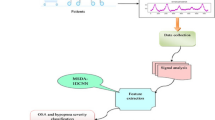
Abstract
Methamphetamine (MA) is a neurological drug, which is harmful to the overall brain cognitive function when abused. Based on this property of MA, people can be divided into those with MA abuse and healthy people. However, few studies to date have investigated automatic detection of MA abusers based on the neural activity. For this reason, the purpose of this research was to investigate the difference in the neural activity between MA abusers and healthy persons and accordingly discriminate MA abusers. First, we performed event-related potential (ERP) analysis to determine the time range of P300. Then, the wavelet coefficients of the P300 component were extracted as the main features, along with the time and frequency domain features within the selected P300 range to classify. To optimize the feature set, F_score was used to remove features below the average score. Finally, a Bidirectional Long Short-term Memory (BiLSTM) network was performed for classification. The experimental result showed that the detection accuracy of BiLSTM could reach 83.85%. In conclusion, the P300 component of EEG signals of MA abusers is different from that in normal persons. Based on this difference, this study proposes a novel way for the prevention and diagnosis of MA abuse.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
Introduction
Methamphetamine (MA) is a neurological drug, which can cause serious mental symptoms, such as hallucinations and delusions. Light MA addiction can cause anxiety and other emotions, while severe MA addiction can cause depression and suicidal tendency (Zweben et al. 2004). Besides, some MA abusers suffer from psychosis and schizophrenia (Liu et al. 2017). Unfortunately, even though the drug is known to be too harmful to humans, little can be done about its addiction (Mooney et al. 2014). More unfortunately, unlike heroin and cocaine, MA formulas are available via the Internet and produced using common daily necessities (Lineberry and Bostwick 2006), which has accelerated its spread.
Electroencephalography (EEG) signals reflect the electrophysiological activity of nerve cells in the brain. In clinical practice, EEG signals have been shown to include a large number of physiological and pathological information (Zhong 2002). Such information can often give more details on a person?s physical condition, which has profound significance for both the prevention and remedy of diseases. In 1932, Dietch first used Fourier transform to analyze the collected EEG signals (Dietsch 2002). Since then, many analytical methods have been applied to study EEG signals, including time-domain and frequency-domain analysis, wavelet transform, artificial neural network (ANN) analysis and nonlinear dynamics analysis (Yousefi et al. 2022; Rafik and Ilyes 2023).
MA primarily affects the central nervous system. Therefore, consuming MA would lead to abnormal EEG signals of drug addicts (Prabhat et al. 2022; Gege et al. 2023). In this study, we attempted to record the EEG signals of MA abusers and analyze the differences in these signals between MA abusers and normal persons, which would support the exploration of the principle of action and treatment methods of MA.
As an important indicator of EEG signals, P300 is related to selective attention, memory renewal, motivation, stimulation significance and the activation of inhibition process (Turnip et al. 2013). Up to now, many studies have intensively investigated the detection of MA abuse using P300 (**xiang et al. 2013; Zhong et al. 2020; xxx yyy; Huang et al. 2023). MA abusers were asked to perform the same task as normal subjects, and it was shown that the P300 component can be successfully used to differentiate MA abusers from healthy subjects (Haifeng et al. 2015; Shuguang et al. 2018). With the advancements in neuroscience, researchers have developed a variety of feature extraction approaches of EEG signals to predict human psychiatric disorders (Shahmohammadi et al. 2016; Ahmadlou et al. 2013). However, little work has been so far devoted to extract the EEG P300 features of MA abusers to set up an automatic classification system and detect MA abusers.
EEG signals are non-stationary random signals (Shin et al. 2015), thus, conventional Fourier transform can only be used to see which frequency domains are EEG signals composed of, while the corresponding time information of each frequency component cannot be obtained. This means that there will be multiple identical time-domain graphs corresponding to one frequency-domain graph only. Hence, it is necessary to mention the wavelet transform, which can be used to decompose signals of different resolutions (Zhang 2020). By scaling and translation of the basis function, the window becomes narrower at high frequencies and wider at the low frequency, so that accurate frequency and time information can be obtained. Due to the superiority of the wavelet in signal transformation, wavelet transform is known as the “digital microscope” (Yu-Sheng et al. 2013). In view of the advantage of the wavelet transform, it was used as the extractor of time-frequency features of P300 signals to obtain wavelet coefficients as the main features (** et al. 2019).
Classical machine learning algorithms are commonly used methods for neurophysiological signal analysis and pattern recognition. The hypothesis in this study is that P300 signals in cognitive processes can demonstrate significant differences between MA abusers and normal persons. By extracting P300 features, the machine learning algorithm is able to recognize MA abusers.
