dateline_nbc-international/t/godfather-terror/#.XS5PluhKjIU
Hill DW, Jones ZM (2014) An empirical evaluation of explanations for state repression. Am Polit Sci Rev 108(3):661–687
Hoffman B (2006) Inside terrorism: revised and expanded edition. Columbia University Press, New York
Horgan J, Taylor M (1999) Playing the ‘green card’—financing the provisional IRA: part 1. Terror Political Violence 11(2):1–38
Horgan J, Taylor M (2003) Playing the ‘green card’—financing the provisional IRA: part 2. Terror Political Violence 15(2):1–60
Horowitz MC, Potter PBK (2014) Allying to kill: terrorist intergroup cooperation and the consequences for lethality. J Confl Resolut 58(2):199–225. https://doi.org/10.1177/0022002712468726
Hutchinson S, O’Malley P (2007) A crime-terror nexus? Thinking on some of the links between terrorism and criminality. Stud Confl Terror 30(12):1095–1107
James G, Witten D, Hastie T, Tibishirani R (2013) An introduction to statistical learning. Springer, New York
Jongman A, Schmid AP (1988) Political terrorism: a new guide to actors, authors, concepts, data bases, theories, and literature. Transaction Publishers, New Brunswick
Kalyvas SN (2004) The paradox of terrorism in civil war. J Ethics 8(1):97–138
Kilberg J (2012) A basic model explaining terrorist group organizational structure. Stud Confl Terror 35(11):810–830
LaFree G, Freilich JD (2012) Editor’s introduction: quantitative approaches to the study of terrorism. J Quant Criminol 28:1–5
Laqueur W, Alexander Y (1978) The terrorism reader: a historical anthology. Temple University Press, Philadelphia
Libicki MC, Jones SG (2008) How terrorist groups end: lessons for countering Al Qa´ida. RAND, Santa Monica
Lo A, Chernoff H, Zheng T, Lo S-H (2015) Why significant variables aren’t automatically good predictors. Proc Natl Acad Sci 112(4):13892–13897
Makarenko T (2004) The crime-terror continuum: tracing the interplay between transnational organised crime and terrorism. Glob Crime 6(1):129–145
Meehan P (2011) Drugs, insurgency and state-building in Burma: why the drugs trade is central to Burma’s changing political order. J Southeast Asian Stud 42:376–404
Mehlum H, Moene K, Torvik R (2003) Predator or prey?: Parasitic enterprises in economic development. Eur Econ Rev 47(2):275–294
Mincheva LG, Gurr TR (2013) Crime—terror aliances and the state. Routledge, Milton Park
Muchlinski D, Siroky D, He J, Kocher M (2016) Comparing random forest with logistic regression for predicting class-imbalanced civil war onset data. Polit Anal 24(1):87–103
Mullins S (2009) Parallels between crime and terrorism: a social psychological perspective. Stud Confl Terror 32(9):811–830
Napoleoni L (2004) The new economy of terror: how terrorism is financed. Forum Crime Soc 4(1/2):31–48
Naylor RT (1993) The insurgent economy: black market operations of Guerrilla organizations. Crime Law Soc Change 20(1):13–51
Perl R (2001) Taliban and the drug trade. Congressional Research Service, Library of Congress
Piazza JA (2012) The opium trade and patterns of terrorism in the provinces of Afghanistan: an empirical analysis. Terror Political Violence 24(2):213–234
Picarelli JT (2006) The turbulent nexus of transnational organized crime and terrorism: a theory of malevolent international relations. Glob Crime 7(1):1–24
Picarelli JT (2012) Osama bin Corleone? Vito the Jackal? Framing threat convergence through an examination of transnational organized crime and international terrorism. Terror Political Violence 24(2):180–198
Podolny JM, Page KL (1998) Network forms of organization. Ann Rev Sociol 24:287–304
Préfontaine D, Dandurand Y (2004) Terrorism and organized crime: reflections on an illusive link and its implication for criminal law reform. International Society for Criminal Law Reform, Montreal
Raab J, Milward HB (2003) Dark networks as problems. J Public Adm Res Theory 13:413–439
RAND Corporation (2014) RAND database of worldwide terrorism incidents. Available at http://www.rand.org/nsrd/projects/terrorism-incidents.html
Rotberg RI (2003) State failure and state weakness in a time of terror. Brookings Institution Press, Washington DC
Rotella S (2004) “Jihad’s unlikely alliance. Los Angel Times 23:A1
Saab BY, Taylor AW (2009) Criminality and armed groups: a comparative study of FARC and paramilitary groups in Colombia. Stud Confl Terror 32(2):455–475
Sandler T, Enders W (2007) Applying analytical methods to study terrorism. Int Stud Perspect 8(3):287–302. https://doi.org/10.1111/j.1528-3585.2007.00290.x
Schelling TC (1984) What is the business of organized crime? In: Schelling TC (ed) Choice and consequence. Harvard University Press, Cambridge, pp 179–194
Schmid AP (1996) The links between transnational organized crime and terrorist crimes. Transnatl Organ Crime 2(3):40–82
Shapiro JN (2013) The terrorist’s dilemma: managing violent covert organizations. Princeton University Press, Princeton
Shelley LI (2014) Dirty entanglements—corruption, crime, and terrorism. Cambridge University Press, New Brunswick
Shelley LI, Picarelli JT (2005) Methods not motives: exploring links between transnational organized crime and international terrorism. Trends Organ Crime 9(2):52–67
Silke A (2008) Holy warriors: exploring the psychological processes of jihadi radicalization. Eur J Criminol 5(1):99–123
Sinno AH (2008) Organizations at war In Afghanistan and beyond. Cornell University Press, Ithaca
