Abstract
Watermarking has been considered to be a potent and persuasive gizmo for its application in healthcare setups that work online, especially in the current COVID-19 scenario. The security and protection of medical image data from various manipulations that take place over the internet is a topic of concern that needs to be addressed. A detailed review of security and privacy protection using watermarking has been presented in this paper. Watermarking of medical images helps in the protection of image content, authentication of Electronic Patient Record (EPR), and integrity verification. At first, we discuss the various prerequisites of medical image watermarking systems, followed by the classification of Medical Image Watermarking Techniques (MIWT) that include state-of-the-art. We have classified MIWT’s into four broader classes for providing better understanding of medical image watermarking. The existing schemes have been presented along with their cons so that the reader may be able to grasp the shortcomings of the technique in order to develop novel techniques proving the inevitability of the presented review. Further, various evaluation parameters along with potential challenges pertaining to medical image watermarking systems have been discussed to provide a deep insight into this research area.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
The emergence of modern technologies including IoT, IoMT, cloud computing, telemedicine, and other secluded health setups have overtaken conventional healthcare. Sharing of digital medical images over the cloud or internet is taking place in huge amounts resulting in increased active and passive attacks on this data. Manipulation, snoo**, deletion, copying, and other unauthorized access to medical data have increased by a huge amount [7, 8, 59, 60, 83, 88, 96]. The variation in medical image data along with the patient’s confidential data may lead to adverse effects. Yet there is an alarming increase in patient information-related thefts, even though it has been enlisted among the severe crimes. This has led the attention of various researchers towards enhancing the security of medical images. Various techniques have been developed for the secure communication of medical images along with the data being hidden within these images [19, 25, 49]. The main aim is that no person other than the two parties should be able to extricate the confidential message from the image. For such a purpose various data-hiding approaches like steganography, cryptography, fingerprinting, and digital watermarking have been proposed [8, 19, 20, 25, 49, 59] have presented an analysis of various medical image watermarking techniques to evaluate the robustness and precincts of these techniques. Thabit [84] has presented a review of medical image watermarking techniques specifically pertaining to authenticity verification. The review papers cited above and in Table 2 have not classified the Medical Image Watermarking Techniques in a broader spectrum and have just chosen to remain specific to a particular application. In this review, we have classified the medical image watermarking techniques into four broader classes and have provided the shortcoming of the literature for the readers to propose novel techniques by overcoming the potential challenges incurred in the already existing schemes. The earlier existing papers presenting the review of medical image watermarking techniques have not considered authentication, integration, and verification, although it is an important domain of medical image watermarking. Therefore there is a need for the updated review paper so as to fill the gap and shortage in the already existing literature. This will help the readers to quickly grasp the idea of existing literature and the shortcomings that need to be worked on for making the remote and online healthcare system more secure, convenient, and most importantly reliable.
The rest of the paper is organized as follows. Section 2 presents the prerequisites for medical image watermarking techniques followed by the general framework of digital image watermarking in Section 3. Section 4 presents applications of medical image watermarking techniques while Section 5 presents watermarking techniques for medical images. Section 6 gives the classification of medical image watermarking techniques based on domains. Further, Sections 7 and 8 present the State of the art watermarking techniques for medical images and assessment of watermarked medical images respectively. Section 9 presents the potential issues and challenges while the paper concludes in section 10.
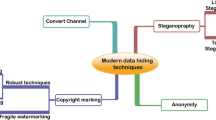
2 Prerequisites for Medical Image Watermarking Techniques
There are several prerequisites for medical image watermarking. These have been depicted in Fig. 1.
2.1 Image fidelity
It is a parameter that is used for the calculation of similarity between the original medical image and watermarked medical image [20, 88, 95]. The watermark should be embedded in the host medical image in a way that it (watermark) is not perceptible to the Human Visual System (HVS) and maintains the quality of the host image. This indicates that HVS should be unable to distinguish between the watermarked medical image and the original medical image. Image fidelity is one of the major properties a watermarking system should have, especially for medical image watermarking systems, where the slightest variation may cause the wrong diagnosis. Therefore, medical image watermarking systems should tend to keep the perceptivity as high as possible.
2.2 Image robustness
Robustness is the ability of the medical image watermarking system to withstand various signal processing and geometric attacks [89]. Since these images are susceptible to attacks including intentional as well as unintentional attacks, there is a requirement to check the robustness of the watermark against these attacks. Even though all medical image watermarking techniques need not be robust, some may be fragile. Fragile watermarks are those that neither resists intentional nor intentional attacks.
2.3 Image payload
It is the amount of data bits that can be obscured within the medical image without affecting/ degrading its quality. The payload can be embedded either to secure the image using a watermark or to send the message along with the image while maintaining its perceptual quality [9].
2.4 Image security
The medical image watermarking algorithm is said to be secure if the intruder is not able to extract the information embedded within the image [1]. Security of medical image is of prime importance due to the presence of crucial data including patient information, insurance information, and health-related information. This is usually obtained by the use of encryption keys with large key space while embedding and extracting the medical image watermark.
2.5 Watermark invisibility
Imperceptivity or watermark invisibility is the measure of similarity between the cover medical image (CMI) and the Watermarked Medical Image (WMI). It is the measure for the level of invisibility of the watermark in WMI and can be calculated as Peak Signal to Noise Ratio (PSNR) and Structural Similarity Index Metric (SSIM) [50, 88].
2.6 Reversibility
The reversibility is of paramount importance in the case of medical images since the slightest variation in medical image data may cause misdiagnosis leading to life-threatening consequences. Even after embedding the watermark or hiding data within the image, we can reconstruct the original image if the method is reversible. Although the watermarked image is not distortionless, the recovered image is distortion-free [26, 69].
2.7 Computational complexity
The complexity of the algorithm is determined by the time taken for its execution i.e., the time required for embedding and extraction of medical images. Medical image watermarking algorithms being mostly real-time, need to be efficient and computationally less complex [25].
