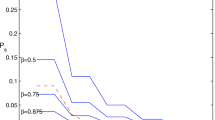
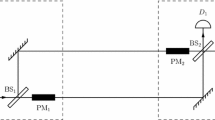
Abstract
Quantum private queries (QPQ) is an important cryptography protocol aiming to protect both the user’s and database’s privacy when the database is queried privately. Recently, a variety of practical QPQ protocols based on quantum key distribution (QKD) have been proposed. However, for QKD-based QPQ the user’s imperfect detectors can be subjected to some detector- side-channel attacks launched by the dishonest owner of the database. Here, we present a simple example that shows how the detector-blinding attack can damage the security of QKD-based QPQ completely. To remove all the known and unknown detector side channels, we propose a solution of measurement-device-independent QPQ (MDI-QPQ) with single- photon sources. The security of the proposed protocol has been analyzed under some typical attacks. Moreover, we prove that its security is completely loss independent. The results show that practical QPQ will remain the same degree of privacy as before even with seriously uncharacterized detectors.
Similar content being viewed by others
Introduction
An ideal symmetrically private information retrieval (SPIR) protocol1 allows a user, e.g. Alice, to extract an item of a database without revealing any information about which one she has retrieved to the database owner, e.g. Bob (perfect user privacy). Meanwhile, Alice can obtain only one item in a single query (perfect database privacy). SPIR can be used in the internet search and online transactions for the valuable and sensitive information. A SPIR protocol is a 1-out-of-N oblivious transfer (OT) protocol essentially2. In the 1-out-of-N OT, Bob sends N bits and Alice chooses which one she obtains. At the end of the protocol Alice knows the chosen bit value but has no information about other bits, while Bob is entirely ignorant of which bit Alice received. The security of classical OT relies on the unproven computational assumptions1. Unfortunately, Lo has proven that quantum mechanics along cannot provide unconditionally secure perfect quantum OT either3. This implies the impossibility of perfect quantum SPIR. It can be concluded from Lo’s proof that if a quantum SPIR has perfect user privacy, then Alice can perform an Einstein-Podolsky-Rosen-type4 attack to access the entire database without being detected.
Despite the no-go theorem about ideal quantum SPIR, some interesting degree of security can be achieved with changes in the model or the security requirements of the protocol. The first attempt of combining the quantum mechanics with SPIR was made by Kerenidis and De Wolf 5. However, in their protocol, the database is replicated over more than one owner and it preserves database privacy against only honest user. In 2008, Giovannetti, Lloyd and Maccone proposed a cheat sensitive quantum protocol (GLM08 protocol), named quantum private queries (QPQ), to solve the SPIR problem6. The term cheat sensitive means that Alice can catch Bob cheating with a nonvanishing (but nonunity) probability if Bob attempts to learn what Alice queries. The imperfect user privacy is the reason that QPQ can evade the no-go proof of Lo3. The security of GLM08 has been analyzed strictly7 and a proof-of-principle experiment has been implemented by De Martini et al.8. In the experiment, the bits of database were represented by an array of half-wave plates. If there existed a half-wave plate in one spatial mode, it meant that the corresponding bit was 1. Otherwise the bit was 0. For the user Alice, she prepared two non-orthogonal polarized states (the query state and test state), and sent them to Bob in a random order. The query state was routed into the desired spatial mode to obtain the retrieved bit value. Combining this value with the test state, Alice could verify the honesty of Bob with a certain probability.