The main contributions of this work are listed as follows:
-
(1)
For the first time, we used the features of the P300 component of EEG signals to detect MA abusers. Compared with other methods, the P300 component shows more differences between healthy people and MA abusers, and it is simpler to extract its features.
-
(2)
MA addiction could be detected through a few stimulation experiments, and the proposed model improved the detection efficiency.
-
(3)
Compared with biochemical detection methods, the detection results of our model were more reliable.
The remaining of this article is organized as follows. Chapter 1 mainly includes a short introduction to the research overview and background. In chapter 2, we present related work of EEG-based MA classification. Chapter 3 describes the experimental methods and process of data analysis. Chapter 4 presents the final results and related discussion, and a conclusion is presented in chapter 5.
Related Work
EEG-Based Research of Methamphetamine
MA can lead to substance use disorder (SUD), directly affect the central nervous system and impose a gigantic burden for the human body. The influence of MA on the brain can be mapped through the brain activity. EEG can reflect the activation process of the brain under various stimulation. It can enlarge the tiny biological electricity to a curvilinear record graph, recording the neural activity in ms. Its excellent temporal resolution ensures more precise analysis of neural activity.
Many studies have extensively investigated the effects of methamphetamine using EEG signals (Di et al. 1.
Data Recording and Preprocessing
Continuous EEG was recorded using the Brain Vision Recorder 2.0 system (Brain Products Company, Munich, Germany). In the process of recording, FCz was regarded as the reference electrode, and the ground electrode was AFz. An electrode placed approximately 2 cm below the right eye and centered under the pupil was used to record vertical electrooculogram (EOG). The recorded EEG signals were amplified and digitized at a sampling rate of 1000 Hz in the DC acquisition mode, and the electrode impedance was required below 10 k\(\Omega\).
The data were processed offline after recording. The operation of processing was executed by EEGLAB and ERPLAB toolboxes based on the MATLAB Platform. Data were re-referenced to a mastoid electrode averaged reference, down_sampled to 250 Hz, filtered by a 30 Hz low-pass filter. Artifacts, such as including spikes, EEG drift and abiotic signals were manually removed. Then the eye electrical interference was eliminated through independent component analysis (ICA). The range of each epoch was \(-200\) to 1000 ms, and we used 200 ms before stimulus presentation as baseline correction. The event-related potential (ERP) of each channel under three stimulations after preprocessing is shown in Fig. 2. As shown in Fig. 2, there was a big difference in the ERP between two groups, especially in the P300 under S2 stimulation. Therefore, only the epochs of S2 were extracted, and every five epochs of each subject were overlapped and averaged. Finally, 144 groups of data were obtained in the addiction and healthy groups, respectively.
Discrete Wavelet Transforms (DWT) for Signal Analysis
Most biological signals in nature are non-stationary random signals; hence, wavelet transform is usually used in biomedical signal field. The time domain features, frequency domain features and wavelet coefficients of P300 stimulated by the S2?signal were abstracted for classification in this work.
The wavelet transform is operated by two basic functions: scale function \(\phi (t)\) and wavelet function \(\psi (t)\), which are the prototype forms of the following class of orthonormal basis functions, respectively:
where k controls the translation of the wavelet base in the time domain, j denotes the parameter in the frequency domain, which determines the frequency features of the wavelet base, and Z is a set of integers.
The complete wavelet expansion f(t) is defined by the wavelet function and the scale function, as follows:
where the coefficients \(c(j_0,k)\) and d(j, k) are calculated by inner product as follows:
This is the final and core form of the wavelet transform (Gandh et al. 2010). In this study, the quadratic B-spline function (Gan et al. 2017) was selected as the mother wavelet. The N-order approximate coefficients can be calculated by wavelet decomposition. Given that the samples are 250 Hz, a fifth-order wavelet decomposition is performed. In the wavelet transform multi-resolution algorithm, low-pass (LP) and high-pass (HP) filters use the same wavelet coefficients. The coefficients with LP filter are related to the scaling function. Its outputs are called the approximate quantity (A). While the HP filter have a connection with the wavelet function, and its outputs are called detail quantity (D).