Tezcür GM, Besaw C (2017) Jihadist waves: Syria, the Islamic state, and the changing nature of foreign fighters. Conflict Manag Peace Sci. https://doi.org/10.1177/0738894217738990
UNODC (2004) United Nations Convention against transnational organized crime and the protocols thereto. UNODC, New York
UNODC (United Nations Office on Drugs, and Crime) (2010) The Globalization of Crime [electronic resource]: a transnational organized crime threat assessment. United Nations Publications
Vittori J (2011) Terrorist financing and resourcing. Palgrave MacMillan, New York
Wang P (2010) The crime-terror nexus: transformation, alliance, convergence. Asian Soc Sci 6(6):11–20
Williams P (2001) Organizing transnational crime: networks, markets and hierarchies. In: Williams P, Vlassis D (eds) Combating transnational crime. Concepts, activities and responses. Frank Cass Publishers, London, pp 57–87
Williams P (2002a) Cooperation among criminal organizations. In: Berdal M, Serrano M (eds) Transnational organized crime and international security. Lynne Rienner Publishers, Boulder
Williams P (2002b) Cooperation among criminal organizations. In: Berdal MR, Serrano M (eds) Transnational organized crime and international security: business as usual?. Boulder, Lynne Reiner, pp 67–82
Williams P (2007) Strategy for a new world: combating terrorism and transnational organized crime. In: Baylis J, Wirtz JJ, Gray CS, Cohen E (eds) Stratgy in the contemporary world: an introduction to strategic studies. Oxford University Press, Oxford, pp 192–208
Williams P (2012) The terrorism debate over mexican drug trafficking violence. Terror Political Violence 24(2):259–278
Williams P (2014) Organized crime and terrorism. LACC Working Paper No.2/2014. Miami, FL
Xu J, Chen H (2008) The topology of dark networks. Commun ACM 51(10):58–65
Young JK, Dugan L (2014) Survival of the fittest: why terrorist groups endure. Perspect Terror 8(2):2–23
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Appendices
Appendix A: Logistic Regression Coefficients
Three logistic regression models were fit to examine variable significance and importance. Table N below displays the results. The first model uses every variable outlined in the data and operationalization section. The second model uses only organizational factors, and the third model uses only environmental factors. Comparing model log likelihood, the organizational model explains a greater amount of variation when compared with the environmental factor model. The AIC statistics also indicates that organizational variables are substantively better than environmental variables for explaining variation concerning criminal activity.
Examining the fully fitted model, the logistic regression results in three statistically significant predictors. The centralized group structure dummy variable is significant at the 10% level. Substantively, the logit coefficient indicates a positive relationship between centralized organizational structure and involvement in criminal activity. The coefficient estimates a 1.82 increase in the odds of a terrorist organization being classified as having involvement in criminal activity when it has a centralized organizational structure. This finding is interesting as it contradicts theoretical and anecdotal expectations about the relationship between decentralized organizational structure and criminal involvement. Namely the expectations concerning the strategic incentive of centralized structures to avoid high-risk activities.
Group size is statistically significant and conforms to the expectations held in the literature. Group size has a positive relationship with involvement in criminal activity. The regression coefficient indicates an average classification odds increase of 1.44 as organizations increase in group size. Finally, the religious ideology dummy variable is statistically significant and indicates a strong positive relationship with criminal involvement, with religious groups having a 14.8 odds increase in being classified as having criminal involvement. This finding is difficult to reconcile with both intuition and theoretical expectations. One would expect religious groups to shy away from illicit activities, yet this finding would suggest the opposite. While not statistically significant, the nationalist ideology dummy indicates the expected relationship as found in the literature. Interestingly, none of the environmental variables are statistically significant in the full model, but military spending and logged GDP are significant in the environment model (Table 3).
Appendix B: Distributional Comparison Between Panel Measures and Aggregated Cross-sections
See Table 4.
Appendix C: Tenfold Cross Validation Estimation of Out of Sample Accuracy
Equation used for estimating tenfold cross validation accuracy. K is for each fold, while Err represents the classification error rate for each fold. The results corroborate the comparison in the main text (bootstrap validation). The random forest (75.2%) is roughly 6% more accurate in classifying out of sample cases when compared to the logistic regression (68.9%) (Figs. 5, 6).
Rights and permissions
About this article
Cite this article
Semmelbeck, J., Besaw, C. Exploring the Determinants of Crime-Terror Cooperation using Machine Learning. J Quant Criminol 36, 527–558 (2020). https://doi.org/10.1007/s10940-019-09421-0
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10940-019-09421-0