2.8 Reliability
The MIWT needs to maintain the integrity, confidentiality, and authenticity of the data. This factor helps in gaining the trustworthiness of the patients over the electronic healthcare setup. Integrity ensures that the medical image data has not been manipulated or modified. Confidentiality ensures that only the authorized person has the access to the medical image data while authenticity ensures that the received medical image data is correct and authentic [57].
Further, we present the evaluation parameters and applications of various prerequisites in tabular form (Table 3).
3 The general framework for digital image watermarking system
Digital watermarking is the method for hiding data in digital media. The watermark is hidden imperceptibly such that it can be used later for the identification and validation of data.
3.1 Basic elements of watermarking approaches
There are three basic components included in various watermarking approaches and these include:
-
a)
Generation of watermark
The watermark generation may vary for different applications according to specified properties and preferred objectives. Figure 2 depicts the process of generation of watermarking.
-
b)
Hiding of watermark
Once the watermark is generated, it is hidden within the image to generate the watermarked image using a data hiding key. Figure 3 depicts the process of hiding the watermark.
-
iii)
Extraction of watermark
At the receiver end, the process of extraction is done by performing a reverse information-hiding algorithm along with the use of the key. Figure 4 depicts the process of extraction of the watermark.
3.2 Basic components of medical image watermarking system
Section 3.1 described the general components of watermarking system. In this section, we introduce various other components required for MIWT. Figure 5 shows the components of medical image watermarking systems. These include:
-
a)
Generation of the medical image
Various methods including Computed Tomography Scan (CT), X-Rays, Magnetic Resonance Imaging (MRI), and other modalities have been developed in order to deliver better healthcare services to patients. It has helped doctors in proper diagnosis and hence is most commonly used. Medical images are collected according to the requirements of the patient. Once these images are generated, they can be used for diagnosis [12].
-
b)
Storage of medical image
After the generation of medical images, there is a need to store these medical images [64].
-
iii)
Data embedding and generation of authentication information
The EHI simultaneously with the authentication data is embedded within the medical image. After embedding this data in the medical image, we obtain a watermarked medical image that can be used for authentication prior to diagnosis [25].
-
iv)
Communication networks
The watermarked medical image is sent over an insecure communication network for remote doctor’s advice or a second opinion.
-
e)
Receipt of medical image
The medical image sent over communication networks is received via different devices including personal computers, smartphones, etc.
-
f)
Data extraction and verification of authenticity
On reception of the medical image, the data including patient information and authentication bits need to be extracted to verify the authenticity of the medical image. This is an important part of MIWT since unverified images may lead to wrong diagnosis and loss of patient information [25].
-
g)
Sharing for diagnosis
On verification of the medical image, it is shared with the doctor for diagnosis and required treatment.
4 Applications of MIWT’s
For safeguarding and securing medical images against various malicious attacks, watermarking plays an important role. The various applications of MIWT’s include:
-
a)
Providence of EHR
The EHR’s are embedded within the medical images for protecting their confidentiality. In region-based methods, this confidential information is embedded in Non-Region of Interest (NROI) in order to save the Region of Interest (ROI) from any degradation.
-
b)
Providence of medical prescription
Medical professionals these days tend to store and share medical prescriptions. These electronic prescriptions can be shared with other remote doctors for their opinion. It has made electronic healthcare cost-effective and easily accessible.
-
iii)
Providence of sensitive data
MIWT’s tend to secure patient information like insurance information, patient identity, patient payment information, etc. this information needs to be protected and secured since privacy, confidentiality, and trustworthiness are main necessities for MIWT’s.
-
iv)
Providence of medical image
An enormous amount of medical image data is generated in healthcare centers due to the gaining speed of electronic healthcare setups. This data is sent over the insecure channels for remote diagnosis and further monitoring of the patient. Various image modalities include CT scans, MRIs, ultrasonography, echocardiography, radiography, and functional MRI. The MIWT’s should be designed in a way that should conceal the information with nominal distortion.
5 Watermarking techniques for medical images
Watermarking is considered to be the best solution for protecting EPR’s containing sensitive patient information while the transmission of medical images [4, 16, 18, 21, 36, 38]. The fact that transmission over insecure channels leads to the stealing of biomedical images, has become a substantial concern for various researchers. This data is usually at risk of being manipulated intentionally or unintentionally. Further, the data can undergo various malicious attacks that may cause a loss of trustworthiness in the newly developed medical image communication system. Watermarking has been considered to be the best solution for the authentication and protection of medical images and EPR’s containing sensitive patient information while transmitting insecure channels.
Medical image authentication can be performed using the following two methods (Fig. 6).
5.1 Image-based watermark embedding
A logo or a watermark containing patient information is used for the validation of medical images [25]. This image can be encrypted prior to data embedding so that it cannot be decrypted other than a person who has the decryption keys.
The process of image-based watermarking is shown in Fig. 7.
5.2 Self-generated watermark embedding
For authentication of medical images, a watermark required to authenticate the medical image data is generated from the image itself [70, 82]. This makes the watermarking algorithm dynamic in nature since the watermark is different for different images. The watermark can also be encrypted and embedded using a security key to obtain the watermarked image. The process of self-generated watermark embedding is shown in Fig. 8.
The watermarking techniques for image authentication can be either block-based [11, 25] or pixel-based [94, 97]. Pixel-based algorithms show higher accuracy because of the fact that in the block-based method, the presence of even a single altered pixel in the block leads to the declaration of the whole block as invalid. The authentication watermark can be further utilized for tamper detection, localization, and recovery (Fig. 9).
Over years, various medical image authentication techniques have been presented [6, 10, 66, 76, 96] with different motives including tamper detection, tamper localization, and tamper recovery [22, 75]. The techniques developed for watermarking medical images should take image quality as a priority because distortion in these images can be fatal. These techniques should be computationally efficient as they have real-time applications. Watermarking techniques for Medical Image Authentication (WTMIA) are either region-based [46] or whole image based [25]. In the region-based method, there is the division of the medical image into ROI and NROI [69]. ROI contains the major portion of concern for diagnosis and hence needs to be accurate. For such a purpose, many watermarking techniques do not consider ROI for watermarking or data hiding. Also, many reversible data-hiding techniques have been developed for embedding watermark in ROI. The reversible watermarking techniques have the ability to reconstruct the lossless image at the receiver making it an efficient method for medical image watermarking.
