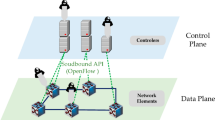
Abstract
In this paper, we propose a novel approach to detect non-periodic Low-rate Denial of Service attacks in Software Defined Networks using Machine Learning algorithms. Low-rate Denial of Service attacks are a type of cyber-attack that aim to disrupt network services by sending low-rate traffic to the target system. These attacks can be difficult to detect as they do not exhibit the same characteristics as traditional high-rate Denial of Service attacks. However, despite their low-rate nature, Low-rate Denial of Service attacks can still have significant harmful effects on network performance and availability. Our approach leverages the flexibility and programmability of Software Defined Networks to collect network traffic data and apply Machine Learning algorithms to detect non-periodic Low-rate Denial of Service attacks in real-time. We evaluate our approach using a simulated Software Defined Networks environment and demonstrate its effectiveness in accurately detecting non-periodic Low-rate Denial of Service attacks.
















Similar content being viewed by others
Data availability
N/A.
References
Rios VDM, Inacio PR, Magoni D, Freire MM (2022) Detection and mitigation of Low-Rate Denial-of-Service attacks: A survey. IEEE Access 10:76648–76668. https://doi.org/10.1109/ACCESS.2022.3191430
Hussein A, Chadad L, Adalian N, Chehab A, Elhajj IH, Kayssi A (2020) Software-Defined Networking (SDN): The security review. J Cyber Secur Technol 4(1):1–66. https://doi.org/10.1080/23742917.2019.1629529
Sarker IH, Kayes A, Badsha S, Alqahtani H, Watters P, Ng A (2020) Cybersecurity data science: An overview from machine learning perspective. J Big data 7:1–29. https://doi.org/10.1186/s40537-020-00318-5
Vedula V, Lama P, Boppana RV, Trejo LA (2021) On the detection of low-rate denial of service attacks at transport and application layers. Electronics 10(17):2105. https://doi.org/10.3390/electronics10172105
Biswas P, Samanta T (2021) Anomaly detection using ensemble random forest in wireless sensor network. Int J Inf Technol 13(5):2043–2052. https://doi.org/10.1007/s41870-021-00717-8
Yue M, Wang H, Liu L, Wu Z (2020) Detecting DoS attacks based on multi-features in SDN. IEEE Access 8:104688–104700. https://doi.org/10.1109/ACCESS.2020.2999668
Bhasin V, Kumar S, Saxena PC, Katti CP (2020) Security architectures in wireless sensor network. Int J Inf Technol 12(1):261–272. https://doi.org/10.1007/s41870-018-0103-6
**e R, Xu M, Cao J, Li Q (2019) SoftGuard: Defend Against the Low-Rate TCP Attack in SDN. In: ICC 2019 - 2019 IEEE International Conference on Communications (ICC), Shanghai, China, pp 1–6. https://doi.org/10.1109/ICC.2019.8761806.
Rios VM, Inácio PRM, Magoni D, Freire MM (2021) Detection of reduction-of-quality DDoS attacks using Fuzzy Logic and machine learning algorithms. Comput Netw 186:107792. https://doi.org/10.1016/j.comnet.2020.107792
Yan Y, Tang D, Zhan S, Dai R, Chen J, Zhu N (2019) Low-Rate DoS Attack Detection Based on Improved Logistic Regression. In: 2019 IEEE 21st International Conference on High Performance Computing and Communications; IEEE 17th International Conference on Smart City; IEEE 5th International Conference on Data Science and Systems (HPCC/SmartCity/DSS), Zhangjiajie, China, pp 468–476. https://doi.org/10.1109/HPCC/SmartCity/DSS.2019.00076.
Tang D, Dai R, Tang L, Li X (2020) Low-rate DoS attack detection based on two-step cluster analysis and UTR analysis. Hum Cent Comput Inf Sci 10(1):6. https://doi.org/10.1186/s13673-020-0210-9
Tang D, Tang L, Dai R, Chen J, Li X, Rodrigues JJPC (2020) MF-Adaboost: LDoS attack detection based on multi-features and improved Adaboost. Futur Gener Comput Syst 106:347–359. https://doi.org/10.1016/j.future.2019.12.034
Tang D, Tang L, Shi W, Zhan S, Yang Q (2021) MF-CNN: a New Approach for LDoS Attack Detection Based on Multi-feature Fusion and CNN. Mobile Netw Appl 26(4):1705–1722. https://doi.org/10.1007/s11036-019-01506-1
Fowdur TP, Baulum BN, Beeharry Y (2020) Performance analysis of network traffic capture tools and machine learning algorithms for the classification of applications, states and anomalies. Int J Inf Technol 12(3):805–824. https://doi.org/10.1007/s41870-020-00458-0
Zhijun W, Wen**g L, Liang L, Meng Y (2020) Low-rate DoS attacks, detection, defense, and challenges: a survey. IEEE Access 8:43920–43943. https://doi.org/10.1109/ACCESS.2020.2976609
Chen Z, Yeo CK, Lee BS, Lau CT (2018) Power spectrum entropy based detection and mitigation of low-rate DoS attacks. Comput Netw 136:80–94. https://doi.org/10.1016/j.comnet.2018.02.029
Mininet (2023) http://mininet.org/ Accessed 04 July 2023
Ryu Controller (2020) https://ryu-sdn.org/ Accessed 04 July 2023
Nload (2023) https://github.com/rolandriegel/nload Accessed 04 July 2023