The advantage of GLM08 and its improved version9 is that the communication and computational complexity has been reduced exponentially. However, the security of the protocols may be seriously compromised in the presence of losses and it will be difficult to retrieve when the dimension of the database is large. In 2011, Jakobi et al.10 proposed a QPQ protocol (J+11 protocol) based on the Scarani-Acin-Ribordy-Gisin 2004 (SARG04) quantum key distribution (QKD) protocol11. J+11 is completely impervious to losses and can be easily implemented for large database with mature QKD technology. By adjusting the coefficients of the sent states, Gao et al. made the J+11 flexible for either better user privacy or better database privacy (G+12 protocol)12. Referring to the two-way QKD scheme, the QPQ has been designed to perform better in resisting the joint-measurement attack13. The QKD-based QPQ is a very practical solution and has been generalized with other QKD protocols14,15,16. The first experimental demonstration of J+11 and G+12 has been done on a QKD system17 with some necessary modifications by Chan et al.18. In their experiment, four polarized states from two orthonormal bases were prepared randomly by Bob using the phase-randomized weak coherent state (PR-WCS) source. The faint laser pulses were transmitted to Alice trough a 12.4 km dark fiber with sequences of strong light, which acted as quantum frames17 to synchronize and compensate the time shift. Alice measured the faint pulses by passively selecting one of the bases randomly. After the classical postprocessing, including Bob announcing pairs of non-orthogonal states, key compression and error correction, Alice performed a total of 11 queries at the single-photon level. This experiment shows the feasibility of QKD-based QPQ with state-of-the-art technology. Note that the novel error-correcting code developed by Chan et al.18 and another one by Gao et al.19 to address the noise in the channel can protect the privacy of both parties. As the above QPQ protocols focused mainly on retrieving a single bit, multi-bit block QPQ has been proposed20,43. Another problem is that the projection |Ψ−〉 from the case when the parties prepare the states in bases  will introduce a high inherent error rate for Alice’s raw key. Thus, an appropriate error-correction code is needed for the correctness of the protocol. Or one can refer the setup proposed for MDI-SARG04 QKD with PR-WCS sources44. We will deal with these obstacles in the following research to make the loss-tolerant MDI-QPQ more practical.
will introduce a high inherent error rate for Alice’s raw key. Thus, an appropriate error-correction code is needed for the correctness of the protocol. Or one can refer the setup proposed for MDI-SARG04 QKD with PR-WCS sources44. We will deal with these obstacles in the following research to make the loss-tolerant MDI-QPQ more practical.
Additional Information
How to cite this article: Zhao, L.-Y. et al. Loss-tolerant measurement-device-independent quantum private queries. Sci. Rep. 7, 39733; doi: 10.1038/srep39733 (2017).
Publisher's note: Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
References
Gertner, Y., Ishai, Y., Kushilevitz, E. & Malkin, T. Protecting data privacy in private information retrieval schemes. Journal of Computer and System Sciences 60, 592–629 (2000).
Rabin, M. O. How to exchange secrets with oblivious transfer. Technical Report TR-81, Aiken Computation Lab, Harvard University (1981).
Lo, H.-K. Insecurity of quantum secure computations. Physical Review A 56, 1154 (1997).
Einstein, A., Podolsky, B. & Rosen, N. Can quantum-mechanical description of physical reality be considered complete? Physical Review 47, 777–780 (1935).
Kerenidis, I. & De Wolf, R. Quantum symmetrically-private information retrieval. Information Processing Letters 90, 109–114 (2004).
Giovannetti, V., Lloyd, S. & Maccone, L. Quantum private queries. Physical Review Letters 100, 230502 (2008).
Giovannetti, V., Lloyd, S. & Maccone, L. Quantum private queries: security analysis. IEEE Transactions on Information Theory 56, 3465–3477 (2010).
De Martini, F. et al. Experimental quantum private queries with linear optics. Physical Review A 80, 010302 (2009).
Olejnik, L. Secure quantum private information retrieval using phase-encoded queries. Physical Review A 84, 022313 (2011).
Jakobi, M. et al. Practical private database queries based on a quantum-key-distribution protocol. Physical Review A 83, 022301 (2011).
Scarani, V., Acin, A., Ribordy, G. & Gisin, N. Quantum cryptography protocols robust against photon number splitting attacks for weak laser pulse implementations. Physical Review Letters 92, 057901 (2004).