For various WTMIA, there is always a trade-off. On increasing the data (i.e., detecting, localizing, and recovering the tamper), there will be a decrease in perceptual quality. In such a case, region-based watermarking plays a significant role wherein tamper detection, localization, and recovery of ROI is a priority. This decreases the number of bits being embedded within the image there are some cases the whole image is important for diagnosis by a remote doctor.
6 Classification of MIWT’s based on domains
The MIWT’s can be classified into two groups based on domain. These are discussed in the following subsections.
6.1 Spatial domain techniques
The spatial domain techniques for MIW modify the pixel intensity values of the medical image directly [57]. These techniques are computationally efficient, simple, and provide a higher payload. Spatial domain techniques provide the above-mentioned advantages but at the same time have several disadvantages. These techniques do not survive certain attacks. Also, the discovery of the watermarking techniques used for embedding can easily give access to the unauthorized user to obtain and alter the embedded watermark. Figure 10 a shows the general flow diagram for spatial domain watermark embedding and Fig. 10 b shows watermark extraction.
-
a)
Least Significant Bit Substitution (LSB)
It is one the oldest and yet simple methods for watermarking in the spatial domain. It is done by embedding the watermark in LSB [74]. The watermark is encoded before embedding. To embed the encoded bits, the pixel values are converted to the binary form and the rightmost bit of every pixel is replaced by the encoded watermark bits. After the replacement of LSB, the binary value image pixel is converted back to the decimal value image pixel. This has been illustrated in Fig. 11 a. Further, the flow graph for LSB substitution has been shown in Fig. 11 b.
-
b)
Modification of image histogram
Histogram modification is another spatial domain technique that has been used for data hiding in the medical image [69]. This scheme makes use of peak bins to embed data in a histogram. This method is easy to implement, yet its embedding capacity is restricted to a number of maximum or peak points that are available.
-
iii)
Local Binary Patterns
LBT is the spatial domain technique that makes use of the difference value between the central pixel and other pixels. It segments the image into non-overlap** blocks before calculating the differences. Then, embedding is done in these pixels according to the rules given in [91].
6.2 Transform domain techniques
Transform domain techniques generate the transform coefficients once they are applied to medical images. These coefficients are used for embedding the data. The most commonly used transform domain techniques include Discrete Fourier Transform (DFT), Discrete Cosine Transform (DCT), and Discrete Wavelet Transform (DFW). The general flow graph for data embedding and extraction in the transform domain is presented in Fig. 12 a and 12 b respectively. At first, the image is transformed using a specific transformation. Then embedding is carried in the coefficients of the transform domain. The embedded data can be the authentication data or a logo required for verification of the medical image. After embedding the data, the image is transformed back to its original form for obtaining the watermarked image. At the receiver, extraction of the embedded data along with the generation of authentication data is carried out to validate the image. If the generated data is similar to that of embedded data, then the algorithm is terminated and the image is considered to be valid else tamper detection, localization, and recovery are carried out to obtain the tamper-corrected image.
These transform domain techniques have been discussed as under:
-
a)
Discrete Fourier Transform
It is the most approachable technique for the conversion of medical image from the spatial domain to the transform domain [76]. It decomposes the Medical image into sine and cosine forms. It has the ability to provide resistance against various geometrical attacks. Let ft(k, l) represent the image with dimensions P×Q, k = 0, 1, 2, …, (P-1) and l = 0, 1, 2, …, (Q-1). The DFT and Inverse DFT (IDFT) can be calculated using the following formulas
And
Here FT(u, v) is DFT coefficient with u = 0, 1, 2, …, P-1 and v = 0, 1, 2, …, Q-1. DFT composes the image into amplitude part and Phase part. The amplitude part is used for watermark embedding since it contains a lesser amount of information in it and helps in the reduction of image distortion.
-
b)
Discrete Cosine Transform
DCT provides an attractive and efficient image transformation that maps linearly and the n-dimensional vector to n number of coefficients. It divides the image into three different frequency components: Low-Frequency Component (LFC), Middle-Frequency Component (MFC), and High-Frequency Component (HFC). The highest amount of energy is compressed LFC [73]. DCT has higher robustness towards JPEG compression but shows a lag in resistance toward the geometric attacks including crop**, rotation, scaling, etc. the DCT and its inverse have been shown in the following equations.
And
Here p and q are the block size and fT(x, y) represents the original image pixel, CT(u, v) is the transform domain coefficient and β(u) and β(v) is calculated as
-
iii)
Discrete Wavelet Transform
DWT is the most efficient and commonly used transform domain technique. Due to the multi-resolution properties, it provides accurate spatial localization. It decomposes the image into four sub-bands including Low Low (LL), Low High (LH), High Low (HL), and High High (HH) as shown in Fig. 13. LL sub-band contains the most significant information regarding the image details while other sub-bands contain the detail that is missed in LL sub-band. Further, DWT offers the decomposition of LL sub-band hierarchically [13, 86]. The energy in the case of DWT is calculated using the following equations.
Here N represents the number of levels considered for decomposition, PN and QN represent image dimensions and IC gives the coefficients of the current sub-bands.
Further, we present the pros and cons of the spatial domain and transform domain techniques for the readers to get better discernment for choosing the domain of watermarking according to their requirements (Table 4).
7 State of the Art watermarking techniques for medical image
7.1 Classical watermarking techniques for medical images
Classical watermarking or conventional watermarking takes whole image into consideration for watermarking. In medical images, distortion is not feasible and no radiologist may accept a distorted image for diagnosis. It may lead to wrong diagnosis leading to an increase in research pertaining to reversible data hiding (RDH). RDH has the capability to restore the original image from the image in which data is hidden. Figure 14 a shows the classical approach for embedding data while Fig. 14 b shows the extraction process.
