Abstract
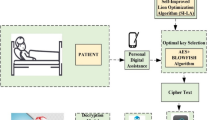
The security and privacy of healthcare data are crucial aspects within the healthcare industry, as accurate diagnoses rely on medical professionals accessing patient healthcare data. Similarly, patients often require access to their data. However, ensuring that sensitive health data is shared securely while prioritizing privacy is essential. This paper proposes an innovative solution called the quaternion based neural network, Advanced Data Security Architecture in Healthcare Environment (ADSAH), which combines Elliptical curve cryptography (ECC) with a blockchain mechanism and a Deep Fuzzy Based Neural Network (DFBNN) to safeguard cloud-stored health data. The proposed approach begins by encoding the input medical data using an encoder and then encrypting the encoded data using ECC techniques. The secret key for encrypting the data is securely stored within a blockchain framework. The key is divided into blocks to enhance security, and the SHA algorithm is employed to identify key events within these blocks. These key events are subsequently stored in a cloud storage system. A modified genetic algorithm is utilized to generate the encryption and decryption key. This algorithm is explicitly tailored to secure healthcare data. Authorized patients or physicians can access medical data using the secret key to decrypt and retrieve the necessary information. The performance of the proposed network is evaluated by considering factors such as time and cost and is compared against existing studies. The evaluation demonstrates notable improvements, including a reduction in the time required for the encryption and decryption process, as well as a decrease in transaction and execution costs when compared to previous research. By incorporating ECC with a blockchain mechanism and DNN, the ADSAH approach offers an advanced solution for ensuring the security and privacy of cloud-stored health data. It provides robust encryption and facilitates efficient and cost-effective access to authorized individuals while safeguarding sensitive health information.












Similar content being viewed by others
References
Duan X, Guo D, Liu N, Li B, Gou M and Qin C 2020 A new high capacity image steganography method combined with image elliptic curve cryptography and deep neural network. IEEE Access 8: 25777–25788
Itoo S, Khan A A, Kumar V, Alkhayyat A, Ahmad M and Srinivas J 2022 CKMIB: Construction of key agreement protocol for cloud medical infrastructure using blockchain. IEEE Access 10: 67787–67801
Zala K, Thakkar H K, Jadeja R, Singh P, Kotecha K and Shukla M 2022 PRMS: design and development of patients’ E-healthcare records management system for privacy preservation in third party cloud platforms. IEEE Access 10: 85777–85791
Haddad A, Habaebi M H, Islam M R, Hasbullah N F and Zabidi S A 2022 Systematic review on AI-blockchain based E-healthcare records management systems. IEEE Access. https://doi.org/10.1109/ACCESS.2022.3201878
Madine M M, Salah K, Jayaraman R, Yaqoob I, Al-Hammadi Y, Ellahham S and Calyam P 2020 Fully decentralized multi-party consent management for secure sharing of patient health records. IEEE Access 8: 225777–225791
Gupta D N, Kumar R and Ansari S H 2022 Federated learning for an IoT application. In: Federated Learning for IoT Applications, Springer International Publishing, Cham, pp. 53–66
Rasina Begum B and Chitra P 2021 ECC-CRT: an elliptical curve cryptographic encryption and Chinese remainder theorem based deduplication in cloud. Wirel. Pers. Commun. 116(3): 1683–1702
Hamza R, Yan Z, Muhammad K, Bellavista P and Titouna F 2020 A privacy-preserving cryptosystem for IoT E-healthcare. Inf. Sci. 527: 493–510
Ilokah M and Eklund J M 2020 A secure privacy preserving cloud-based framework for sharing electronic health data. In: 2020 42nd Annual International Conference of the IEEE Engineering in Medicine & Biology Society (EMBC), IEEE, pp. 5592–5597
Christo M S, Jesi V E, Priyadarsini U, Anbarasu V, Venugopal H and Karuppiah M 2021 Ensuring improved security in medical data using ECC and blockchain technology with edge devices. Secur. Commun. Netw. 2021: 1–13
Kwabena O A, Qin Z, Zhuang T and Qin Z 2019 Mscryptonet: multi-scheme privacy-preserving deep learning in cloud computing. IEEE Access 7: 29344–29354
An J, Fu L, Hu M, Chen W and Zhan J 2019 A novel fuzzy-based convolutional neural network method to traffic flow prediction with uncertain traffic accident information. IEEE Access 7: 20708–20722
Amosov O S, Ivanov Y S and Amosova S G 2019 Recognition of abnormal traffic using deep neural networks and fuzzy logic. In: 2019 International Multi-Conference on Industrial Engineering and Modern Technologies (FarEastCon), IEEE, pp. 01–05
