Search
Search Results
-
Review of few-shot learning application in CSI human sensing
Wi-Fi sensing has garnered increasing interest for its significant advantages, primarily leveraging Wi-Fi signal fluctuations induced by human...

-
State-of-the-art review on the use of AI-enhanced computational mechanics in geotechnical engineering
Significant uncertainties can be found in the modelling of geotechnical materials. This can be attributed to the complex behaviour of soils and rocks...

-
Augmenting Cervical Cancer Analysis with Deep Learning Classification and Topography Selection Using Artificial Bee Colony Optimization
According to the research and study, cervical cancer has risen to develop the fourth most communal malignancy to strike women. Five different forms...

-
“Solar synergy: maximizing photovoltaic power with spotted hyena method in uniform and partial-shade environmental conditions”
A novel bioinspired Spotted-Hyena Method (SH) is proposed to track the maximum power point of partially shaded photovoltaic arrays. The SH algorithm...

-
Enhancing Forecasting Accuracy with a Moving Average-Integrated Hybrid ARIMA-LSTM Model
This research provides a time series forecasting model that is hybrid which combines Long Short-Term Memory (LSTM) and Autoregressive Integrated...
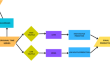
-
Performance of the pre-trained large language model GPT-4 on automated short answer grading
Automated Short Answer Grading (ASAG) has been an active area of machine-learning research for over a decade. It promises to let educators grade and...

-
Integration of facility manager in planning, design, and execution of construction projects
Construction projects typically progress through four primary phases, namely planning, design, implementation, and operation. This study discusses...

-
Improved V-detector algorithm based on bagging for earthquake prediction with faults
With the highly nonlinear relationship between various seismic feature indicators and earthquakes, the researchers can hardly construct an earthquake...

-
Evolution of Information Infrastructures in Healthcare as Convergence of Digital Trajectories
In information infrastructures at hospitals, various stakeholders are responsible for specific information and communications technology (ICT)...
-
Multimedia Educational System and its Improvement Using AI Model for a Higher Education Platform
In the world of technology today, the hardware, applications, and online computing service have transformed instructional approaches and classroom...

-
Graph foundation model
Graph Foundation Models represent an evolving direction in graph machine learning. Drawing inspiration from the success of Large Language Models in...
-
CT-MFENet: Context Transformer and Multi-Scale Feature Extraction Network via Global-Local Features Fusion for Retinal Vessels Segmentation
Segmentation of the retinal vessels in the fundus is crucial for diagnosing ocular diseases. Retinal vessel images often suffer from category...

-
Conversing with AI chatbots: examining what OpenAI ChatGPT-4, Microsoft Bing Chatbot, and google bard know, think they know, do not know, and would like to know about engineering
Over the past few weeks, chatbots have become increasingly popular, and these are likely to revolutionize our lives. While the most common three...
-
Robust consistency learning for facial expression recognition under label noise
Label noise is inevitable in facial expression recognition (FER) datasets, especially for datasets that collected by web crawling, crowd sourcing in...
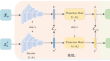
-
‘Worldview’ of the AIGC systems: stability, tendency and polarization
This study aims to investigate the worldview characteristics of current systems of artificial intelligence generated content (AIGC). Eight...

-
Optimizing U-Net CNN performance: a comparative study of noise filtering techniques for enhanced thermal image analysis
Infrared thermal imaging presents a promising avenue for detecting physiological phenomena such as hot flushes in animals, presenting a non-invasive...

-
Lattice-based device-to-device authentication and key exchange protocol for IoT system
Protecting IoT environments from the increasing number of cyber threats has grown more important as the number of Internet of Things (IoT) devices...

-
FedSHE: privacy preserving and efficient federated learning with adaptive segmented CKKS homomorphic encryption
Unprotected gradient exchange in federated learning (FL) systems may lead to gradient leakage-related attacks. CKKS is a promising approximate...

-
Business Unit Development: Vorteile und Herausforderungen für beteiligte Mitarbeiter
The ongoing shortage of skilled workers in the IT sector is a key challenge for companies and is hampering progress in the digital transformation. As...