The state-of-the-art techniques along with evaluation parameters, pros, and cons of classical watermarking techniques for medical image watermarking have been presented in Table 5 [14, 25, 27, 33, 47, 48, 56, 66, 71, 86].
7.2 Reversible watermarking for medical images
Embedding data into an image may lead to distortion of the image when compared to the original image. This distortion may lead to the wrong diagnosis and may prove fatal for the patient’s health. For such a purpose, reversible data-hiding techniques have been developed. These techniques can reconstruct the original image along with the embedded data accurately. Figure 15 a shows the framework for data embedding in reversible watermarking techniques for medical images and Fig. 15 b shows the data extraction and reconstruction of the original image after the extraction of hidden data.
The state-of-the-art techniques along with evaluation parameters, pros, and cons of reversible watermarking techniques for medical image watermarking have been presented in Table 6 [24, 26, 29, 32, 34, 40, 43, 52, 53, 67, 92].
7.3 Region-based watermarking techniques for medical images
Medical images can be divided into two regions namely ROI and NROI. ROI contains the important region for diagnosis purpose while the region other than ROI mostly contains black background which has no significance for diagnosis [69]. Usually, ROI is not preferred for data hiding since it contains significant information and its distortion is not acceptable. There are several methods that use NROI for hiding data but these methods have certain shortcomings. In this method, the amount of data to be embedded is determined by the size of the NROI. Further, it does not protect ROI from various malicious attacks. Also, these methods can only be implemented if NROI is present. Figure 16 a and 16 b show the data embedding and extraction in the case of region-based methods.
The state-of-the-art techniques along with evaluation parameters, pros, and cons of the region-based watermarking techniques for medical image watermarking have been presented in Table 7 [2, 17, 35, 42, 45, 55, 62, 74, 77, 80].
7.4 Authentication-based watermarking techniques for medical images
Authentication of images is a part of watermarking schemes. The authentication watermarking techniques for medical images (AWTMI) can perform operations including Medical Image Tamper Detection (MITD), Medical Image Tamper Localization (MITL), Medical Image Tamper Recovery (MITR), and EHR embedding (Fig. 17). MITD can be done using a logo, generating the data using a hash function for ROI or whole image, the identity of patients or doctors, medical image features, etc.
MITL is usually done by generating the average of each block of the image, using a logo, etc. MITR can be ROI-based or whole image based. It is usually done by considering the image pixels directly. Recovery of images increases image payload due to the fact that recovery of the image requires more data. The data is either generated from the average of each block or by using compression methods. EHR contains information related to the patient including patient identity, medical prescription, insurance information, payment information, etc. these watermarks are embedded either in the spatial domain (pixel domain) or in the transform domain in a medical image [15, 25]. The two main processes included in the watermarking process are watermark embedding and extraction as discussed earlier. Depending on the applicability of watermarking, the process of embedding and extraction is carried out. If we require only the detection of tamper in medical images, once detected the algorithm is terminated else the algorithm goes on till it performs the function of localizing and recovering the tamper. Most of the MIAT applied in the spatial domain use LSB substitution, difference expansion, exclusive OR, or chaotic key for watermarking. Spatial domain techniques make use of DCT, DWT, and others. Further, the watermarking domain can be selected on the basis of the required application.
Figure 18 a and 18 b show the framework for data embedding and extraction in authentication-based watermarking schemes. The state-of-the-art techniques along with evaluation parameters, pros, and cons of authentication-based watermarking techniques for medical image watermarking have been presented in Table 8 [30, 41, 44, 51, 61, 63, 68, 79, 81, 85]. Further in Table 9 we present the comparative analysis of several existing schemes in terms of PSNR, SSIM, and computational complexity.
8 Evaluation parameters for MIWT’s
For the evaluation of MIWT, various metrics can be calculated in order to determine the degree of distortion of the watermarked image. Also, the extracted watermark can be tested for its accuracy.
8.1 Assessment of watermarked medical Images
Various parameters including Peak Signal to Noise Ratio (PSNR), Mean Square Error (MSE), and Structural Similarity Index Matrices (SSIM) can be calculated for the estimation of distortion among the original and watermarked image. For an image (O) of size P×Q and watermarked image OW, the above-mentioned parameters are calculated as under:
-
a)
Mean Square Error
MSE can be calculated among O and OW using the following equation [50].
-
b)
Structural Similarity Index Metrics
SSIM gives the measure of correspondence among the images O and OW. It can be calculated using an equation [90].
Here,
In the above equations, μO, μOW are local means, σ0, σ0W are standard deviations and σOOW is the cross-covariance between the two images O and OW. On default selection of exponents and E3, the equation is reframed as under
-
iii)
Peak Signal to Noise Ratio
PSNR is the measure of visual quality distortion among the two images O and OW. A high value of PSNR depicts higher visual similarity between the images [6]. PSNR is calculated using the following equation.
PSNR is determined in terms of decibels (dB)
A high PSNR value indicates better perceptual quality. A PSNR value of 100 dB indicates no distortion. PSNR value of above 40 dB is acceptable for medical images. SSIM close to 1 indicates better image similarity. BER value close to 0 indicates lesser distortion among the original and watermarked image.
8.2 Assessment of extracted watermarked
To verify the reliability of the extracted watermark, various parameters can be evaluated. Let ‘L’ be the embedded logo or watermark and L’ be the extracted watermark, following are the various metrics calculated for assessment of extracted watermark.
-
a)
Correlation coefficient (CR)
CR is used to analyze the correspondence between L and L’. Its value ranges from 0 to 1 and it is calculated using the following equation [31].
-
b)
Bit Error Rate (BER)
BER is the metric that gives the measure of wrongly extracted bits in binary sequence [28]. Lower BER depicts the efficiency of the embedding algorithm. BER is calculated as
-
iii)
Accuracy Rate (AR)
AR is metric that gives the measure of correctly extracted bits in a binary sequence [28]. The higher the value of AR, the better is the embedding algorithm. It can be calculated using the following equation.