Feature Extraction
The frequency range of P300 has been confirmed to be in the delta band (Gao et al. 2010). Therefore, using the method of wavelet decomposition, we calculated the wavelet coefficients of the delta band as the wavelet features. Furthermore, the time and frequency domain features of all signals X(t) have also previously been added to classify the two types of signals (Gao et al. 2014). Several time domain features were calculated as follows:
-
(1)
Maximum amplitude (MAA): the maximum amplitude of X(t), calculated as follows:
$$\begin{aligned} MAA = \max \{ X(t)\} \end{aligned}$$(6) -
(2)
Minimum amplitude (MIA): the minimum amplitude of X(t), calculated as follows:
$$\begin{aligned} MIA = \min \{ X(t)\} \end{aligned}$$(7) -
(3)
Latency (LAT): the time at which MAA of X(t) occurs, calculated as follows:
$$\begin{aligned} LAT = \{ X(LAT) = MAA\} \end{aligned}$$(8) -
(4)
Ratio latency to maximum (RLM): the ratio latency to maximum amplitude of X(t), calculated as follows:
$$\begin{aligned} RLM = \frac{{MAA}}{{LAT}} \end{aligned}$$(9) -
(5)
Positive area (PA): the sum of the positive signal values of X(t), calculated as follows:
$$\begin{aligned} PA = \sum \limits _{t1}^{t2} {\frac{{X(t) + \left| {X(t)} \right| }}{2}} \end{aligned}$$(10)where t1 and t2 denote the initial time value and cut-off time value of P300, respectively.
-
(6)
Difference between positive and negative amplitude (DPN), calculated as follows:
$$\begin{aligned} DPN = MAA - MIA \end{aligned}$$(11)
Let Y(f) be the power spectral density of X(t). Then, the following calculation methods can be used to extract the frequency domain features:
-
(1)
Maximum frequency (MF): the maximum frequency of X(t), calculated as follows:
$$\begin{aligned} MF = \{ Y(MF) = Y{(f)_{\max }}\} \end{aligned}$$(12) -
(2)
Average frequency (AF): calculated by a frequency weighted average, where the weighted coefficient is the value of Y(f). It can be calculated as follows:
$$\begin{aligned} AF = \frac{{\int _0^{125} {f \times Y(f)df} }}{{\int _0^{125} {Y(f)df} }} \end{aligned}$$(13)
A total of 31 features under each channel were involved in the classification, and an EEG sample with features from 62 channels was a 1922-dimensional vector. The entire feature extraction mechanism is summarized in Fig. 3, and the pseudo-code of the algorithm with feature extractor is shown in Algorithm 1.
However, a lot of repetitive or redundant information exist in EEG signals (Amin et al. 2015), so there is a strong correlation between the features, which can weaken the generalization ability of the model and reduce the classification accuracy. Thus, the F_score is still needed to select which features would have better classification effect.
F_score for Feature Selection
F_score can measure the discrimination of two sets of features (**e et al. 2010). Let \({x_k} \in {R^m},k = 1,2,\ldots ,n\), be the given recording set, and the number of positive and negative samples be \({n_ + }\) and \({n_ -}\), respectively. Then, the F_score value of the ith feature of the training sample can be defined as follows:
where \({{x_{k,j}}^{( + )}}\) and \({{x_{k,j}}^{( - )}}\) are the kth positive and negative sample points of the ith feature, respectively. \({\overline{{x_i}} }\), \({\overline{{x_i}^{( + )}} }\) and \({\overline{{x_i}^{( - )}} }\) represent the average of the whole, positive and negative data sets, respectively. The degree of the discrimination of the feature is decided by the value of the F_score (Chen and Lin 2006).
In this study, F_score was calculated for all features, and we removed the features with a score below the average score. All features will be put into the feature set in descending order to form the final feature set. The feature selection algorithm is shown in Algorithm 2.
Classification
LSTM has shown a good effect in a variety of applications in image recognition, text analysis, disease prediction and so on (Zhang et al. 2019). LSTM is an improved and upgraded RNN. It adds weight control over different moments of memory through a gate controller. The memory unit structure of LSTM is shown in Fig. 4.
c represents a memory state, which is the most important part of the entire memory unit (Houdt et al. 2020). As shown in Fig. 4, it is directly transferred on the entire structural chain, using only a small number of linear operations, hence the information is substantially unchanged during transmission. Meanwhile, the memory unit contains three intelligent “gate” structures to control the flow of information, namely forget gate input gate and output gate. According to the choice of the gate, the information contained in the memory status can be added or deleted. It includes a point-by-point multiplication operation of vectors and a sigmoid function, mainly with the following parts:
\({C_{t - 1}}\) represents the memory state at time \(t-1\), which records historical information of all time steps. It belongs to the long-term memory of the model.
\({h_{t - 1}}\)represents the output at time \(t-1\), which mainly records the time step information, thus belonging to the short-term memory of the model.
