Search
Search Results
-
Assessing the effects of different foundation base shapes on settlement and heaving in expansive clay: numerical analysis
This paper investigates the behavior of shallow foundations with different base shapes on expansive soils under various Stresses conditions and...

-
Spatial resolution measurement method for 3D displays from contrast modulation
Augmented Reality 3D head-up displays use a autostereoscopic 3D display as a panel. The 3D optical unit of autostereoscopic 3D displays controls the...

-
Analysis of channel capacity for UWB antenna for improvements in the data rates and low Power transmission over wireless application
Multiple input- Multiple output- Ultra-wideband (MIMO-UWB) is a wireless communication approach that combines multiple antennas at the transmitter...

-
Enhancing 3D localization in wireless sensor network: a differential evolution method for the DV-Hop algorithm
Wireless sensor network is large-scale, self-organizing and reliable. It is widely used in the military, disaster management, environmental...

-
Blockchain enabled secure pharmaceutical supply chain framework with traceability: an efficient searchable pharmachain approach
The complex networks of manufacturers, suppliers, retailers, and customers that make up today’s pharmaceutical supply chain span worldwide. As it is,...

-
Energy-Constrained DAG Scheduling on Edge and Cloud Servers with Overlapped Communication and Computation
Mobile edge computing (MEC) has been widely applied to numerous areas and aspects of human life and modern society. Many such applications can be...
-
Construction of Amharic information retrieval resources and corpora
The development of information retrieval systems and natural language processing tools has been made possible for many natural languages because of...

-

-
Virtual Machine Provisioning Within Data Center Host Machines Using Ensemble Model in Cloud Computing Environment
In the digital age of exponential data proliferation and growing computing demands, efficient resource management within data centers is crucial. A...

-
Metaheuristic algorithms and their applications in wireless sensor networks: review, open issues, and challenges
Metaheuristic algorithms have wide applicability, particularly in wireless sensor networks (WSNs), due to their superior skill in solving and...

-
Generative adversarial networks for handwriting image generation: a review
Handwriting synthesis, the task of automatically generating realistic images of handwritten text, has gained increasing attention in recent years,...
-
An anonymous authentication with blockchain assisted ring-based homomorphic encryption for enhancing security in cloud computing
Nowadays, the need for cloud computing has increased due to the exponential growth in information transmission. Cybercriminals are persistent in...

-
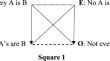
The Oppositions of Categorical Propositions in Avicenna’s Frame
The aim of this paper is to analyse categorical propositions and their oppositional relations in Avicenna’s frame. For Avicenna’s expression and...
-
A Semiautomatic Image Processing-Based Method for Binary Segmentation of Lungs in Computed Tomography Images
Precise biomedical image segmentation is pivotal in medical diagnosis and treatment. Among various methodologies, image processing-based techniques...

-
A signcryption with identity-based authentication for secure EHR sharing in IoMT utilizing ECC
Due to real-time data sharing in the Internet of Medical Things (IoMT), the healthcare sector has evolved significantly in recent years. However,...

-
Convolutional neural network (CNN) and federated learning-based privacy preserving approach for skin disease classification
This research displays inspect a study on the classification of human skin diseases using medical imaging, with a focus on data privacy preservation....

-
Exploring high-quality image deraining Transformer via effective large kernel attention
In recent years, Transformer has demonstrated significant performance in single image deraining tasks. However, the standard self-attention in the...

-
Setting a double-capacitive neuron coupled with Josephson junction and piezoelectric source
Perception of voice means acoustic electric conversion in the auditory system, and changes of external magnetic field can affect the neural...

-
Improved homomorphic evaluation for hash function based on TFHE
Homomorphic evaluation of hash functions offers a solution to the challenge of data integrity authentication in the context of homomorphic...

-
Expecting politeness: perceptions of voice assistant politeness
We examined how politeness perception can change when used by a human or voice assistant in different contexts. We conducted two norming studies and...