8.3 Assessment of embedding capacity
Embedding capacity or payload refers to the total number of binary data that can be embedded in the medical image using a particular watermarking algorithm. The payload can be calculated using the following equation.
8.4 Assessment of False Positive and False Negative Rates
In authentication-based watermarking schemes, classification on the basis of erroneous detection of pixels as tampered or non-tampered is done. False Positive Rates give the number of pixels erroneously detected as non-tampered whereas False Negative Rates (FNR) give the number of pixels erroneously detected as tampered. Further, the Tamper Detection Rate (TDR) gives the proportion of pixels sensed as tampered to the overall tampered pixels.
9 Potential issues and challenges
Plenty of research has been carried out for watermarking in medical images. Various methods have been developed for the purpose of medical image authentication. Yet, there are potential issues and challenges that limit the practicality of health-related watermarking systems. This can be attributed to the fact that a trade-off always exists amid the necessities of watermarking systems (i.e., perceptivity, payload, security, robustness). It is not possible to accomplish these requirements altogether. For such a purpose, the medical image watermarking system should be able to attain a better trade-off among the above-given requirements. The potential issues and challenges of medical image watermarking techniques observed from the above-mentioned schemes have been summarized below
-
Medical image watermarking systems should attain better trade-offs among perceptivity, payload, and robustness.
-
These techniques have real-time applications, therefore should be computationally efficient.
-
Reversible data hiding is found to be an efficient technique in medical images, due to its ability to reconstruct the original cover at the receiver.
-
Compression techniques can be used for the enhancement of image payload while reducing storage requirements.
-
Several methods in medical image watermarking are able to detect tampered regions, but only a few are able to reconstruct these regions.
-
The time requirements for embedding/encryption, extracting/ decryption, and image reconstruction need to be considered because the process altogether should not be time-consuming.
-
For enhancing the security of medical images and EHI encryption algorithms can be used. However, there is a need to consider other parameters that depict the efficiency of the system.
-
On develo** the medical image watermarking system, it should be evaluated for its performance on various image processing and geometric attacks.
-
In ROI and NROI-based watermarking techniques, there is a possibility of the absence of NROI. Even if the NROI is present its size depicts the amount of data that can be hidden in the image.
-
To ensure reliability and perceptual quality, almost every method makes use of two benchmarks namely PSNR and SSIM. Yet, there is a need for considering clinically relevant information in order to provide an accurate diagnosis. Therefore, the addition of benchmarks that access the watermarking system clinically to enhance its relevance and credibility should be considered.
10 Conclusions
Medical image watermarking is taking a lead in the present world and has the latency to provide an appreciable solution for various applications of e-healthcare. The challenges do not only include confidentiality but also include the prevention of manipulations because of authorized or unauthorized users, so that trust may be built in the e-healthcare setups. Several medical image watermarking techniques have been developed in spatial and transform domains with a different applicability. This paper presents a compendious survey of various medical image watermarking techniques using classical methods, reversible data hiding, ROI-based watermarking, and authentication-based watermarking. Further, various prerequisites along with the general framework of medical image watermarking and its capabilities have been discussed. We have presented the critical review in tabular form for various notable medical image watermarking schemes. The aim of this survey is to help future researchers to propose medical image watermarking techniques that might address the potential issues and challenges in e-healthcare setups. Furthermore, these techniques can be collaborated with machine learning algorithms [5, 65, 78] for providing better security.
Data availability
Data can not be made available due to Intuition policy.
References
Abdullatif M, Zeki AM, Chebil J, Gunawan TS (2013) Properties of digital image watermarking, in: Signal Processing and its Applications (CSPA), 2013 IEEE 9th International Colloquium on, 235–240
Aherrahrou N, Tairi H (2015) PDE based scheme for multi-modal medical image watermarking. Biomed Eng Online 14:108. https://doi.org/10.1186/s12938-015-0101-x
Allaf AH, Kbir MA (2019) A Review of Digital Watermarking Applications for Medical Image Exchange Security, In: Ben Ahmed M, Boudhir A, Younes A (eds) Innovations in Smart Cities Applications Edition 2. SCA 2018. Lecture Notes in Intelligent Transportation and Infrastructure. Springer, Cham https://doi.org/10.1007/978-3-030-11196-0_40
Alshanbari HS (2020) Medical image watermarking for ownership & tamper detection, Multimed Tools Appl, 1–17, https://doi.org/10.1007/s11042-020-08814-9
Alsmirat MA, Jararweh Y, Al-Ayyoub M et al (2017) Accelerating compute intensive medical imaging segmentation algorithms using hybrid CPU-GPU implementations. Multimed Tools Appl 76:3537–3555. https://doi.org/10.1007/s11042-016-3884-2
Anand A, Singh AK (2020) An improved DWT-SVD domain watermarking for medical information security. Comput Commun 152:72–80