Forget gate \(f_t\), input gate \(i_t\) and output gate \(o_t\), are between 0 and 1. The memory state C of the jth memory unit at time t is the operated result of the input gate \(i_t^j\), forget gate \(f_t^j\) and previous memory state \(C_{t-1}^j\) (Zaremba et al. 2014). The memory status C at time t is defined as:
such that
where w, b, \(\sigma\) and \(x_t\) represent the weight matrix, bias parameters, sigmoid activation functions corresponding to each gate, and input of the model at time t, respectively. When the memory unit is updated, the output gate \(o_t\) and the hidden layer \(h_t\) can be represented as:
Traditional LSTM networks mainly use historical background information. However, lacking future feature information may lead to an incomplete feature matrix. As for BiLSTM, it realizes bi-directional features reading by combining the forward and backward LSTM layers, hence fully taking the context feature information (Zhang et al. 2020). The model structure is shown in Fig. 5.
Given that at time t, \(\uparrow {h_t}\) is a hidden state of the forward LSTM output, and \(\downarrow {h_t}\) is a hidden state of the backward LSTM, then \(h_t\) can be calculated as follows:
Studies have proven that the BiLSTM model containing overall information is better than other classification algorithm (Wang et al. 2016).
Cross-Validation
To ensure that all data can be used for classification, we performed 12-fold cross-validation (CV) (Xu and Goodacre 2018). First, we randomly divided all the feature samples into 12 sample sets. Within these 12 sets, 11 sets were used to train model, and can be denoted by \({D_{tra}}\), while the 12th set was selected to test model, and denoted by \({D_{tes}}\). We repeated this process 12 times, with each set being used once for testing. Furthermore, we applied an additional 8-fold cross-validation on each \({D_{tra}}\) set, randomly dividing each set \({D_{tra}}\) into 8 subsets, where 7 sets served as training subsets (\({D_{s\_tra}}\)) and the 8th set served as the validation subset (\({D_{s\_val}}\)). \({D_{s\_tra}}\) and \({D_{s\_val}}\) were then assigned to the classifier for training and validating its performance. This process was repeated 8 times, with each subset being used once for validation, to overcome the overfitting problem. We used the following performance measures for classification:
-
(a)
Balanced validation accuracy (BVA): For each Dtra, BVA was obtained by averaging 8 pairs of sensitivities and specificities (8-fold CV). By comparing the classification result of different feature sets, the best BVA can be obtained and the optimal classifier (and its parameters) could be obtained as the one with the highest BVA. It is worth knowing that the best results maybe have some differences for a different set \({D_{tra}}\).
-
(b)
Balanced Testing Accuracy (BTA): BTA was obtained by averaging the sensitivity and specificity, and the sensitivity and specificity is the test result of the classifier which have trained completely. Through the 12-fold CV, we could obtain the average of all 12 BTAs as ABTA (average BTA). Then, the final optimal classifier (and its parameters) was decided when the BTA reached the highest among all the 12 BTAs.
The cross-validation illustration is shown in Fig. 6. The feature sample set was formed after the F_score feature selection operation, and after two layers of CV, the best training model and the average test accuracy were obtained.
Flow chart of the classification. The operation results and data are expressed in italics. CV i: The first layer cross-validation, testing the optimal model of the second layer CV training. CV II: The second layer cross-validation, training the best model and verify. The two branches of orange lines represent the input of the training set and testing set in the first layer CV, respectively. The same is true for the meaning of the red line in the second layer CV
Statistical Evaluation of Performance
For classification models, the test accuracy is a very good and intuitive evaluation indicator. However, accurate rates do not always fully represent a model as good or bad. Therefore, the performance of the classifier was also evaluated by the following specificity (Spe) and sensitivity (Sen) metrics (Subasi 2007):
where sensitivity is the true positive rate, reflecting the probability of missed diagnosis, and specificity is the true negative rate, reflecting the probability of misdiagnosis. The following statistics are used to calculate specificity and sensitivity:
TP (True Positive): the number of addiction cases identified by the classifier, which are actually addiction cases.
FN (False Negative): the number of healthy cases identified by the classifier, which are actually addiction cases.
TN (True Negative): the number of healthy cases identified by the classifier, which are actually healthy cases.
FP (False Positive): the number of addiction cases identified by the classifier, which are actually healthy cases.
Results
Classifier Performance
In this study, 288 cases were classified, including 144 in the addiction group and 144 in the healthy group.