Soni A and Agrawal S 2013 Key generation using genetic algorithm for image encryption. Int. J. Comput. Sci. Mob. Comput. (IJCSMC) 2(6): 376–383
Tanwar S, Parekh K and Evans R 2020 Blockchain-based electronic healthcare record system for healthcare 4.0 applications. J. Inf. Secur. Appl. 50: 102407
Adedeji K B, Nwulu N I, Aigbavboa C and Gbadamosi S L 2019 Assessment of encryption and decryption schemes for secure data transmission in healthcare systems. In: 2019 IEEE AFRICON, IEEE, pp. 1–6
Mousavi S K, Ghaffari A, Besharat S and Afshari H 2021 Improving the security of internet of things using cryptographic algorithms: a case of smart irrigation systems. J. Ambient Intell. Human. Comput. 12: 2033–2051
Osia S A, Shamsabadi A S, Sajadmanesh S, Taheri A, Katevas K, Rabiee H R, Lane N D and Haddadi H 2020 A hybrid deep learning architecture for privacy-preserving mobile analytics. IEEE Internet of Things J. 7(5): 4505–4518
Wang Z, Luo N and Zhou P 2020 GuardHealth: blockchain empowered secure data management and graph convolutional network enabled anomaly detection in smart healthcare. J. Parallel Distrib. Comput. 142: 1–12
Wu T Y, Yang L, Lee Z, Chen C M, Pan J S and Islam S H 2021 Improved ECC-based three-factor multiserver authentication scheme. Secur. Commun. Netw. 20(21): 1–14
**e X, Fang Y, Jian Z, Lu Y, Li T and Wan G 2020 Blockchain-driven anomaly detection framework on edge intelligence. CCF Trans. Network. 3: 171–192
Xu J, Xue K, Li S, Tian H, Hong J, Hong P and Yu N 2019 Healthchain: a blockchain-based privacy preserving scheme for large-scale health data. IEEE Internet of Things J. 6(5): 8770–8781
Yaeger K, Martini M, Rasouli J and Costa A 2019 Emerging blockchain technology solutions for modern healthcare infrastructure. J. Sci. Innov. Med. 2(1)
Yassein H R, Abidalzahra A A and Al-Saidi N M 2021 A new design of NTRU encryption with high security and performance level. In: AIP Conference Proceedings, Vol. 2334, No. 1, AIP Publishing LLC, p. 080005
Zhou T, Shen J, He D, Vijayakumar P and Kumar N 2020 Human-in-the-loop-aided privacy-preserving scheme for smart healthcare. IEEE Trans. Emerg. Top. Comput. Intell. 6(1): 6–15
Li W, ** C, Kumari S, **ong H and Kumar S 2022 Proxy re-encryption with equality test for secure data sharing in Internet of Things-based healthcare systems. Trans. Emerg. Telecommun. Technol. 33(10): e3986
Das S and Namasudra S 2022 A novel hybrid encryption method to secure healthcare data in IoT-enabled healthcare infrastructure. Comput. Electr. Eng. 101: 107991
Nagarajan S M, Deverajan G G, Kumaran U, Thirunavukkarasan M, Alshehri M D and Alkhalaf S 2021 Secure data transmission in internet of medical things using RES-256 algorithm. IEEE Trans. Ind. Inform. 18(12): 8876–8884
Almalawi A, Khan A I, Alsolami F, Abushark Y B and Alfakeeh A S 2023 Managing security of healthcare data for a modern healthcare system. Sensors 23(7): 3612
Raheja N and Manocha A K 2022 IoT based ECG monitoring system with encryption and authentication in secure data transmission for clinical health care approach. Biomed. Sign. Process. Control 74: 103481
Wu Y, Zhang L, Berretti S and Wan S 2022 Medical image encryption by content-aware DNA computing for secure healthcare. IEEE Trans. Ind. Inform. 19(2): 2089–2098
Karuppiah S V and Gurunathan G 2021 Secured storage and disease prediction of E-health data in cloud. J. Ambient Intell. Human. Comput. 12: 6295–6306
Boumezbeur I and Zarour K 2022 Improving privacy-preserving healthcare data sharing in a cloud environment using hybrid encryption. Acta Inform. Prag. 3: 361–379
Jiang H, Wang M, Zhao P, **ao Z and Dustdar S 2021 A utility-aware general framework with quantifiable privacy preservation for destination prediction in LBSs. IEEE/ACM Trans. Netw. 29(5): 2228–2241
Qiao F, Li Z and Kong Y 2023 A privacy-aware and incremental defense method against GAN-based poisoning attack. IEEE Trans. Comput. Soc. Syst.
Han S, Ding H, Zhao S, Ren S, Wang Z, Lin J, Zhou S 2023 Practical and robust federated learning with highly scalable regression training. IEEE Trans. Neural Networks Learn Syst.
Luan D, Liu A, Wang X, **e Y, Wu Z, Zhang W 2022 Robust two-stage location allocation for emergency temporary blood supply in postdisaster. Discrete Dyn. Nat. Soc.
Song Y, **n R, Chen P, Zhang R, Chen J, Zhao Z 2023 Identifying performance anomalies in fluctuating cloud environments: A robust correlative-GNN-based explainable approach. Future Gener. Comput. Syst. 145: 77–86
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Suganthi, P., Kavitha, R. Secure and privacy in healthcare data using quaternion based neural network and encoder-elliptic curve deep neural network with blockchain on the cloud environment. Sādhanā 48, 206 (2023). https://doi.org/10.1007/s12046-023-02249-2
Received:
Revised:
Accepted:
Published:
DOI: https://doi.org/10.1007/s12046-023-02249-2