Aparna P, Kishore PVV (2018) An Efficient Medical Image Watermarking Technique in E-healthcare Application Using Hybridization of Compression and Cryptography Algorithm. J Intell Syst 27(1):115–133
Aparna P, Kishore PVV (2020) A Blind Medical Image Watermarking for Secure E-Healthcare Application Using Crypto-Watermarking System. J Intell Syst 29(1):1558–1575
Arya P, Tomar DS, Dubey D (2015) A review on different digital watermarking techniques, Int. J. Signal Process. Image Process Pattern Recognit 8:129–136
Ashima A, Kumar AS (2020) An improved DWT-SVD domain watermarking for medical information security. Comput Commun 15:272–280
Azeroual A, Afdel K (2017) Real-time image tamper localization based on fragile watermarking and faber-schauder wavelet. AEU-Int J Electron Commun 79:207–218
Bagheri MH et al (2017) Advances in medical imaging for the diagnosis and management of common genitourinary cancers. Urol Oncol Semin Orig Investig 35(7):473–491
Balasamy K, Suganyadevi S (2021) A fuzzy based ROI selection for encryption and watermarking in medical image using DWT and SVD. Multimed Tools Appl 80:7167–7186
Cedillo-Hernandez M, Cedillo-Hernandez A, Nakano-Miyatake M, Perez-Meana H (2020) Improving the management of medical imaging by using robust and secure dual watermarking, Biomed Signal Process Control, 56, https://doi.org/10.1016/j.bspc.2019.101695
Chaitanya K, Rao KG (2018) A novel approach to medical image watermarking for tamper detection and recovery of Region of Interest using block compression and checksum. Int J Eng Technol 7(4):2137–2148
Chauhan DS, Singh AK, Adarsh A, Kumar B, Saini JP (2019) Combining Mexican hat wavelet and spread spectrum for adaptive watermarking and its statistical detection using medical images. Multimed Tools Appl 78(10):12647–12661
Das S, Kundu MK (2013) Effective management of medical information through ROI lossless fragile image watermarking technique, Comput Methods Prog Biomed, 111(3)
Dixit A, Dixit R (2017) A Review on Digital Image Watermarking Techniques. Int J Image Signal Process 9(4):56–66
Edward JS, Ramu P, Ramakrishnan S (2014) Discrete wavelet transform and singular value decomposition based ECG steganography for secured patient information transmission. J Med Syst 38(10):132–140
Elhoseny M, Shankar K, Lakshmanaprabu SK, Maseleno A, Arunkumar N (2020) Hybrid optimization with cryptography encryption for medical image security in Internet of Things. Neural Comput & Applic 32:10979–10993
Fan TY, Chao HC, Chieu BC (2019) Lossless medical image watermarking method based on significant difference of cellular automata transform coefficient. Signal Process Image Commun 70:174–183
Gad Hiya TD, Roy AK, Mitra SK, Mall V (2017) Use of discrete wavelet transform method for detection and localization of tampering in a digital medical image, In: 2017 IEEE Region 10 Symposium(TENSYMP), 1–5. https://doi.org/10.1109/TENCONSpring.2017.8070082.
Ghazali NF, Manaf AA, Sulong G (2015) Review of watermarking techniques for medical images. Int J Appl Eng Res 10(2):4991–5003
Govind PVS, Judy MV (2021) A secure framework for remote diagnosis in health care: A high capacity reversible data hiding technique for medical images, Comput Electr Eng, 89
Gull S, Loan NA, Parah SA, Sheikh JA, Bhat G (2018) An efficient watermarking technique for tamper detection and localization of medical images. J Ambient Intell Humaniz Comput 11:1799–1808
Gull S, Parah SA, Muhammad K (2020) Reversible Data Hiding Exploiting Huffman Encoding with Dual Images for IoMT based Healthcare, J Comput Commun, https://doi.org/10.1016/j.comcom.2020.08.023
Gull S, Mansour RF, Aljehane NO, Parah SA (2021) A self-embedding technique for tamper detection and localization of medical images for smart-health. Multimed Tools Appl 80:29939–299654. https://doi.org/10.1007/s11042-021-11170-x
Heylen K, Dams T (2008) An image watermarking tutorial tool using Matlab, in: Proc. of SPIE, 1–12
Huang LC, TsengLY HMS (2013) A reversible data hiding method by histogram shifting in high quality medical images. J Syst Softw 86(3):716–727
Hussan M, Parah SA, Gull S et al (2021) Tamper Detection and Self-Recovery of Medical Imagery for Smart Health. Arab J Sci Eng 46:3465–3481. https://doi.org/10.1007/s13369-020-05135-9
Jabade VS, Gengaje DSR Literature review of wavelet based digital image watermarking techniques. Int J Comput Appl 31:28–35
Jafar IF, Darabkh KA, Al-Zubi RT, Saifan RR (2016) An efficient reversible data hiding algorithm using two steganographic images. Signal Process 128:98–109
Jana M, Jana B, Joardar S (2022) Local feature based self-embedding fragile watermarking scheme for tampered detection and recovery utilizing AMBTC with fuzzy logic. J King Saud Uni Comput Inf Sci 34(10):9822–9835. https://doi.org/10.1016/j.jksuci.2021.12.011
Kaw JA, Loan NA, Parah SA, Muhammad K, Sheikh JA, Bhat GM (2018) A reversible and secure patient information hiding system for IoT driven e-health. Int J Inf Manag 45:262–275
Khor HL, Liew SC, Zain JM (2017) Region of Interest-Based Tamper Detection and Lossless Recovery Watermarking Scheme (ROI-DR) on Ultrasound Medical Images. J Digit Imaging 30:328–349
Kishore RR (2020) A Novel and Efficient Blind Domain Image Watermarking In Transform Domain. Procedia Comput Sci 167:1505–1514
Kishore P, Rao MS, Prasad CR, Kumar DA (2016) Medical image watermarking run through review. J Eng Appl Sci 11(5):2882–2899
Kishore PVV, Srinivasa Rao M, Raghava Prasad C, Anil Kumar D (2016) Medical image watermarking: Run through review. ARPN J Eng Appl Sci 11(5):2882–2899
Kumar L, Singh KU (2020) An Analysis of Different Watermarking Schemes for Medical Image Authentication. Eur J Mol Clin Med 7(4):2250–2259
