Search
Search Results
-
An innovative privacy preservation and security framework with fog nodes in enabled vanet system using hybrid encryption techniques
Effective communication between smart transportation and smart vehicles is carried out using Vehicular Ad-Hoc Networks (VANETs). Here, the VANET...

-
Optimization algorithms in security and privacy-preserving data disturbance for collaborative edge computing social IoT deep learning architectures
Edge computing is an innovative solution to cloud computing’s IoT application support issues. Due to network instability and increased attack...
-
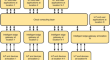
An Efficient Q-KPABE Framework to Enhance Cloud-Based IoT Security and Privacy
The Key Policy Attribute-based Encryption (KPABE) standard arises as the utmost appropriate security system for public key encipherment. KP-ABE has...
-
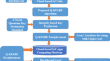
Fog computing-based IoT-enabled system security for electrical vehicles in the smart grid
Wireless sensor networks (WSNs) face significant challenges related to dependability, integrity, and confidentiality due to their widespread...
-
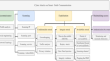
An Efficient Security Testing for Android Application Based on Behavior and Activities Using Improved PCA and DNN-KNN Classifier
Privacy and the safety of users are seriously threatened by Android, a mobile operating system that is becoming more and more popular. Due to the...

-
ERNSS-MCC: Efficient relay node selection scheme for mission critical communication using machine learning in VANET
In recent days, vehicular ad hoc networks (VANET) is advanced in communication paradigm, safety, and intelligent-based technique for message...

-
Privacy-aware access control (PAAC)-based biometric authentication protocol (Bap) for mobile edge computing environment
Since ancient times, privacy is being a greater issue. However, its impact on a subject where its significance is readily apparent has been...

-
Survey on Joint Paradigm of 5G and SDN Emerging Mobile Technologies: Architecture, Security, Challenges and Research Directions
Modern communication systems are probable to surface new challenges while introducing innovative fronts concerning context consciousness in wireless...

-
Security-aware IoT botnet attack detection framework using dilated and cascaded deep learning mechanism with conditional adversarial autoencoder-based features
The “Internet of Things (IoT)” technology has been utilized in various industries in the past few years. As the IoT technology has diverse and small...

-
Modular Encryption Standard to Improve Security of Health Information in Mobile Cloud Computing
Despite the numerous and visible benefits of mobile cloud computing (MCC) in medical care, its advancement is hampered by protection and security...
-
Cloud data transmission based on security and improved routing through hybrid machine learning techniques
A shared environment and the computer paradigm are combined in cloud computing (CC), enabling multiple users to access services and resources. This...

-
IoT Data Stream Handling, Analysis, Communication and Security Issues: A Systematic Survey
Massive data management or data stream handling has become a prominent study topic as a result of recent breakthroughs in the Internet of Things...

-
Enhanced security for IoT networks: a hybrid optimized learning model for intrusion classification
The Internet of Things (IoT) features multiple device connectivity and breaks the conventional network connectivity limitations like limited wireless...

-
Data Security and Privacy in 5G-Enabled IoT
Internet is a major communication medium for sharing data, audios, videos for various services like retrieval of information, online shop**, video...
-
Computation Infrastructure: Data Offloading, Processing, and Privacy
This chapter elaborates the computation infrastructure, namely, cloud, fog, and edge computing. Various kinds of data offloading mechanisms and a...
-
Survey of IoT Security: Application Areas, Threats and Solutions
The current communication era is commonly called the Internet of Things (IoT). The IoT facilitates data generation, reception, and transmission among...
-
Security and Energy Efficiency Enhancement for the Internet of Things: Challenges, Architecture and Future Research
Thanks to constantly advancing technology, the world is changing rapidly. One such idea that has contributed to the reality of automation is the...
-
Attacks and Threats Verification Based on 4G/5G Security Architecture
5G networks are in high demand and are expected to transform many industries, including finance, healthcare, transportation, and entertainment,...
-
End-to-end privacy preserving deep learning on multi-institutional medical imaging
Using large, multi-national datasets for high-performance medical imaging AI systems requires innovation in privacy-preserving machine learning so...

-
A survey of research on computation offloading in mobile cloud computing
Mobile devices (MDs), represented by smartphones, have been widely used in various industries. However, MDs are constrained by their limited...

