Search
Search Results
-
RBFK cipher: a randomized butterfly architecture-based lightweight block cipher for IoT devices in the edge computing environment
Internet security has become a major concern with the growing use of the Internet of Things (IoT) and edge computing technologies. Even though data...
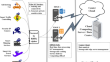
-
A lightweight and robust block cipher algorithm for real-time applications
Ensuring the protection of big data during transmission or storage represents a highly significant concern for both enterprises and individual users....

-
Robust hardware implementation of a block-cipher scheme based on chaos and biological algebraic operations
Currently, chaos-based cryptosystems are widely used for the reason of protecting sensitive data. Various different chaos-based cryptography systems...

-
SCENERY: a lightweight block cipher based on Feistel structure
In this paper, we propose a new lightweight block cipher called SCENERY. The main purpose of SCENERY design applies to hardware and software...
-
Modified lightweight GIFT cipher for security enhancement in resource-constrained IoT devices
The internet of things (IoT) ensures flexible network services to the end devices connected to it. Although security has always been a concern for...

-
A reversible system based on hybrid toggle radius-4 cellular automata and its application as a block cipher
The one-dimensional cellular automata (CA) system detailed herein uses a hybrid mechanism to attain reversibility, and this approach is adapted to...

-
Improved meet-in-the-middle attack on 10 rounds of the AES-256 block cipher
Meet-in-the-middle (MitM) attack method has led to the best currently published cryptanalytic results on the AES block cipher in the single-key...

-
SAND: an AND-RX Feistel lightweight block cipher supporting S-box-based security evaluations
We revisit designing AND-RX block ciphers, that is, the designs assembled with the most fundamental binary operations—AND, Rotation and XOR...

-
FUTURE: A Lightweight Block Cipher Using an Optimal Diffusion Matrix
In this work, we present FUTURE, a new 64-bit lightweight SPN-based block cipher. FUTURE encrypts data in a single clock cycle with a very low...
-
Improved Meet-in-the-Middle Attacks on Nine Rounds of the AES-192 Block Cipher
In the single-key attack scenario, meet-in-the-middle (MitM) attack method has led to the best currently published cryptanalytic results on the AES...
-
Quantum Query Lower Bounds for Key Recovery Attacks on the Even-Mansour Cipher
The Even-Mansour (EM) cipher is one of the famous constructions for a block cipher. Kuwakado and Morii demonstrated that a quantum adversary can...
-
The Cipher Bureau: Early Days
Herbert Yardley proceeds to set up his new Cipher Bureau in New York City. His original plans and budget run up against Congress’s determination to...
-
An image cipher based on bio-molecular hyper chaotic system with dual diffusion scheme
Sensitive images are being transmitted over insecure media as network and information technology evolve at a rapid pace. As a result, people are...

-
WARP : Revisiting GFN for Lightweight 128-Bit Block Cipher
In this article, we present WARP, a lightweight 128-bit block cipher with a 128-bit key. It aims at small-footprint circuit in the field of 128-bit...
-
FASTA – A Stream Cipher for Fast FHE Evaluation
In this paper we propose Fasta, a stream cipher design optimised for implementation over popular fully homomorphic encryption schemes. A number of...
-
Security Challenges and Lightweight Cryptography in IoT: Comparative Study and Testing Method for PRESENT-32bit Cipher
The Internet of Things (IoT) stands out as one of the most remarkable innovations in recent times, offering a promising future for global...
-
Lightweight architecture for fault detection in Simeck cryptographic algorithms on FPGA
Internet of Things (IoT) laid the roadmap for vast data exchange in-between resource-constrained devices such as RFID tags and nanosensors. The...

-
Output Prediction Attacks on Block Ciphers Using Deep Learning
In this paper, we propose deep learning-based output prediction attacks in a blackbox setting. As preliminary experiments, we first focus on two toy...
-
Differential Cryptanalysis of Lightweight Block Ciphers SLIM and LCB
In this paper, we analyze the security of two recently proposed ultra-lightweight block ciphers, SLIM and LCB. SLIM is designed based on the Feistel...
-
An Account of the ISO/IEC Standardization of the Simon and Speck Block Cipher Families
Simon and Speck are two block cipher families published in 2013 by the US National Security Agency (NSA). These block ciphers, targeting lightweight...