The time-domain features, frequency-domain features and wavelet coefficients of the delta band were used as classification features. Then, the features of 62 channels were connected in series. To improve the performance of classifier and reduce the computation and experiment time, F_score was used to evaluate the discrimination degree of the feature data. Next, arranging features in descending order, and classification was performed. In this study, the classification accuracy of SVM and BiLSTM were compared. To increase the comparability, all BiLSTM and SVM classifiers used the sigmoid activation function. The test accuracy of 12-fold cross-validation was calculated, and the violin diagram was plotted (see Fig. 7). It can be seen that the classification results obtained by BiLSTM in cross-validation are more stable compared with SVM.
Table 2 shows the performance evaluation results of the feature dimension with the highest classification accuracy after classifying the data with different classifiers. It was observed that when BiLSTM was used as the classifier, the classification accuracy was better. The P300 features of EEG signals were used to classify MA abusers and healthy subjects, and we achieved a classification accuracy rate of 83.85%.
Performance of Different Electrodes
In addition, due to the characteristics of BiLSTM, we also compared the use of different electrode signals separately for classification. Among them, 20 electrodes achieved a classification accuracy of 60% (see Table 3). It can be seen from Table 3 that most of the electrodes were located in the frontal?lobe, to which the advanced functions of brain, such as judgment, decision making, thinking and executive control are related (Anne et al. 2012). Therefore, the signal of the frontal?lobe can more clearly reflect the mental activity of the two groups during the task implementation. The C3 and C4 electrodes were substantially mapped in the primary motor cortex region, and the region electrode signal also exhibited strong differences. This may indicate that MA has an impact on the function of exercise execution in MA abusers. Meanwhile, this phenomenon may also be related to the symptoms in patients with amphetamine psychosis, such as irritation, anxiety and psychomotor agitation.
Discussion
Identification of MA Addiction Based on EEG
The previous research indicates that men and women exhibit similar MA-related characteristics and behaviors (Brecht et al. 2004). Compared with men, women\('\)s symptoms were more specific to MA and they responded better to treatment (Dluzen and Liu 2008). Therefore, we collected EEG signals from 18 female perpetrators and 22 healthy females, processed using MATLAB R2014b software and the EEGLAB toolbox. After preprocessing, we obtained 144 and 184 groups of data, respectively. Figure 2 illustrates significant differences between the signals of the two groups. The ERP amplitudes corresponding to MA-related stimuli in MA addicts are higher than those in the control group. Studies have shown that MA addicts exhibit attentional bias towards MA-related cues when exposed to such stimuli (Gege et al. 2023; Di et al. 2018). Therefore, this study can provide a judgement basis for the prevention of MA addiction. In future studies, the other component of EEG signals such as N300, P200 and N200 can be analyzed jointly. Although the difference between the two groups of people regarding those components is less than that of P300, it may contain some critical factors that do not present in P300.
Data Availability
The datasets analyzed during the current study are not publicly available, but are available from the corresponding author on reasonable request.
References
Ahmadlou M, Ahmadi K, Rezazade M, Azad-Marzabadi E (2013) Global organization of functional brain connectivity in methamphetamine abusers. Clin Neurophysiol 124(6):1122–1131
Amin HU, Malik AS, Kamel N, Hussain M (2015) A novel approach based on data redundancy for feature extraction of EEG signals. Brain Topogr 29(2):207–217
Anne C, Etienne K, O’Doherty JP (2012) Reasoning, learning, and creativity: frontal lobe function and human decision-making. PLoS Biol 10(3):1001293
Brecht ML, OBrien A, Mayrhauser CV (2004) Methamphetamine use behaviors and gender differences. Addict Behav 29(1):89–106
Chen YW, Lin CJ (2006) Combining SVMs with various feature selection strategies. Springer, New York