IPERF - The TCP, UDP and SCTP network bandwidth measurement tool (2023) https://iperf.fr/ Accessed 04 July 2023
Sarker IH (2022) Machine learning for intelligent data analysis and automation in cybersecurity: Current and future prospects. Ann Data Sci. https://doi.org/10.1007/s40745-022-00444-2
Cervantes J, Garcia-Lamont F, Rodríguez-Mazahua L, Lopez A (2020) A comprehensive survey on support vector machine classification: Applications, challenges and trends. Neurocomputing 408:189–215. https://doi.org/10.1016/j.neucom.2019.10.118
Maalouf M (2011) Logistic regression in data analysis: an overview. Int J Data Analysis Techniques Strategies 3(3):281–299. https://doi.org/10.1504/IJDATS.2011.041335
Zhang T, Ramakrishnan R, Livny M (1996) BIRCH: An efficient data clustering method for very large databases. ACM SIGMOD Rec 25(2):103–114
SVM SciKit Learn (2023) https://scikit-learn.org/stable/modules/svm.html Accessed 04 July 2023
Logistic Regression (2023) https://scikit-learn.org/stable/modules/generated/sklearn.linear_model.LogisticRegression.html Accessed 04 July 2023
BIRCH (2023) https://scikit-learn.org/stable/modules/generated/sklearn.cluster.Birch.html Accessed 04 July 2023
Guo L, Lee JY (2021) TCP-FLASH - A Fast Reacting TCP for Modern Networks. IEEE Access 9:68861–68879. https://doi.org/10.1109/ACCESS.2021.3077612
TcpDump (2023) https://www.tcpdump.org/ Accessed 04 July 2023
Fu Y, Duan X, Wang K, Li B (2022) Low-rate Denial of Service attack detection method based on time-frequency characteristics. J Cloud Comput 11(1):31. https://doi.org/10.1186/s13677-022-00308-3
Kebande VR, Karie NM, Ikuesan RA (2021) Real-time monitoring as a supplementary security component of vigilantism in modern network environments. Int J Inf Technol 13(1):5–17. https://doi.org/10.1007/s41870-020-00585-8
**n Y et al (2018) Machine Learning and Deep Learning Methods for Cybersecurity. IEEE Access 6:35365–35381. https://doi.org/10.1109/ACCESS.2018.2836950
Eshima N (2020) Statistical Data Analysis and Entropy. Behaviormetrics: Quantitative Approaches to Human Behavior, vol. 3. Springer Nature, Singapore. https://doi.org/10.1007/978-981-15-2552-0.
Illowsky B, Dean S (2018) Introductory statistics. OpenStax.
GridSearchCV (2023) https://scikit-learn.org/stable/modules/generated/sklearn.model_selection.GridSearchCV.html Accessed 04 July 2023
KFold (2023) https://scikit-learn.org/stable/modules/generated/sklearn.model_selection.KFold.html Accessed 04 July 2023
Singh P, Ranga V (2021) Attack and intrusion detection in cloud computing using an ensemble learning approach. Int J Inf Technol 13(2):565–571. https://doi.org/10.1007/s41870-020-00583-w
Alqahtani H, Sarker IH, Kalim A, Minhaz Hossain SM, Ikhlaq S, Hossain S. Cyber intrusion detection using machine learning classification techniques. In: Springer. 2020:121–131. https://doi.org/10.1007/978-981-15-6648-6_10
Sakhai M, Wielgosz M (2021) Modern cybersecurity solution using supervised machine learning. ar**v preprint ar**v:2109.07593.
Zhan S, Tang D, Man J, Dai R, Wang X (2019) Low-Rate DoS Attacks Detection Based on MAF-ADM. Sensors 20(1):189. https://doi.org/10.3390/s20010189
Liu L, Wang H, Wu Z, Yue M (2020) The detection method of low-rate DoS attack based on multi-feature fusion. Digital Commun Netw 6(4):504–513. https://doi.org/10.1016/j.dcan.2020.04.002
Zhang D, Tang D, Tang L, Dai R, Chen J, Zhu N (2019) PCA-SVM-Based Approach of Detecting Low-Rate DoS Attack. In: 2019 IEEE 21st International Conference on High Performance Computing and Communications; IEEE 17th International Conference on Smart City; IEEE 5th International Conference on Data Science and Systems (HPCC/SmartCity/DSS). Zhangjiajie, China, pp 1163–1170. https://doi.org/10.1109/HPCC/SmartCity/DSS.2019.00164
Funding
No funding was received for conducting this study.
Author information
Authors and Affiliations
Contributions
All authors contributed to the study conceptualization, design and methodology. Material preparation, analysis and writing the original draft were performed by DY, BM and MS; the resources preparation and visualization was made by BM and PP. All authors reviewed and edited the final manuscript. All authors have read and agreed to the published version of the manuscript.
Corresponding author
Ethics declarations
Conflict of interest
The authors have no competing interests to declare that are relevant to the content of this article.
Ethical approval
N/A.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Yousef, D., Maala, B., Skvortsova, M. et al. Detection of non-periodic low-rate denial of service attacks in software defined networks using machine learning. Int. j. inf. tecnol. 16, 2161–2175 (2024). https://doi.org/10.1007/s41870-023-01634-8
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s41870-023-01634-8