Abstract
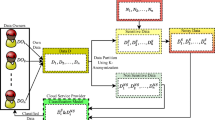
By applying novel way of cloud computing, the computing resources and services are delivered. That can raise the benefit health care research, and alter the face of health information technology. The E-health applications have capable to process the trivial and non-trivial connections among the different sensor signals and big data, better conception of diseases. Cloud computing are controls better advantages but it has also control main security challenges. To raise the data security in cloud computing the two fish encryption algorithm was suggested by us. At first the sensitive data’s are separated into the multiples of data by applying Multi kernel support vector machine (MKSVM) classification algorithm in our article. By applying optimal two fish encryption algorithm, and second the segmented sensitive data are encrypted. Then the encrypted data are saved in the cloud service provider. After the encryption process, the user must be chosen an optimal key. The optimal key will be inquired by the cloud server. For that, we are also suggested an optimization algorithm called as Modified whale optimization algorithm (MWO). After all the verification process only the user found the data from the cloud server. This will increase the security of data cloud computing environment. The performance of our suggested method is computed in terms of accuracy, time and memory utilization. The introduced method is implemented in Cloud sim with JAVA. Our techniques and algorithms are outperforms equated with existing methods.










Similar content being viewed by others
Change history
07 June 2022
This article has been retracted. Please see the Retraction Notice for more detail: https://doi.org/10.1007/s12652-022-04036-z
References
Ajesh F, Ravi R, Rajakumar G (2020) Early diagnosis of glaucoma using multi-feature analysis and DBN based classification. J Ambient Intell Hum Comput
Aldeen YAAS, Salleh M, Aljeroudi Y (2016) An innovative privacy preserving technique for incremental datasets on cloud computing. J Biomed Informat 62:107–116
Ali O, Shrestha A, Soar J, Wamba SF (2018) Cloud computing-enabled healthcare opportunities, issues, and applications: a systematic review. Int J Inform Manag 43:146–158
An NT, Huynh CT, Lee B, Hong CS, Huh EN (2015) An efficient block classification for media healthcare service in mobile cloud computing. Multimed Tools Appl 74(14):5209–5223
Cavalcante E, Pereira J, Alves MP, Maia P, Moura R, Batista T, Delicato FC, Pires PF (2016) On the interplay of internet of things and cloud computing: a systematic map** study. Comput Commun 89:1–54
Chen X, Huang X, Jiao C, Flanner MG, Raeker T, Palen B (2016) Running climate model on a commercial cloud computing environment: a case study using community earth system model (CESM) on Amazon AWS. Comput Geosci 98:1–17
Deshmukh P (2017) Design of cloud security in the EHR for Indian healthcare services. J King Saud Univ-Comput Inform Sci 29(3):281–287
El-Gazzar R, Hustad E, Olsen DH (2016) Understanding cloud computing adoption issues: a Delphi study approach. J Syst Softw 118:64–84
Gupta PK, Maharaj BT, Malekian R (2017) A novel and secure IoT based cloud centric architecture to perform predictive analysis of users activities in sustainable health centres. Multimed Tools Appl 76(18):18489–18512
Ji X, Zeng F, Lin M (2016) Data transmission strategies for resource monitoring in cloud computing platforms. Optik 127(16):6726–6734
** Y, Liu Y, Si W (2020) Editorial for the special issue on Intelligent agent distributed signal processing for IoT. J Ambient Intell Hum Comput 11:447–449
Khan MA (2016) A survey of security issues for cloud computing. J Netw Comput Appl 71:11–29
Kumar PM, Lokesh S, Varatharajan R, Babu GC, Parthasarathy P (2018) Cloud and IoT based disease prediction and diagnosis system for healthcare using Fuzzy neural classifier. Future Gener Comput Syst 86:527–534
Kwon Y, Yi H, Kwon D, Yang S, Cho Y, Paek Y (2016) Precise execution offloading for applications with dynamic behavior in mobile cloud computing. Pervas Mob Comput 27:58–74
Masdari M, ValiKardan S, Shahi Z, Azar SI (2016) Towards workflow scheduling in cloud computing: a comprehensive analysis. J Netw Comput Appl 66:64–82
Odelu V, Das AK, Kumari S, Huang X, Wazid M (2016) Provably secure authenticated key agreement scheme for distributed mobile cloud computing services. Future Gener Comput Syst 68:74–88
Saikrishna PS, Pasumarthy R (2016) Multi-objective switching controller for cloud computing systems. Control Eng Pract 57:72–83
Shakil KA, Zareen FJ, Alam M, Jabin S (2017) BAMHealthCloud: a biometric authentication and data management system for healthcare data in cloud. J King Saud Univ-Comput Inform Sci 32:57–64
Sharma Y, Javadi B, Si W, Sun D (2016) Reliability and energy efficiency in cloud computing systems: survey and taxonomy. J Netw Comput Appl 74:1–54
Tian N, Zhang L, Li Z, Liu J, Lei G, Ma Y (2019) Big data of clinical manifestations combined with neuroelectrophysiologic features in the early diagnosis of motor neuron disease. J Ambient Intell Hum Comput 10:3879–3888
Wei J, Yi M, Song L (2016) Efficient integrity verification of replicated data in cloud computing system. Comput Secur 65:1–23
Yang X, Huang X, Liu JK (2016) Efficient handover authentication with user anonymity and untraceability for mobile cloud computing. Future Gener Comput Syst 62:190–195
Zhang J, Wang X, Huang H, Chen S (2016a) Clustering based virtual machines placement in distributed cloud computing. Future Gener Comput Syst, 1–21
Zhang J, Huang H, Wang X (2016b) Resource provision algorithms in cloud computing: a survey. J Netw Comput Appl 64:23–42
Zhang G, Kou L, Yuan Y, Sun J, Lin Y, Da Q, Wang W (2017) An intelligent method of cancer prediction based on mobile cloud computing. Clust Comput. https://doi.org/10.1007/s10586-017-1416-0
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
This article has been retracted. Please see the retraction notice for more detail:https://doi.org/10.1007/s12652-022-04036-z
About this article
Cite this article
Karuppiah, S.V., Gurunathan, G. RETRACTED ARTICLE: Secured storage and disease prediction of E-health data in cloud. J Ambient Intell Human Comput 12, 6295–6306 (2021). https://doi.org/10.1007/s12652-020-02205-6
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12652-020-02205-6