Search
Search Results
-
Near Collision Attack Against Grain V1
A near collision attack against the Grain v1 stream cipher was proposed by Zhang et al. in Eurocrypt 18. The attack uses the fact that two internal...
-
Restricted near collision attack on Plantlet
Plantlet is a recent lightweight stream cipher designed by Mikhalev, Armknecht and Müller in IACR ToSC 2017. This design paradigm receives attention...
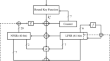
-
Ipsilateral and contralateral warnings: effects on decision-making and eye movements in near-collision scenarios
Cars are increasingly capable of providing drivers with warnings and advice. However, whether drivers should be provided with ipsilateral warnings...

-
Efficient Adaptively-Secure IB-KEMs and VRFs via Near-Collision Resistance
We construct more efficient cryptosystems with provable security against adaptive attacks, based on simple and natural hardness assumptions in the...
-
Improved (semi-free-start/near-) collision and distinguishing attacks on round-reduced RIPEMD-160
In this paper, we present an improved cryptanalysis of the double-branch hash function RIPEMD-160 standardized by ISO/IEC. First, how to...

-
Mobile robot path planning and obstacle avoidance using hybrid algorithm
Path planning of a mobile robot is a budding field of research and a significant problem to solve in robot navigation. It is widely used for...

-
Time for Traffic Manoeuvres
The use of driving assistance systems up to the level of autonomous cars asks for methods showing that cars equipped with such systems behave safely....
-
Impact Position Detection of Baseball Bat Using Multi-axis Accelerometers
In baseball, whether a batter has the ability to hit accurately is one of the key factors affecting his or her batting performance. Therefore, we...
-
Revisit Two Memoryless State-Recovery Cryptanalysis Methods on A5/1
At ASIACRYPT 2019, Zhang proposes a near collision attack on A5/1. He claims that such an attack method can recover the 64-bit A5/1 state with a time...
-
Pervasive Computing for Efficient Intra-UAV Connectivity: Based on Context-Awareness
Swarms of unmanned aerial vehicles are increasingly being utilized for a variety of operations. However, extremely variable environmental...
-
Learning practically feasible policies for online 3D bin packing
We tackle the online 3D bin packing problem (3D-BPP), a challenging yet practically useful variant of the classical bin packing problem. In this...
-
Succinct Arguments for RAM Programs via Projection Codes
Motivated by the goal of proving statements that involve small subsets of a big database, we introduce and study the notion of projection codes. A...
-
Multi-objective offline and online path planning for UAVs under dynamic urban environment
This paper presents a multi-objective hybrid path planning method MOHPP for unmanned aerial vehicles (UAVs) in urban dynamic environments. Several...

-
A scenario generation pipeline for autonomous vehicle simulators
To develop a realistic simulator for autonomous vehicle testing, the simulation of various scenarios that may occur near vehicles in the real world...

-
Hitting Enemies with Projectiles
Once you have a player you can control and a way to fire projectiles, the next step involves hitting enemies with a projectile. This involves...
-
Fast Near Collision Attack on the Grain v1 Stream Cipher
Modern stream ciphers often adopt a large internal state to resist various attacks, where the cryptanalysts have to deal with a large number of...
-
Game 1: Meteor Shower
Let's start by creating a new project called dinometeor02 by the process shown in Chapter 1.
-
Basic Hazards
Now that our player can be killed, let’s start coding up some villainy to kill them. We’ll make a generic script called Hazard that makes a...
-
Reliable and Accurate Implicit Neural Representation of Multiple Swept Volumes with Application to Safe Human–Robot Interaction
In automated production using collaborative robots in a manufacturing cell, a crucial aspect is to avoid collisions to ensure the safety of workers...

-
Enhancing Prediction Entropy Estimation of RNG for On-the-Fly Test
Random number generators (RNGs) play a vital role in cryptographic applications, and ensuring the quality of the generated random numbers is crucial....
