Search
Search Results
-
Securing edge computing using cryptographic schemes: a review
The exponential growth and wide-area applications of the Internet of Things have garnered a lot of interest from academics and industries, thus...

-
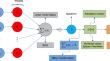
Construction of multivalued cryptographic boolean function using recurrent neural network and its application in image encryption scheme
The construction and development of new techniques for a nonlinear multivalued Boolean function is one of the important aspects of modern ciphers....
-
A novel cryptographic protocol for privacy preserving classification over distributed encrypted databases
Recent progression in Information Technology facilitated the collection and storage of large amounts of data to be accessed by multiple parties in a...

-
PROACT - Physical Attack Resistance of Cryptographic Algorithms and Circuits with Reduced Time to Market
Electronic devices that populate the Internet of Things play increasingly important roles in our everyday lives. When these devices process, store,...
-
Artificial Intelligence for the Design of Symmetric Cryptographic Primitives
This chapter provides a general overview of AI methods used to support the design of cryptographic primitives and protocols. After giving a brief...
-
Implementation of RSA cryptographic algorithm using SN P systems based on HP/LP neurons
Asymmetric cryptographic systems are often more complex and require more computational power than symmetric systems. This is why they might be...

-
Delegating Supersingular Isogenies over \(\mathbb {F}_{p^2}\) with Cryptographic Applications
Although isogeny-based cryptographic schemes enjoy the smallest key sizes amongst current post-quantum cryptographic candidates, they come at a high...
-
Towards accurate keyspace analysis of chaos-based image ciphers
In recent years, there has been a surge in new chaos-based cryptographic algorithms, many of which claim to have unusually large keyspaces. Although...

-
Advanced encryption schemes in multi-tier heterogeneous internet of things: taxonomy, capabilities, and objectives
The Internet of Things (IoT) is increasingly becoming widespread in different areas such as healthcare, transportation, and manufacturing. IoT...

-
Theoretical differential fault attacks on FLIP and FiLIP
In this article, we examine Differential Fault Attacks (DFA) targeting two stream ciphers, FLIP and FiLIP. We explore the fault model where an...

-
Model architecture level privacy leakage in neural networks
Privacy leakage is one of the most critical issues in machine learning and has attracted growing interest for tasks such as demonstrating potential...
-
A survey on lattice-based digital signature
Lattice-based digital signature has become one of the widely recognized post-quantum algorithms because of its simple algebraic operation, rich...

-
Decoding the future: exploring and comparing ABE standards for cloud, IoT, blockchain security applications
Data security poses a significant challenge in cloud computing, the Internet of Things (IoT), and blockchain applications. Attribute-Based Encryption...

-
Insights Gained After a Decade of Cellular Automata-Based Cryptography
Cellular Automata (CA) have been extensively used to implement symmetric cryptographic primitives, such as pseudorandom number generators and...
-
Hunting the pertinency of hash and bloom filter combinations on GPU for fast pattern matching
There has been rapid growth in the field of graphical processing unit (GPU) programming due to the drastic increase in the computing hardware...

-
Symmetric key-based authentication and key agreement scheme resistant against semi-trusted third party for fog and dew computing
Fog and dew computing represent relatively new computing paradigms in the literature. The main idea is to offload the computation processes from the...

-
A reversible system based on hybrid toggle radius-4 cellular automata and its application as a block cipher
The one-dimensional cellular automata (CA) system detailed herein uses a hybrid mechanism to attain reversibility, and this approach is adapted to...

-
A Quantum Physics Approach for Enabling Information-Theoretic Secure Communication Channels
Quantum communication, a field of applied quantum physics, is closely tied to quantum teleportation and quantum information processing, with a...
-
Enhancing trust and privacy in distributed networks: a comprehensive survey on blockchain-based federated learning
While centralized servers pose a risk of being a single point of failure, decentralized approaches like blockchain offer a compelling solution by...