Gao, F., Liu, B., Wen, Q.-Y. & Chen, H. Flexible quantum private queries based on quantum key distribution. Optics Express 20, 17411–17420 (2012).
Wei, C.-Y., Wang, T.-Y. & Gao, F. Practical quantum private query with better performance in resisting joint-measurement attack. Physical Review A 93, 042318 (2016).
Yang, Y.-G., Sun, S.-J., Xu, P. & Tian, J. Flexible protocol for quantum private query based on b92 protocol. Quantum Information Processing 13, 805–813 (2014).
Zhang, J.-L., Guo, F.-Z., Gao, F., Liu, B. & Wen, Q.-Y. Private database queries based on counterfactual quantum key distribution. Physical Review A 88, 022334 (2013).
Liu, B., Gao, F., Huang, W. & Wen, Q. Qkd-based quantum private query without a failure probability. Science China Physics, Mechanics & Astronomy 58, 1–6 (2015).
Lucio-Martinez, I., Chan, P., Mo, X., Hosier, S. & Tittel, W. Proof-of-concept of real-world quantum key distribution with quantum frames. New Journal of Physics 11, 095001 (2009).
Chan, P., Lucio-Martinez, I., Mo, X., Simon, C. & Tittel, W. Performing private database queries in a real-world environment using a quantum protocol. Scientific Reports 4, 5233 (2014).
Gao, F., Liu, B., Huang, W. & Wen, Q.-Y. Postprocessing of the oblivious key in quantum private query. IEEE Journal of Selected Topics in Quantum Electronics 21, 1–11 (2015).
Wei, C.-Y., Gao, F., Wen, Q.-Y. & Wang, T.-Y. Practical quantum private query of blocks based on unbalanced-state bennett-brassard-1984 quantum-key-distribution protocol. Scientific Reports 4, 7537 (2014).
Wei-Xu, S., **ng-Tong, L., Jian, W. & Chao-**g, T. Multi-bit quantum private query. Communications in Theoretical Physics 64, 299 (2015).
Scarani, V. et al. The security of practical quantum key distribution. Reviews of Modern Physics 81, 1301 (2009).
Lo, H.-K., Curty, M. & Tamaki, K. Secure quantum key distribution. Nature Photonics 8, 595–604 (2014).
Qi, B., Fung, C.-H. F., Lo, H.-K. & Ma, X. Time-shift attack in practical quantum cryptosystems. Quantum Information & Computation 7, 73–82 (2007).
Makarov, V., Anisimov, A. & Skaar, J. Effects of detector efficiency mismatch on security of quantum cryptosystems. Physical Review A 74, 022313 (2006).
Lydersen, L. et al. Hacking commercial quantum cryptography systems by tailored bright illumination. Nature Photonics 4, 686–689 (2010).
Lo, H.-K., Curty, M. & Qi, B. Measurement-device-independent quantum key distribution. Physical Review Letters 108, 130503 (2012).
Rubenok, A., Slater, J. A., Chan, P., Lucio-Martinez, I. & Tittel, W. Real-world two-photon interference and proof-of-principle quantum key distribution immune to detector attacks. Physical Review Letters 111, 130501 (2013).
Liu, Y. et al. Experimental measurement-device-independent quantum key distribution. Physical Review Letters 111, 130502 (2013).
da Silva, T. F. et al. Proof-of-principle demonstration of measurement-device-independent quantum key distribution using polarization qubits. Physical Review A 88, 052303 (2013).
Tang, Z. et al. Experimental demonstration of polarization encoding measurement-device-independent quantum key distribution. Physical Review Letters 112, 190503 (2014).
Tang, Y.-L. et al. Measurement-device-independent quantum key distribution over 200 km. Physical Review Letters 113, 190501 (2014).
Wang, C. et al. Phase-reference-free experiment of measurement-device-independent quantum key distribution. Physical Review Letters 115, 160502 (2015).