Lei B, Tan EL, Chen S, Ni D, Wang T, Lei H (2014) Reversible watermarking scheme for medical image based on differential evolution. Expert Syst Appl 41(7):3178–3188
Lin CC, Lee TL, Chang YF, Shiu PF, Zhang B (2023) Fragile Watermarking for Tamper Localization and Self-Recovery Based on AMBTC and VQ. Electronics 12:415. https://doi.org/10.3390/electronics12020415
Liu X et al (2019) A Novel Robust Reversible Watermarking Scheme for Protecting Authenticity and Integrity of Medical Images. IEEE Access 7:76580–76598
Loan NA, Parah SA, Sheikh JA, Akhoon JA, Bhat GM (2017) Hiding Electronic Patient Record (EPR) in medical images: A high capacity and computationally efficient technique for e-healthcare applications. J Biomed Inform 73:125–136
Madhuri YU, Chaitanya K (2016) Reversible watermarking technique for data hiding, accurate tamper detection in ROI and exact recovery of ROI. IJARCCE 5(8):184–188
Memon NA, Alzahrani A (2020) Prediction-Based Reversible Watermarking of CT Scan Images for Content Authentication and Copyright Protection. IEEE Access 8:75448–75462
Memon NA, Gilani SAM, Ali A (2011) Watermarking of chest CT scan medical images for content authentication. Int J Comput Math 88:265–280
Moad MS, Kafi MR, Khaldi A (2022) A wavelet based medical image watermarking scheme for secure transmission in telemedicine applications, Microprocess Microsyst, 90, https://doi.org/10.1016/j.micpro.2022.104490
Moad MS, Kafi MR, Khaldi A (2022) Medical image watermarking for secure e-healthcare applications. Multimed Tools Appl 81:44087–44107. https://doi.org/10.1007/s11042-022-12004-0
Mothi R, Karthikeyan M (2019) Protection of bio medical iris image using watermarking and cryptography with WPT. Meas 136:67–73
Mousavi SM, Naghsh A, Abu-Bakar SAR (2014) Watermarking Techniques used in Medical Images: a Survey. J Digit Imaging 27:714–729
Naseem MT, Qureshi IM, Cheema TA (2013) Hash based Medical Image Authentication and Recovery using Chaos and Residue Number System. J Basic Appl Sci Res 3(6):488–495
Nasir M, Jadoon W, Khan IA, Gul N, Shah S, ELAffendi M, Muthanna A (2022) Secure Reversible Data Hiding in Images Based on Linear Prediction and Bit-Plane Slicing, Mathematics,10, https://doi.org/10.3390/math10183311
Nuñez-Ramirez D, Mata-Mendoza D, Cedillo-Hernandez M (2021) Improving preprocessing in reversible data hiding based on contrast enhancement, J King Saud Univ Comput Inf Sci https://doi.org/10.1016/j.jksuci.2021.05.007
Nyeem H, Boles W, Boyd C (2013) A review of medical image watermarking requirements for teleradiology. J Digit Imaging 26(2):326–343
Pandey R, Singh AK, Kumar B (2016) Iris based secure NROI multiple eye image watermarking for teleophthalmology. Multimed Tools Appl 75:14381–14397
Parah SA, Sheikh JA, Ahad F (2015) Information hiding in medical images: a robust medical image watermarking system for E-healthcare. Multimed Tools Appl 76:10599–10633
Priya R, Sadasivam V (2014) A survey on watermarking techniques, requirements, applications for medical images. J Theor Appl Inf Technol 65:103–120
Priya S, Santhi B, Swaminathan P (2014) Study on Medical Image Watermarking Techniques. J Appl Sci 14(14):1638–1642
Qasim AF, Meziane F, Aspin R (2018) Digital watermarking: Applicability for develo** trust in medical imaging workflows state of the art review. Comput Sci Rev 27(2):45–60
Qasim AF, Aspin R, Meziane F, Hogg P (2019) ROI-based reversible watermarking scheme for ensuring the integrity and authenticity of DICOM MR images. Multimed Tools Appl 78(12):16433–16463
Ranjani JJ, Babu M (2018) Medical Image Reliability Verification Using Hash Signatures and Sequential Square Encoding. J Intell Syst 27(1):19–30. https://doi.org/10.1515/jisys-2017-0019
Ravichandran D, Praveenkumar P, Rajagopalan S (2021) ROI-based medical image watermarking for accurate tamper detection, localisation and recovery. Med Biol Eng Comput 59:1355–1372
Rayachoti E, Edara SR, Pradesh A, Pradesh A (2014) Block based medical image watermarking technique for tamper detection and recovery, ar**v:1412.6143 [cs.MM]
Razbonyalı C, Güvenoğlu E (2016) Traditional Data Storage Methods and the Big Data Concepts. Int Res J Eng Technol 03(06):2556–2561
Rostami M, Forouzandeh S, Berahmand K, Soltani M, Shahsavari M, Oussalah M (2022) Gene selection for microarray data classification via multi-objective graph theoretic-based method. Artif Intell Med 123:102228. https://doi.org/10.1016/j.artmed.2021.102228
Sabbane F, Tairi H (2019) Medical image watermarking technique based on polynomial decomposition. Multimed Tools Appl 78(23):34129–34155
Sahu AK, Swain G (2019) High fidelity based reversible data hiding using modified LSB matching and pixel difference. J King Saud Uni Comput Inf Sci. https://doi.org/10.1016/j.jksuci.2019.07.004
Saju G (2019) An effective method for detection and localization of tampering. Int J Inf Syst Comput Sci 8(2):152–154
Showkat S, Parah SA, Gull S (2020) Reversible embedding in medical images with contrast enhancement and tamper detection capability, J Multimed Tools Appl, https://doi.org/10.1007/s11042-020-09732-6
Singh D, Singh SK (2019) Block truncation coding based effective watermarking scheme for image authentication with recovery capability. Multimed Tools Appl 78(4):4197–4215
Singh AK, Dave M, Mohan A (2016) Hybrid technique for robust and imperceptible multiple watermarking using medical images. Multimed Tools Appl 75:8381–8401
Singh AK, Kumar B, Singh G, Mohan A (2017) Medical Image Watermarking Techniques: A Technical Survey and Potential Challenges. In: Singh A, Kumar B, Singh G, Mohan A (eds) Medical Image Watermarking. Multimedia Systems and Applications. Springer, Cham. https://doi.org/10.1007/978-3-319-57699-2_2
Singh S, Singh R, Singh AK, Siddiqui TJ (2018) SVD-DCT Based Medical Image Watermarking in NSCT Domain, In: Hassanien A., Elhoseny M., Kacprzyk J. (eds) Quantum Computing:An Environment for Intelligent Large Scale Real Application, Studies in Big Data, vol 33. Springer, Cham. https://doi.org/10.1007/978-3-319-63639-9_20