Chen T, Xu R, He Y, Wang X (2016) Improving sentiment analysis via sentence type classification using BILSTM-CRF and CNN. Expert Syst Appl
Chen C-C, Tsai M-C, Wu EH-K, Chung C-R, Lee Y, Chiu P-R, Tsai P-Y, Sheng S-R, Yeh S-C (2022) Neuronal abnormalities induced by an intelligent virtual reality system for methamphetamine use disorder. IEEE J Biomed Health Inform 26(7):3458–3465. https://doi.org/10.1109/JBHI.2022.3154759
Cui F, Wang R, Ding W, Chen Y, Huang L (2022) A novel DE-CNN-BILSTM multi-fusion model for EEG emotion recognition. Mathematics 10:582
Dayanti N, Kusumandari DE, Kusumaningrum HB, Alexandra TC (2023) Characterization of EEG-p300 signals in drug users. J Phys 2673(1):012009. https://doi.org/10.1088/1742-6596/2673/1/012009
Di Z, Zhang M, Tian W, **nyu C, Lu Y, Yi L, Tian-Le X, Wenbo L, Ti-Fei Y (2021) Neurophysiological correlate of incubation of craving in individuals with methamphetamine use disorder. Mol Psychiatry 26:6198–6208. https://doi.org/10.1038/s41380-021-01252-5
Dietsch G (2002) Fourier-analyse von elektrencephalogrammen des menschen. Pflger’s Archiv fr die gesamte Physiologie des Menschen und der Tiere
Ding X, Li Y, Li D, Li L, Liu X (2020) Using machine learning approach to distinguish patients with methamphetamine dependence from healthy subjects in a virtual reality environment. Brain Behav 10(11):01814
Dluzen DE, Liu B (2008) Gender differences in methamphetamine use and responses: a review. Gend Med 5(1):24–35
Gan Y, Sun Z, Chen Z, Zhang X, Liu Y (2017) Enhancement of the material point method using bspline basis functions. Int J Numer Methods Eng 113:411–431
Gandh T, Panigrahi BK, Bhatia M, Anand S (2010) Expert model for detection of epileptic activity in EEG signature. Expert Syst Appl 37(4):3513–3520
Gao J, Wang P, Zheng C (2010) Lie detection method based on p300 and machine learning. Hsi-An Chiao Tung Ta Hsueh 44:120–124
Gao JF, Zhang WJ, Yang Y, Hu JJ, Guan JA (2014) Lie detection study based on p300 and extreme learning machine. Dianzi Keji Daxue Xuebao 43(2):301–305
Gege Z, Su H, Wang P, Wang J, Jiang H, Zhang L, Kang X (2023) Non-invasive brain–computer interfaces: a new perspective on the assessment and classification of individuals with methamphetamine addiction. SN Comp Clin Med. https://doi.org/10.1007/s42399-023-01585-y
Haifeng J, Wenxu Z, Hong C, Chuanwei L, Jiang D, Haiming S, Zhikang C, Din X, Jijun W, Min Z (2015) P300 event-related potential in abstinent methamphetamine-dependent patients. Physiol Behav 149:142–148
Hou Y, Jia S, Zhang S, Lun X, Shi Y, Li Y, Yang H, Zeng R, Lv J (2020) Deep feature mining via attention-based BILSTM-GCN for human motor imagery recognition. Front Bioeng Biotechnol 9:706229
Houdt GV, Mosquera C, Nápoles G (2020) A review on the long short-term memory model. Artif Intell Rev 53:1–27
Howells FM, Temmingh HS, Hsieh JH, Van Dijen AV, Baldwin DS, Stein DJ (2018) Electroencephalographic delta/alpha frequency activity differentiates psychotic disorders: a study of schizophrenia, bipolar disorder and methamphetamine-induced psychotic disorder. Transl Psychiatry 8(1):75
Huang G, Han C, Yang J, Ye C, Javed I, Liu F, Kong Z, Li Y, Zhu Y, Yi G, Ju C, Jia X, Yang M (2023) Neural basis of the attention bias during addiction Stroop task in methamphetamine-dependent patients with and without a history of psychosis: an ERP study. Front Psychol. https://doi.org/10.3389/fpsyg.2023.1173711
Jia** Y, Yuejia L, ** H, Yan X, Meng F (2009) Neural correlates of the females’ susceptibility to negative emotions: an insight into gender-related prevalence of affective disturbances. Hum Brain Mapp 30(11):3676–3686
** Z, Wei LI, Jian-Cheng YU, Dong-Cen XU, **u-Lan DU (2019) Classification of EEG signals in different states based on combined classifier. Control Decision
**xiang L, Yan C, Yan W (2013) Application of event-related potentials p300 on cognitive abilities screening of patients with methamphetamine dependence. China J Health Psychol 149:142–8
Khajehpour H, Makkiabadi B, Ekhtiari H, Bakht S, Alireza N (2019) Disrupted resting-state brain functional network in methamphetamine abusers: a brain source space study by EEG. PLoS ONE 14(12):0226249
Khajehpour H, Mohagheghian F, Ekhtiari H, Makkiabadi B, Jafari A, Eqlimi E, Harirchian M (2019) Computer-aided classifying and characterizing of methamphetamine use disorder using resting-state EEG. Cogn Neurodyn. https://doi.org/10.1007/s11571-019-09550-z
