Search
Search Results
-
Exploring the feasibility of adversarial attacks on medical image segmentation
Recent advancements in Deep Learning (DL) based medical image segmentation models have led to tremendous growth in healthcare applications. However,...

-
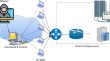
Leveraging blockchain and machine learning to counter DDoS attacks over IoT network
The paper presents an approach for detecting Distributed Denial of Service (DDoS) attacks using machine learning and blockchain technology. With the...
-
Defense against adversarial attacks via textual embeddings based on semantic associative field
Deep neural networks are known to be vulnerable to various types of adversarial attacks, especially word-level attacks, in the field of natural...

-
Adversarial Attacks on Visual Objects Using the Fast Gradient Sign Method
Adversarial attacks exploit vulnerabilities or weaknesses in the model’s decision-making process to generate inputs that appear benign to humans but...
-
Securing multi-chain consensus against diverse miner behavior attacks in blockchain networks
As cross-chain technologies enable interactions among different blockchains (hereinafter “chains”), multi-chain consensus is becoming increasingly...
-
Study of smart grid cyber-security, examining architectures, communication networks, cyber-attacks, countermeasure techniques, and challenges
Smart Grid (SG) technology utilizes advanced network communication and monitoring technologies to manage and regulate electricity generation and...

-
Optimizing Rectangle and Boomerang Attacks: A Unified and Generic Framework for Key Recovery
The rectangle attack has shown to be a very powerful form of cryptanalysis against block ciphers. Given a rectangle distinguisher, one expects to...

-
Towards Unified Defense for Face Forgery and Spoofing Attacks via Dual Space Reconstruction Learning
Real-world face recognition systems are vulnerable to diverse face attacks, ranging from digitally manipulated artifacts to physically crafted...

-
Detection of non-periodic low-rate denial of service attacks in software defined networks using machine learning
In this paper, we propose a novel approach to detect non-periodic Low-rate Denial of Service attacks in Software Defined Networks using Machine...

-
Deep learning techniques to detect cybersecurity attacks: a systematic map** study
ContextRecent years have seen a lot of attention into Deep Learning (DL) techniques used to detect cybersecurity attacks. DL techniques can swiftly...

-
WFSS: weighted fusion of spectral transformer and spatial self-attention for robust hyperspectral image classification against adversarial attacks
The emergence of adversarial examples poses a significant challenge to hyperspectral image (HSI) classification, as they can attack deep neural...

-
Deep learning adversarial attacks and defenses on license plate recognition system
The breakthroughs in Machine learning and deep neural networks have revolutionized the handling of critical practical challenges, achieving...

-
Blockchain-based security framework for mitigating network attacks in multi-SDN controller environment
In the evolving landscape of network management, multi-Software Defined Networking (SDN) controller environments represent a paradigm shift toward...

-
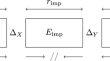
Quantum impossible differential attacks: applications to AES and SKINNY
In this paper we propose the first efficient quantum version of key-recovery attacks on block ciphers based on impossible differentials, which was...
-
B-CAT: a model for detecting botnet attacks using deep attack behavior analysis on network traffic flows
Threats on computer networks have been increasing rapidly, and irresponsible parties are always trying to exploit vulnerabilities in the network to...

-
Meet-in-the-middle attacks on AES with value constraints
In meet-in-the-middle (MITM) attacks, the sizes of the precomputation tables determine the effectiveness. In this paper, value constraints are...

-
A Geth-based real-time detection system for sandwich attacks in Ethereum
With the rapid development of the Ethereum ecosystem and the increasing applications of decentralized finance (DeFi), the security research of smart...

-
Enhancing non-profiled side-channel attacks by time-frequency analysis
Side-channel analysis (SCA) has become an increasing important method to assess the physical security of cryptographic systems. In the process of...

-
A Cost Optimized Solution for Defending Against DDoS Attacks: An Analysis of a Multi-layered Architecture
Distributed denial-of-service (DDoS) attacks have grown to be a major concern for businesses and individuals who use the internet for operations and...

-
Detecting SQL injection attacks by binary gray wolf optimizer and machine learning algorithms
SQL injection is one of the important security issues in web applications because it allows an attacker to interact with the application's database....

