Search
Search Results
-
Deep contrastive multi-view clustering with doubly enhanced commonality
Recently, deep multi-view clustering leveraging autoencoders has garnered significant attention due to its ability to simultaneously enhance feature...
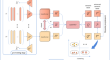
-
Expediting the design and development of secure cloud-based mobile apps
The adoption and popularity of mobile devices by end-users is partially driven by the increasing development and availability of mobile applications...

-
Quality evaluation methods of handwritten Chinese characters: a comprehensive survey
Quality evaluation of handwritten Chinese characters aims to automatically quantify and assess handwritten Chinese characters through computer vision...

-
Some self-dual codes and isodual codes constructed by matrix product codes
In 2020, Cao et al. proved that any repeated-root constacyclic code is monomially equivalent to a matrix product code of simple-root constacyclic...
-
FEF-Net: feature enhanced fusion network with crossmodal attention for multimodal humor prediction
Humor segment prediction in video involves the comprehension and analysis of humor. Traditional humor prediction has been text-based; however, with...
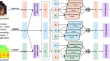
-
A channel-gained single-model network with variable rate for multispectral image compression in UAV air-to-ground remote sensing
Unmanned aerial vehicle (UAV) air-to-ground remote sensing technology, has the advantages of long flight duration, real-time image transmission, wide...

-
Some constacyclic BCH codes with good parameters
BCH codes as a subclass of constacyclic BCH codes have been widely studied, while the results on the parameters of BCH codes over finite fields are...
-
Multi-party codebook distribution strategy based on secret sharing
The paper addresses the issue of secure distribution of codebooks in the field of information security, particularly in the domain of covert...

-
Gaming the system: tetromino-based covert channel and its impact on mobile security
Trojan droppers consistently emerge as challenging malware threats, particularly within the Android ecosystem. Traditional malware detection...

-
PointDMIG: a dynamic motion-informed graph neural network for 3D action recognition
Point cloud contains rich spatial information, providing effective supplementary clues for action recognition. Existing action recognition algorithms...
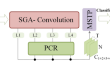
-
Security analysis of the ISO standard \(\textsf{OFB}\)-\(\textsf{DRBG}\)
Deterministic random bit generators (DRBGs) are essential tools in modern cryptography for generating secure and unpredictable random numbers. The...

-
A survey of compositional inverses of permutation polynomials over finite fields
In this paper, we survey on the recent results and methods in the study of compositional inverses of permutation polynomials over finite fields. In...
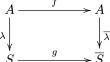
-
Constructions for t-designs and s-resolvable t-designs
The purpose of the present paper is to introduce recursive methods for constructing simple t -designs, s -resolvable t -designs, and large sets of t -desi...
-
Finding orientations of supersingular elliptic curves and quaternion orders
An oriented supersingular elliptic curve is a curve which is enhanced with the information of an endomorphism. Computing the full endomorphism ring...

-
DMFNet: deep matrix factorization network for image compressed sensing
Due to its outstanding performance in image processing, deep learning (DL) is successfully utilized in compressed sensing (CS) reconstruction....

-
Acnn: arbitrary trace attacks based on leakage area detection
Deep Learning-based Side-Channel Analysis (DL-SCA) has emerged as a powerful method in the field of side-channel analysis. Current works on DL-SCA...

-
Multi-branch feature fusion and refinement network for salient object detection
With the development of convolutional neural networks (CNNs), salient object detection methods have made great progress in performance. Most methods...

