Abstract
Differential attack is a basic cryptanalysis method for block ciphers that exploits the high probability relations between the input and output differences. The existing work in quantum differential cryptanalysis of block ciphers is focused on resource estimation to recover the last round subkeys on the basis of relations constructed using classical methods. To find such relations using quantum computing, we propose a method to search the high probability differential and impossible differential characteristics. The method explores all possible input and output difference pairs using superposition of qubits. The proposed method is used to design the quantum circuit to search the differential characteristics for a toy cipher smallGIFT. We execute the quantum circuit on a quantum simulator to get differential and impossible characteristics. These characteristics are validated with the characteristics obtained using branch-and-bound based method. The differential characteristic is used to mount quantum key recovery attack using Grover’s search. We provide the estimation of quantum resources to search the differential characteristics of lightweight block cipher GIFT-64 on a quantum computer.















Similar content being viewed by others
Notes
Grover’s Oracle and Diffusion source code taken from [20]
References
Augot, D., Batina, L., Bernstein, D.J., Bos, J.W., Buchmann, J.A., Castryck, W., Dunkelman, O., Güneysu, T., Gueron, S., Hülsing, A., Lange, T., Rechberger, C., Schwabe, P., Sendrier, N., Vercauteren, F., Yang, B.: Initial recommendations of long-term secure post-quantum systems (2015)
Anand, R., Maitra, A., Mukhopadhyay, S.: Evaluation of quantum cryptanalysis on speck. Progress in Cryptology, INDOCRYPT-2020, LNCS, vol. 12578, Springer, Cham (2020)
Anand, R., Maitra, A., Mukhopadhyay, S.: Grover on simon. Quantum Information Processing 19, 340 (2020)
Biham, E., Biryukov, A., Shamir, A.: Cryptanalysis of skipjack reduced to 31 rounds using impossible differentials, In: Stern, J. (ed.), advances in cryptology, EUROCRYPT’99, LNCS, vol. 1592, pp. 12-23. Springer Verlag (1999)
Bijwe, S., Chauhan, A.K., Sanadhya, S.K.: Quantum search for lightweight block ciphers: GIFT, SKINNY, SATURNIN. IACR Cryptology ePrint Archive, Report No. 2020/1485, https://eprint.iacr.org/2020/1485 (2020)
Bonnetain, X., Naya-Plasencia, M., Schrottenloher, A.: Quantum security analysis of AES. IACR Transactions on Symmetric Cryptology 2019(2), 55–93 (2019)
Banik, S., Pandey, S.K., Peyrin, T.,Sasaki, Y., Sim, S.M., Todo, Y.: GIFT: A small present - towards reaching the limit of lightweight encryption. CHES 2017, LNCS, vol. 10529, pp. 321-345, Springer (2017)
Biham, E., Shamir, A.: Differential cryptanalysis of DES-like Cryptosystems. Journal of Cryptology, vol. 4, pp. 3-72, springer (1991)
CPLEX optimizer, https://www.ibm.com/analytics/cplex-optimizer
Chauhan, A., Sanadhya, S.: Quantum Resource Estimates of Grover’s Key Search on ARIA. SPACE-2020, LNCS, vol. 12586, pp. 238-258, Springer, Cham (2020)
Fowler, A.G., Mariantoni, M., Martinis, J.M., Cleland, A.N.: Surface codes: Towards practical large-scale quantum computation. Phys. Rev., vol. 86, issue 3 (2012)
Grassl, M., Langenberg, B., Roetteler, M., Steinwandt, R.: Applying grover’s algorithm to AES: quantum resource estimates. PQCrypto 2016, LNCS, vol. 9606, pp. 29-43, Springer (2016)
Grover, L.K.: A fast quantum mechanical algorithm for database search. In: Miller, G.L. (ed.), Proceedings of the Twenty-Eighth Annual ACM Symposium on the Theory of Computing, Philadelphia, Pennsylvania, USA, May 22-24, 1996, pp. 212-219, ACM (1996)
GUROBI optimizer, https://www.gurobi.com/
