Search
Search Results
-
Robust Control for Interval Type-2 T-S Fuzzy Discrete Systems with Input Delays and Cyber Attacks
This paper focuses on the robust control issue for interval type-2 Takagi-Sugeno (IT2 T-S) fuzzy discrete systems with input delays and cyber...
-
Finite-Time Fuzzy Adaptive Output Feedback Resilient Control of Nonlinear Cyber-Physical Systems with Sensor Attacks and Actuator Faults
This paper studies the finite-time fuzzy adaptive output feedback resilient control problem for nonlinear cyber-physical systems (CPSs) with sensor...
-
Detection of Stealthy False Data Injection Attacks Against Cyber-Physical Systems: A Stochastic Coding Scheme
This paper, from the view of a defender, addresses the security problem of cyber-physical systems (CPSs) subject to stealthy false data injection...
-
Optimal Resource Allocation and Feasible Hexagonal Topology for Cyber-Physical Systems
Networked cyber-physical systems are facing serious security threats from malicious attacks. It is noted that the networked cyber-physical system...
-
Is accumulation risk in cyber methodically underestimated?
Many insurers have started to underwrite cyber in recent years. In parallel, they developed their first actuarial models to cope with this new type...

-
A Bonus-Malus framework for cyber risk insurance and optimal cybersecurity provisioning
The cyber risk insurance market is at a nascent stage of its development, even as the magnitude of cyber losses is significant and the rate of cyber...

-
Modeling and pricing cyber insurance
The paper provides a comprehensive overview of modeling and pricing cyber insurance and includes clear and easily understandable explanations of the...

-
Constrained optimization based adversarial example generation for transfer attacks in network intrusion detection systems
Deep learning has enabled network intrusion detection rates as high as 99.9% for malicious network packets without requiring feature engineering....

-
A Reputation Game on Cyber-Security and Cyber-Risk Calibration
To analyze strategic interactions arising in the cyber-security context, we develop a new reputation game model in which an attacker can pretend to...

-
Whittle’s Index Based Sensor Scheduling for Multiprocess Systems Under DoS Attacks
In this paper, the authors consider how to design defensive countermeasures against DoS attacks for remote state estimation of multiprocess systems....
-
Algebraic-Differential Attacks on a Family of Arithmetization-Oriented Symmetric Ciphers
Motivated by applications in advanced cryptographic protocols, research on arithmetization-oriented symmetric primitives has been rising in the field...
-
Polynomial-Time Key-Recovery Attacks Against NTRUReEncrypt from ASIACCS’15
In ASIACCS 2015, Nuñez, et al. proposed a proxy re-encryption scheme, named NTRUReEncrypt, based on NTRU, which allows a proxy to translate...
-
Diagnosability and attack detection for discrete event systems under sensor attacks
This paper extends the theory of diagnosability by investigating fault diagnosis in discrete event systems under sensor attacks using finite-state...

-
H∞/Passive Synchronization of Semi-Markov Jump Neural Networks Subject to Hybrid Attacks via an Activation Function Division Approach
In this work, an H ∞ /passive-based secure synchronization control problem is investigated for continuous-time semi-Markov neural networks subject to...
-
A comprehensive model for cyber risk based on marked point processes and its application to insurance
After scrutinizing technical, legal, financial, and actuarial aspects of cyber risk, a new approach for modelling cyber risk using marked point...
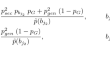
-
An Optimal Group Decision-Making Approach for Cyber Security Using Improved Selection-Drift Dynamics
In cyber security, balancing investment and risk has always been a dilemmatic problem since the threats often lurk in the shadows. Thus, timely and...

-
Reachable set estimation of multi-agent systems under packet losses and deception attacks
This paper considers the problem of estimating reachable set in leaderless consensus for multi-agent systems with Lipschitz nonlinear dynamics and...

-
Analysis of Stealthy False Data Injection Attacks Against Networked Control Systems: Three Case Studies
This paper mainly investigates the security problem of a networked control system based on a Kalman filter. A false data injection attack scheme is...
-
Secure synchronization and identification for fractional complex networks with multiple weight couplings under DoS attacks
This paper is concerned with the secure synchronization and topology identification for fractional complex networks (FCNs) with multiple weight...

-
The critical node game
In this work, we introduce a game-theoretic model that assesses the cyber-security risk of cloud networks and informs security experts on the optimal...