Li X, Zhou Y, Zhang G, Lu Y, Zhou C, Wang H (2022) Behavioral and brain reactivity associated with drug-related and non-drug-related emotional stimuli in methamphetamine addicts. Front Hum Neurosci. https://doi.org/10.3389/fnhum.2022.894911
Lian S, Xu J, Zuo G, Wei X, Zhou H (2021) A novel time-incremental end-to-end shared neural network with attention-based feature fusion for multiclass motor imagery recognition. Comput Intell Neurosci 2021(2):1–16
Lin Q, Li D, Hu C, Shen Z, Wang Y (2022) Altered EEG microstates dynamics during cue-induced methamphetamine craving in virtual reality environments. Front Psychiatry. https://doi.org/10.3389/fpsyt.2022.891719
Lineberry TW, Bostwick JM (2006) Methamphetamine abuse: a perfect storm of complications. Mayo Clin Proc 81(1):77–84
Liu Y, Hao B, Shi Y, Xue L, Wang X, Chen Y, Zhao H (2017) Violent offences of methamphetamine users and dilemmas of forensic psychiatric assessment. Forensic Sci Res 2(1):7
Madhavan S, Tripathy RK, Pachori RB (2020) Time-frequency domain deep convolutional neural network for the classification of focal and non-focal EEG signals. IEEE Sens J 20(6):3078–3086
Michael B, Williams Janet BW, Spitzer Robert L (2015) User’s guide for the structured clinical interview for DSM-5 disorders-clinician version (SCID-5-CV)
Mooney LJ, Cooper C, London ED, Chudzynski J, Dolezal B, Dickerson D, Brecht M-L, Peate J, Rawson RA (2014) Exercise for methamphetamine dependence: rationale, design, and methodology. Contemp Clin Trials 37(1):139–147
Prabhat S, Nikita K, Sooyeun L, Ji Hae S, Jee-Heon J, Simmyung Y (2022) Methamphetamine induced neurotoxic diseases, molecular mechanism, and current treatment strategies. Biomed Pharmacotherapy 154:113591. https://doi.org/10.1016/j.biopha.2022.113591
Rafik D, Ilyes D (2023) Nonlinear and chaos features over EMD VMD decomposition methods for ictal EEG signals detection. Comput Methods Biomech Biomed Eng. https://doi.org/10.1080/10255842.2023.2271603
Shafiee-Kandjani AR, Jahan A, Moghadam-Salimi M, Fakhari A, Sadeghpour S (2020) Resting-state electroencephalographic coherence in recently abstinent methamphetamine users. Int J High Risk Behav Addict 9(4):103606
Shahmohammadi F, Golesorkhi M, RiahiKashani M, Sangi M, Yoonessi A (2016) Neural correlates of craving in methamphetamine abuse. Basic Clin Neurosci 7(3):221–230
Shin Y, Lee S, Ahn M, Cho H, Jun S, Lee H-N (2015) Noise robustness analysis of sparse representation based classification method for non-stationary EEG signal classification. Biomed Signal Process Control. https://doi.org/10.1016/j.bspc.2015.05.007
Shuguang W, Ya Z, Qi L, Weine D, **xiu S, Haiyan W, Xun L (2018) Enhanced neural responses to monetary rewards in methamphetamine use disordered individuals compared to healthy controls. Physiol Behav 195:0031938418306371
Subasi A (2007) EEG signal classification using wavelet feature extraction and a mixture of expert model. Expert Syst Appl 32(4):1084–1093
Turnip A, Hutagalung SS, Pardede J, Soetraprawata D (2013) P300 detection using a multilayer neural network classifier based on adaptive feature extraction. Int J Brain Cognitive Sci 2(5):63–75
Turnip A, Kusumandari D, Hidayat T (2018) Brain map** of drug addiction in withdrawal condition based p300 signals. J Phys 1007:012060. https://doi.org/10.1088/1742-6596/1007/1/012060
Vasconcelos A, Malloy-Diniz L, Correa H (2012) Systematic review of psychometric proprieties of barrattimpulsiveness scale version 11 (bis-11). Clin Neuropsychiatry 9:61–74
Wang Y, Feng S, Wang D, Zhang Y, Yu G (2016) Context-aware Chinese microblog sentiment classification with bidirectional lstm. In: Asia-Pacific Web Conference
**e JY, Wang CX, Jiang S, Zhang Y (2010) Feature selection method combing improved f-score and support vector machine. J Comput Appl 30(4):993–996
**ong Y, Gao J, Zhang J (2019) Detection methamphetamine patients using ERP features. In: 2019 6th international conference on information science and control engineering (ICISCE), pp 259–262 . https://doi.org/10.1109/ICISCE48695.2019.00059
Xu Y, Goodacre R (2018) On splitting training and validation set: a comparative study of cross-validation, bootstrap and systematic sampling for estimating the generalization performance of supervised learning. J Anal Test 2(3):14