Jang K., Choi S., Kwon H., Seo H.: Grover on SPECK: Quantum Resource Estimates. IACR Cryptology ePrint Archive, Report No. 2020/640, https://eprint.iacr.org/2020/640 (2020)
Jang, K.; Song, G.; Kim, H.; Kwon, H.; Kim, H.; Seo, H.: Efficient Implementation of PRESENT and GIFT on Quantum Computers. Appl. Sci. 2021, 11, 4776 (2021)
Jaques, S., Naehrig, M., Roetteler, M., Virdia, F.: Implementing grover oracles for quantum key search on AES and lowmc. EUROCRYPT 2020, LNCS, vol. 12106, pp.280-310. Springer (2020)
Jang, K., Song, G., Kwon, H., Uhm, S., Kim, H., Lee, W.K., Seo, H.: Grover on PIPO. Electronics, vol. 10, No. 10 (2021)
Kaplan, M., Leurent, G., Leverrier, A., Naya-Plasencia, M.: Quantum differential and linear cryptanalysis. IACR Transactions on Symmetric Cryptology 2016(1), 71–94 (2016)
Koch, D., Wessing, L. and Alsing, P.M.: Introduction to coding quantum algorithms: A Tutorial Series Using Qiskit. ar**v preprint ar**v:1903.04359(2019)
Kumar, M., Suresh, T.S., Pal, S.K., Panigrahi, A.: Optimal Differential Trails in Lightweight Block Ciphers ANU and PICO. Cryptologia 44(1), 68–78 (2020)
Kumar, M., Yadav, T.: MILP based differential attack on round reduced WARP. In: Batina, L., Picek, S., Mondal, M. (eds.) Security, Privacy, and Applied Cryptography Engineering. SPACE 2021. Lecture Notes in Computer Science, vol. 13162, pp. 42-59. Springer, Cham. (2022). https://doi.org/10.1007/978-3-030-95085-9_3
Leander, G., May, A.: Grover meets simon-quantumly attacking the fxconstruction. ASIACRYPT-2017, LNCS, vol. 10625, pp. 161-178 Springer, Cham (2017)
Li, H., Yang, L.: Quantum differential cryptanalysis to the block ciphers. In International Conference on Applications and Techniques in Information Security, pp. 44-51, Springer, Berlin, Heidelberg (2015)
Mouha, N., Wang, Q., Gu, D., Preneel, B.: Differential and Linear Cryptanalysis Using Mixed-Integer Linear Programming. In: Wu, C., Yung, M., Lin, D. (eds.) Inscrypt 2011, vol. 7537, LNCS, pp. 57-76. Springer (2011)
NIST: Submission requirements and evaluation criteria for the post-quantum cryptography standardization process (2016)
Shor, P.W.: Polynominal time algorithms for discrete logarithms and factoring on a quantum computer. In: Adleman, L.M., Huang, M.D. (eds.) Algorithmic Number Theory, First International Symposium, ANTS-2015, LNCS, vol. 877, pp. 289. Springer (1994)
Song, G., Jang, K., Kim, H., Eum, S., Sim, M., Kim, H., Lee, W.K., Seo, H.: Grover on SPEEDY. IACR Cryptology ePrint Archive, Report No. 2021/1211, https://eprint.iacr.org/2021/1211 (2021)
Sasaki, Y., Todo, Y.: New impossible differential search tool from design and cryptanalysis aspects - revealing structural properties of several ciphers. EUROCRYPT 2017, LNCS, vol. 10212, pp. 185-215, Springer (2017)
Yadav, T., Kumar, M.: Differential-ML distinguisher: Machine learning based generic extension for differential cryptanalysis. In: Longa, P., Rafols, C. (eds.) Progress in Cryptology- LATINCRYPT 2021, LNCS, vol. 12912, pp. 191–212. Springer, Cham (2021)
Zhou, Q., Lu, S., Zhang, Z., Sun, J.: Quantum differential cryptanalysis. Quantum Information Processing 14(6), 2101–2109 (2015)
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Appendix
Appendix
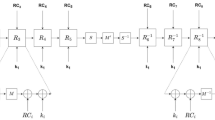
1.1 A Quantum Circuit of Differential Characteristics Search for 3 rounds of smallGIFT
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Yadav, T., Kumar, M., Kumar, A. et al. A practical-quantum differential attack on block ciphers. Cryptogr. Commun. (2023). https://doi.org/10.1007/s12095-023-00650-6
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s12095-023-00650-6