Comandar, L. et al. Quantum key distribution without detector vulnerabilities using optically seeded lasers. Nature Photonics 10, 312–315 (2016).
Yin, H.-L. et al. Measurement-device-independent quantum key distribution over a 404 km optical fiber. Physical Review Letters 117, 190501 (2016).
Xu, F., Curty, M., Qi, B. & Lo, H.-K. Measurement-device-independent quantum cryptography. IEEE Journal of Selected Topics in Quantum Electronics 21, 1–11 (2015).
Zhao, L. et al. Measurement-device-independent quantum coin tossing. Physical Review A 92, 062327 (2015).
Makarov, V. Controlling passively quenched single photon detectors by bright light. New Journal of Physics 11, 065003 (2009).
Chefles, A. Unambiguous discrimination between linearly independent quantum states. Physics Letters A 6, 339–347 (1998).
Herzog, U. Optimal state discrimination with a fixed rate of inconclusive results: Analytical solutions and relation to state discrimination with a fixed error rate. Physical Review A 86, 032314 (2012).
Wootters, W. K. & Zurek, W. H. A single quantum cannot be cloned. Nature 299, 802–803 (1982).
Bae, J. Structure of minimum-error quantum state discrimination. New Journal of Physics 15, 073037 (2013).
Pappa, A., Chailloux, A., Diamanti, E. & Kerenidis, I. Practical quantum coin flip**. Physical Review A 84, 052305 (2011).
Mizutani, A., Tamaki, K., Ikuta, R., Yamamoto, T. & Imoto, N. Measurement-device-independent quantum key distribution for scarani-acin-ribordy-gisin 04 protocol. Scientific Reports 4, 5236 (2014).
Acknowledgements
The work is supported by the Strategic Priority Research Program (B) of the Chinese Academy of Sciences (Grant Nos XDB01030100 and XDB01030300), the National Key Research and Development Program of China (Grant No. 2016YFA0302600), and National Natural Science Foundation of China (Grant Nos 61475148 and 61575183).
Author information
Authors and Affiliations
Contributions
L.-Y.Z., Z.-Q.Y., W.C., G.-C.G. and Z.-F.H. conceived the project. L.-Y.Z. and Y.-J.Q. analyzed the detector-blinding attack. L.-Y.Z., Z.-Q.Y. and C.-M.Z. designed the protocol. L.-Y.Z. and Z.-Q.Y. performed the security analysis. L.-Y.Z. wrote the paper.
Corresponding author
Ethics declarations
Competing interests
The authors declare no competing financial interests.
Rights and permissions
This work is licensed under a Creative Commons Attribution 4.0 International License. The images or other third party material in this article are included in the article’s Creative Commons license, unless indicated otherwise in the credit line; if the material is not included under the Creative Commons license, users will need to obtain permission from the license holder to reproduce the material. To view a copy of this license, visit http://creativecommons.org/licenses/by/4.0/
About this article
Cite this article
Zhao, LY., Yin, ZQ., Chen, W. et al. Loss-tolerant measurement-device-independent quantum private queries. Sci Rep 7, 39733 (2017). https://doi.org/10.1038/srep39733
Received:
Accepted:
Published:
DOI: https://doi.org/10.1038/srep39733
- Springer Nature Limited
This article is cited by
-
Decoy-state method for quantum-key-distribution-based quantum private query
Science China Physics, Mechanics & Astronomy (2022)
-
Participant attack on the deterministic measurement-device-independent quantum secret sharing protocol
Science China Physics, Mechanics & Astronomy (2021)
-
Practical Quantum Database Private Query Protocol with Classical Database Owner
International Journal of Theoretical Physics (2020)
-
Practical quantum private query of blocks based on the two-dimensional QKD system
Quantum Information Processing (2019)
-
A New Protocol for Quantum Private Query Against Joint-Measurement Attack
International Journal of Theoretical Physics (2019)