Search
Search Results
-
Blind image—variant based authentication method
There is a plethora of image authentication techniques in the literature. Almost all of these methods use either a form of watermarking or data...

-
A perceptual entanglement-based image authentication with tamper localisation
With the recent development in image editing tools the content of digital images can be easily manipulated. Research efforts are being deployed to...

-
Public key based bidirectional shadow image authentication without pixel expansion in image secret sharing
Image secret sharing (ISS) is gaining popularity due to the importance of digital images and its wide application to cloud-based distributed storage...
-
Asymmetric image authentication algorithm using double random modulus decomposition and CGI
In this paper, we have proposed asymmetric image encryption cum authentication cryptosystem based on double random modulus decomposition using...

-
Reversible image authentication using a central folding strategy with two images
In reversible image authentication (RIA) methods, it is common to use a reversible hiding method to embed the authentication code (AC) bits into each...

-
A reversible watermarking for image content authentication based on wavelet transform
In the special field of anti-counterfeit authentication, such as medical archive protection, there is a problem of copyright infringement. To protect...

-
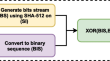
Stabilized Performance Maximization for GAN-based Real-Time Authentication Image Generation over Internet
Providing the completely automated public test to tell computers and humans apart (CAPTCHA) services that are not vulnerable to learning is an...

-
Image authentication and recovery: Sudoku puzzle and MD5 hash algorithm based self-embedding fragile image watermarking method
In recent years, image forgery has become an important issue with the use of images in many important areas. Several self-embedding fragile...

-
A double-embedding hidden image encryption and authentication scheme based on compressed sensing and double random phase encoding
The image may be maliciously tampered when transmitted on the shared platform, and the receiver cannot determine whether the received image is a true...

-
Binary Wavelet Transform-Based Financial Text Image Authentication Algorithm
AbstractThis paper presents a novel financial text image security authentication algorithm based on binary wavelet transform. Initially, the...

-
A secure DWT-based dual watermarking scheme for image authentication and copyright protection
Digital watermarking mechanisms have become an essential tool for guaranteeing copyright protection and content authentication. However, most...

-
Nonlinear image authentication algorithm based on double fractional Mellin domain
In this paper, we propose a novel dual-user image authentication algorithm based on the double fractional Mellin transform. We perform a security...

-
A novel strict color image authentication scheme based on dual-complex LU decomposition
In this paper, we construct the dual-complex Gauss transformation and propose novel algorithms for LU decomposition and partial pivoting LU...

-
Integer wavelet transform based watermarking scheme for medical image authentication
In this work, a blind watermarking scheme has been proposed for medical image authentication. The scheme can embed patients’ records in digital...
-
A secure secret image sharing with steganography and authentication by Hamming code (15,11) for compressed images
The impressive increase in the rate of image transmission via internet has, more than ever, highlighted the importance of image securing techniques....

-
Multiple image watermarking with dual authentication for smart and safe city environment
The drastic advancement in medical data volume is a big concern for researchers to prevent it from forgery. The presented dual image watermarking...

-
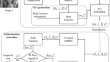
An effective compressed image authentication scheme based on N-variant AMBTC
Image authentication is one technique that provides integrity protection for digital images, making them sensitive to any slight modification....
-
LWT-DCT based image hashing for image authentication via blind geometric correction
Image authentication based on robust image hashing has been paid large attention by researchers. However, most of the existing methods are unable to...

-
Real-time and secure identity authentication transmission mechanism for artificial intelligence generated image content
The rapid development of generative artificial intelligence technology and large-scale pre-training models has led to the emergence of artificial...

-
A comprehensive survey on image authentication for tamper detection with localization
The data that is stored or transmitted in digital form is susceptible to be attacked. Digital images are particularly vulnerable to unauthorized...

