Search
Search Results
-
Quantum Query Lower Bounds for Key Recovery Attacks on the Even-Mansour Cipher
The Even-Mansour (EM) cipher is one of the famous constructions for a block cipher. Kuwakado and Morii demonstrated that a quantum adversary can...
-
The Cipher Bureau: Early Days
Herbert Yardley proceeds to set up his new Cipher Bureau in New York City. His original plans and budget run up against Congress’s determination to...
-
Never Underestimate Substitution Cipher with Diffusion
This work investigates whether a modified substitution cipher can have any cryptographic importance in today’s scenario. A classical substitution...
-
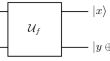
A quantum distinguisher for 7/8-round SMS4 block cipher
Constructions of quantum distinguishers (extended to key recovery attacks) for generalized Feistel networks have been recently proposed in several...
-
Lightweight Block Cipher for Resource Constrained IoT Environment—An Survey, Performance, Cryptanalysis and Research Challenges
Nowadays IoT (Internet of Things) is becoming a more popular environment and has a variety of applications like Smart Home, Smart Healthcare,...
-
An image cipher based on bio-molecular hyper chaotic system with dual diffusion scheme
Sensitive images are being transmitted over insecure media as network and information technology evolve at a rapid pace. As a result, people are...

-
An efficient and secure cipher scheme for MIMO–OFDM systems based on physical layer security
Multiple-input multiple-output orthogonal frequency division multiplexing (MIMO–OFDM) is, currently, the most dominant air interface for wireless...
-
WARP : Revisiting GFN for Lightweight 128-Bit Block Cipher
In this article, we present WARP, a lightweight 128-bit block cipher with a 128-bit key. It aims at small-footprint circuit in the field of 128-bit...
-
A survey on software implementation of lightweight block ciphers for IoT devices
Internet of things (IoT) is a computing concept that illustrates how things are connected to the internet and can communicate with other things. IoT...

-
LEDPatNet19: Automated Emotion Recognition Model based on Nonlinear LED Pattern Feature Extraction Function using EEG Signals
Electroencephalography (EEG) signals collected from human brains have generally been used to diagnose diseases. Moreover, EEG signals can be used in...

-
FASTA – A Stream Cipher for Fast FHE Evaluation
In this paper we propose Fasta, a stream cipher design optimised for implementation over popular fully homomorphic encryption schemes. A number of...
-
Fault Analysis Against Final Round of L-Block
A lightweight block cipher L-Block was presented in ACNS 2011 with various security analysis for hardware-constrained environment. Parameter such as...
-
Security Challenges and Lightweight Cryptography in IoT: Comparative Study and Testing Method for PRESENT-32bit Cipher
The Internet of Things (IoT) stands out as one of the most remarkable innovations in recent times, offering a promising future for global...
-
Lightweight architecture for fault detection in Simeck cryptographic algorithms on FPGA
Internet of Things (IoT) laid the roadmap for vast data exchange in-between resource-constrained devices such as RFID tags and nanosensors. The...

-
Output Prediction Attacks on Block Ciphers Using Deep Learning
In this paper, we propose deep learning-based output prediction attacks in a blackbox setting. As preliminary experiments, we first focus on two toy...
-
Differential Cryptanalysis of Lightweight Block Ciphers SLIM and LCB
In this paper, we analyze the security of two recently proposed ultra-lightweight block ciphers, SLIM and LCB. SLIM is designed based on the Feistel...
-
An Account of the ISO/IEC Standardization of the Simon and Speck Block Cipher Families
Simon and Speck are two block cipher families published in 2013 by the US National Security Agency (NSA). These block ciphers, targeting lightweight...
-
Comparison of PRESENT and KLEIN Ciphers Using Block RAMs of FPGA
In order to tackle the problem of data security in resource constrained devices, many lightweight ciphers have been introduced. The PRESENT and KLEIN...
-
Block Cipher Invariants as Eigenvectors of Correlation Matrices
A new approach to invariant subspaces and nonlinear invariants is developed. This results in both theoretical insights and practical attacks on block...

-
µ2 : A Lightweight Block Cipher
This paper presents a 64-bit lightweight block cipher, µ2 with a key size of 80-bit. µ2 is designed based on well-established design paradigms,...