Singh P, Devi KJ, Thakkar HK, Kotecha K (2022) Region-Based Hybrid Medical Image Watermarking Scheme for Robust and Secured Transmission in IoMT. IEEE Access 10:8974–8993. https://doi.org/10.1109/ACCESS.2022.3143801
Sinha S, Singh A, Gupta R, Singh S (2018) Authentication and Tamper Detection in Tele-medicine using Zero Watermarking. Procedia Comput Sci 132:557–562
Sinhal R, Sharma S, Ansari IA et al (2022) Multipurpose medical image watermarking for effective security solutions. Multimed Tools Appl 81:14045–14063. https://doi.org/10.1007/s11042-022-12082-0
Solanki N, Malik SK (2014) ROI Based Medical Image Watermarking with Zero Distortion and Enhanced Security. IJMECS 6(10):40–48
Song L, Liu X, Chen S, Liu S, Liu X, Muhammad K, Bhattacharyya S (2022) A deep fuzzy model for diagnosis of COVID-19 from CT images. Appl Soft Comput 122. https://doi.org/10.1016/j.asoc.2022.108883
Soualmi A, Alti A, Laouamer LA (2021) novel blind watermarking approach for medical image authentication using MinEigen value features. Multimed Tools Appl 80:2279–2293
Swaraja K (2018) Medical image region based watermarking for secured telemedicine. Multimed Tools Appl 77:28249–28280
Swaraja K, Meenakshi K, Padmavathi K (2020) An optimized blind dual medical image watermarking framework for tamper localization and content authentication in secured telemedicine. Biomed Signal Process Control 55. https://doi.org/10.1016/j.bspc.2019.101665
Tai WL, Liao ZJ (2018) Image self-recovery with watermark self-embedding. Signal Process Image Commun 65:11–25
Thabit R (2019) Review of Cryptography Applications in eHealth Security Systems. Int J Sci Eng Investig 8(89):110–116
Thabit R (2021) Review of medical image authentication techniques and their recent trends. Multimed Tools Appl 80:13439–13473
Thabit R, Khoo BE (2017) Medical image authentication using SLT and IWT schemes. Multimed Tools Appl 76(1):309–332. https://doi.org/10.1007/s11042-015-3055-x
Thanki R, Borra S, Dwivedi V, Borisagar K (2017) An efficient medical image watermarking scheme based on FDCuT–DCT. Eng Sci Technol Int J 20(4):1366–1379
Tripathi M, Tripathi SP (2013) Rev Med image Watermark Schemes 2(3):1–10
Verma U, Sharma N (2019) Hybrid mode of medical image watermarking to enhance robustness and imperceptibility. Int J Innov Technol Explor Eng 9(1):351–359
Voloshynovskiy S, Pereira S, Iquise V, Pun T (2001) Attack modelling: Towards a second generation watermarking benchmark. Signal Process 81:1177–1214
Wang Z, Bovik AC, Sheikh HR, Simoncelli EP Image quality assessment: From error visibility to structural similarity. IEEE Trans Image Process 13:600–612
Wenyin Z, Shih FY (2011) Semi-fragile spatial watermarking based on local binary pattern operators. Opt Commun 284:3904–3912
Wu HT, Huang J, Shi YQ (2015) A reversible data hiding method with contrast enhancement for medical images. J Vis Commun Image Represent 31:146–153
Ye C, **ong Z, Ding Y, Zhang X, Wang G, Xu F (2015) Joint fingerprinting/encryption for medical image security. Int J Secur Appl 9(1):409–418
Yu M, Wang J, Jiang G, Peng Z, Shao F, Luo T (2015) New fragile watermarking method for stereo image authentication with localization and recovery. AEU Int J Electron Commun 69(1):361–370. https://doi.org/10.1016/j.aeue.2014.10.006
Yu X, Wang C, Zhou X (2017) Review on semi-fragile watermarking algorithms for content authentication of digital images. Futur Int 9(4):1–17
Zear A, Singh AK, Kumar P (2018) A proposed secure multiple watermarking technique based on DWT. DCT and SVD for Appl Med Multimed Tools Appl 77(4):4863–4882
Zhang H, Wang C, Zhou X (2017) Fragile watermarking for image authentication using the characteristic of SVD. Algorithms 10(1):1–12
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
The authors have no relevant financial or non-financial interests to disclose.
The authors have no competing interests to declare that are relevant to the content of this article.
All authors certify that they have no affiliations with or involvement in any organization or entity with any financial interest or non-financial interest in the subject matter or materials discussed in this manuscript.
The authors have no financial or proprietary interests in any material discussed in this article.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Appendix
Appendix
List of Abbreviations
Abbreviation | Meaning |
IoT | Internet of Things |
IoMT | Internet of Medical Things |
MIAT | Medical Image Authentication Technique |
MIP | Medical Image Processing |
MITD | Medical Image Tamper Detection |
MITL | Medical Image Tamper Localization |
MITR | Medical Image Tamper Recovery |
MIW | Medical Image Watermarking |
MIWT | Medical Image Watermarking Technique |
WMI | Watermarked Medical Image |
WTMIA | Watermarking Techniques For Medical Image Authentication |
EHI | Electronic Health Information |
EPI | Electronic Patient Information |
CT | Computed Tomography |
MRI | Magnetic Resonance Imaging |
ROI | Region of Interest |
RONI | Region of Non Interest |
LSB | Least Significant Bit |
DCT | Discrete Cosine Transform |
DWT | Discrete Wavelet Transform |
DFT | Discrete Fourier transform |
LFC | Low Frequency Component |
MFC | Middle Frequency Component |
HFC | High Frequency Component |
HH | High High |
LL | Low Low |
HL | High Low |
LH | Low High |
RDH | Reversible Data Hiding |
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Gull, S., Parah, S.A. Advances in medical image watermarking: a state of the art review. Multimed Tools Appl 83, 1407–1447 (2024). https://doi.org/10.1007/s11042-023-15396-9
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-023-15396-9