Yang J, Huang X, Wu H, Yang X (2020) EEG-based emotion classification based on bidirectional long short-term memory network. Procedia Comput Sci 174:491–504
Yousefi MR, Golnejad S, Hosseini MM (2022) Comparison of EEG based epilepsy diagnosis using neural networks and wavelet transform
Yu-Sheng XI, Wei-Jie Z, Ya-** G (2013) Feature extraction algorithm of carotid artery pulse wave based on wavelet transform. Chin J Med Phys
Zaremba W, Sutskever I, Vinyals O (2014) Recurrent neural network regularization. Eprint Arxiv
Zhang D (2020) Fundamentals of image data mining: analysis, features, classification and retrieval
Zhang B, Zhang H, Zhao G, Lian J (2019) Constructing a pm2.5 concentration prediction model by combining auto-encoder with bi-LSTM neural networks. Environ Modell Softw 124:104600
Zhang J, Zi L, Hou Y, Deng D, Wang M (2020) A c-bilstm approach to classify construction accident reports. Appl Sci 10(17):5754
Zhong J (2002) The EEG signals processing based on Wigner distribution. Signal Process
Zhong N, Chen T, Zhu Y, Su H, Zhao M (2020) Smaller feedback-related negativity (FRN) reflects the risky decision-making deficits of methamphetamine dependent individuals. Front Psychol 11:320
Zhong Y, Wang Y, He Z, Lin Z, Pang N, Niu L, Guo Y, Pan M, Meng L (2021) Closed-loop wearable ultrasound deep brain stimulation system based on EEG in mice. J Neural Eng 18(4):0460–8
Zolfaghari S, Sarbaz Y, Shafiee-Kandjani AR (2024) Analysing the behaviour change of brain regions of methamphetamine abusers using electroencephalogram signals: Hope to design a decision support system. Addict Biol 29(2):13362. https://doi.org/10.1111/adb.13362
Zuckerman M (2007) The sensation seeking scale v (SSS-V): still reliable and valid. Personality Individ Differ 43(5):1303–1305
Zuo X, Zhang C, Cong F, Zhao J, Hamalainen T (2022) Driver distraction detection using bidirectional long short-term network based on multiscale entropy of EEG. IEEE Trans Intell Transp Syst 23:1–14. https://doi.org/10.1109/TITS.2022.3159602
Zweben JE, Cohen JB, Christian D, Galloway GP, Salinardi M, Parent D, Iguchi M (2004) Psychiatric symptoms in methamphetamine users. Am J Addict 13(2):181–190
Funding
This work was supported by the National Nature Science Foundation of China under Grants 82102028, 61773408, 62072218, 62076257 and 81601586, Applied Basic Research Programme of Wuhan under Grant 2020020601012239, the Fundamental Research Funds for the Central Universities, South-Central Minzu University under Grant CPT22021. Furthermore, the authors would like to express their gratitude to EditSprings (https://www.editsprings.cn) for the expert linguistic services provided.
Author information
Authors and Affiliations
Contributions
Hui Zhou: Methodology, Validation, Writing—original draft, Software, Visualization. Jiaqi Zhang: Conceptualization, Methodology, Writing—original draft, Validation. Junfeng Gao: Visualization, Methodology, Writing—review and editing, Investigation. Xuanwei Zeng: Investigation, Data curation, Software. **angde Min: Methodology, Funding acquisition, Data curation. Huimiao Zhan: Software, Statistical analysis, Validation. Hua Zheng: Resources, Data curation. Huaifei Hu: Writing—review and editing. Yong Yang: Supervision, Methodology, Funding acquisition. Shuguang Wei: Formal analysis, Supervision, Project administration.
Corresponding authors
Ethics declarations
Conflict of interest
The authors declare that they have no known competing financial interests or personal relationships that could have appeared to influence the work reported in this paper.
Ethical Approval
The study protocol was approved by the Institutional Review Board of the Institute of Psychology of the Chinese Academy of Science.
Consent to Participate
All subjects obtained remuneration and agreed to the experiment.
Consent for Publication
All authors have approved the manuscript and the submission to this journal.
Code Availability
The code generated during the current study are not available.
Additional information
Communicated by Helmut Laufs.
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/.
About this article
Cite this article
Zhou, H., Zhang, J., Gao, J. et al. Identification of Methamphetamine Abusers Can Be Supported by EEG-Based Wavelet Transform and BiLSTM Networks. Brain Topogr (2024). https://doi.org/10.1007/s10548-024-01062-2
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s10548-024-01062-2