Search
Search Results
-
Cloud data security for distributed embedded systems using machine learning and cryptography
In the growing demand for distributed embedded systems that efficiently execute complex processes and high-end applications, safeguarding sensitive...

-
A survey on IoT & embedded device firmware security: architecture, extraction techniques, and vulnerability analysis frameworks
IoT and Embedded devices grow at an exponential rate, however, without adequate security mechanisms in place. One of the key challenges in the cyber...

-
Speech emotion recognition systems and their security aspects
Speech emotion recognition (SER) systems leverage information derived from sound waves produced by humans to identify the concealed emotions in...

-
On the Security of Smart Home Systems: A Survey
Among the plethora of IoT (Internet of Things) applications, the smart home is one of the fastest-growing. However, the rapid development of the...
-
Intelligent detection for sustainable agriculture: A review of IoT-based embedded systems, cloud platforms, DL, and ML for plant disease detection
Plant diseases pose a significant threat to the sustainability of the environment and global food security. With an increasing population density and...

-
Embedded Systems: Rules to Improve Adaptability
Embedded systems have specific properties, which are consequences of the application domain, namely the close connection to the underlying technical...
-
Winternitz stack protocols for embedded systems and IoT
This paper proposes and evaluates a new bipartite post-quantum digital signature protocol based on Winternitz chains and an oracle. Mutually...

-
Security Algorithm for Intelligent Transport System in Cyber-Physical Systems Perceptive: Attacks, Vulnerabilities, and Countermeasures
Upcoming technological innovations and findings are immense in the field of intelligent transport systems (ITS). Cyber-physical systems (CPSs) are...

-
Embedded decision support platform based on multi-agent systems
There has been an outstanding use of memory storage of processors as current applications: Artificial Intelligence-based applications,...

-
Efficient memory reuse methodology for CNN-based real-time image processing in mobile-embedded systems
Real-time image processing applications such as intelligent security and traffic management requires pattern recognition tasks, such face...

-
Embedded Ethics for Responsible Artificial Intelligence Systems (EE-RAIS) in disaster management: a conceptual model and its deployment
In this paper, we argue that Responsible Artificial Intelligence Systems (RAIS) require a shift toward embedded ethics to address value-based...

-
Who is controlling whom? Reframing “meaningful human control” of AI systems in security
Decisions in security contexts, including armed conflict, law enforcement, and disaster relief, often need to be taken under circumstances of limited...

-
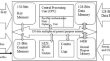
Lightweight micro-architecture for IoT & FPGA security
Cryptographic standards were created with the goal of being able to work on a wide range of systems. Small computing systems with limited capacity to...
-
SyMPLES: Embedded Systems Design with SMarty
The evolution of hardware platforms has led to the move of a large amount of functionality to embedded software systems. Thus, the software has...
-
Hel** novice developers harness security issues in cloud-IoT systems
The development of cloud-connected Internet of Things (IoT) systems is becoming more and more affordable, even to novice programmers, thanks to...

-
A Deep Learning Framework for Microarchitecture Independent Workload Characterization Technique for Multi-core Asymmetric Embedded Systems
Embedded workloads are increasing day by day and becoming more complex. The number of workloads running in the embedded processors has been growing...

-
Exception Handling in Real-Time and Embedded Systems
Modern computing not only demands precise execution but also timely and responsive actions. Nowhere is this truer than in the realm of real-time and...
-
Multiprocessing in Embedded Systems
This chapter covers multiprocessing in embedded systems. It explains the requirements of Symmetric Multiprocessing (SMP) systems and compares the...
-
Decentralized and Autonomous Key Management for Open Multi-agent Systems of Embedded Agents
This paper presents a public key infrastructure for open multi-agent systems of embedded agents. Open multi-agent systems of embedded agents are a...
-
\(\mu \) IPS: Software-Based Intrusion Prevention for Bare-Metal Embedded Systems
Many embedded systems are low-cost bare-metal systems where the firmware executes directly on hardware without an OS. Bare-metal systems typically...
