Search
Search Results
-
Construction of Amharic information retrieval resources and corpora
The development of information retrieval systems and natural language processing tools has been made possible for many natural languages because of...

-

-
Virtual Machine Provisioning Within Data Center Host Machines Using Ensemble Model in Cloud Computing Environment
In the digital age of exponential data proliferation and growing computing demands, efficient resource management within data centers is crucial. A...

-
Generative adversarial networks for handwriting image generation: a review
Handwriting synthesis, the task of automatically generating realistic images of handwritten text, has gained increasing attention in recent years,...
-
Improved homomorphic evaluation for hash function based on TFHE
Homomorphic evaluation of hash functions offers a solution to the challenge of data integrity authentication in the context of homomorphic...

-
A Semiautomatic Image Processing-Based Method for Binary Segmentation of Lungs in Computed Tomography Images
Precise biomedical image segmentation is pivotal in medical diagnosis and treatment. Among various methodologies, image processing-based techniques...

-
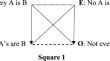
The Oppositions of Categorical Propositions in Avicenna’s Frame
The aim of this paper is to analyse categorical propositions and their oppositional relations in Avicenna’s frame. For Avicenna’s expression and...
-
Exploring high-quality image deraining Transformer via effective large kernel attention
In recent years, Transformer has demonstrated significant performance in single image deraining tasks. However, the standard self-attention in the...

-
A signcryption with identity-based authentication for secure EHR sharing in IoMT utilizing ECC
Due to real-time data sharing in the Internet of Medical Things (IoMT), the healthcare sector has evolved significantly in recent years. However,...

-
Setting a double-capacitive neuron coupled with Josephson junction and piezoelectric source
Perception of voice means acoustic electric conversion in the auditory system, and changes of external magnetic field can affect the neural...

-
Convolutional neural network (CNN) and federated learning-based privacy preserving approach for skin disease classification
This research displays inspect a study on the classification of human skin diseases using medical imaging, with a focus on data privacy preservation....

-
SDESA: secure cloud computing with gradient deep belief network and congruential advanced encryption
With the aim to enhance cloud security with higher data confidentiality rate and integrity, we propose a novel technique called Stochastic Deep...

-
Expecting politeness: perceptions of voice assistant politeness
We examined how politeness perception can change when used by a human or voice assistant in different contexts. We conducted two norming studies and...

-
Enhancing Oyente: four new vulnerability detections for improved smart contract security analysis
Enhancing the security analysis of smart contracts, particularly in Ethereum, by extending the widely used Oyente tool is the main objective of this...

-
Artistic style decomposition for texture and shape editing
While methods for generative image synthesis and example-based stylization produce impressive results, their black-box style representation...

-
A novel solution for the development of a sentimental analysis chatbot integrating ChatGPT
In today’s business landscape, Chatbots play a pivotal role in innovation and process optimization. In this paper, we introduced a novel advanced...

-
On modular (CRT-based) secret sharing
Secret sharing scheme (SSS) allows to share some secret s among n parties in such a way that only certain subsets of them can recover the secret. The...

-
Strategic view on the current role of AI in advancing environmental sustainability: a SWOT analysis
Sustainability has become a critical global concern, focusing on key environmental goals such as achieving net-zero emissions by 2050, reducing...

-
An enhanced QoS approach for multi-objective optimization using social spider optimization 5G enable IoMT network
Social Spider Optimization (SSO) is a swarm algorithm, based on the mating and cooperating behaviour of social spiders. This approach is basically...

