Search
Search Results
-

-
Why the use of domain-specific modeling in airworthy software requires new methods and how these might look like? (extended version)
The use of domain-specific modeling (DSM) in safety-critical avionics is rare, even though the ever-increasing complexity of avionics systems makes...

-
iDOCEM
In the business process lifecycle, models can be approached from two perspectives: on the one hand, models are used to create systems in the design...

-
A robust method for malware analysis using stacking classifiers and dendrogram visualization
Malware analysis is a vital and challenging task in the ever-changing cyber threat landscape. Traditional signature-based methods cannot keep up with...

-
Electromagnetic properties of coal using microstrip and an algorithm based on the Nicolson-Ross-Weir method
The work implements an experimental methodology to find the dielectric parameters: electrical permittivity, effective permittivity, magnetic...

-
Aggregating the response in time series lag models using quad weight kernel: impact of environmental factors on schizophrenia admissions
There has been a growing apprehension in the past few years concerning the issue of pollution and climate change. Several articles have shown the...

-
Requirements for modelling tools for teaching
Modelling is an important activity in software development and it is essential that students learn the relevant skills. Modelling relies on dedicated...

-
What you see is what you trace: a two-stage interview study on traceability practices and eye tracking potential
The benefits of traceability have widely been discussed in research. However, studies have also shown that traceability practices are still not...

-
Exploiting recurrent graph neural networks for suffix prediction in predictive monitoring
Predictive monitoring is a subfield of process mining that aims to predict how a running case will unfold in the future. One of its main challenges...

-
Deep learning-based classification and application test of multiple crop leaf diseases using transfer learning and the attention mechanism
Crop diseases are among the major natural disasters in agricultural production that seriously restrict the growth and development of crops,...

-
A splash of color: a dual dive into the effects of EVO on decision-making with goal models
Recent approaches have investigated assisting users in making early trade-off decisions when the future evolution of project elements is uncertain....

-
Optimizing pre-copy live virtual machine migration in cloud computing using machine learning-based prediction model
One of the preconditions for efficient cloud computing services is the continuous availability of services to clients. However, there are various...

-
Detecting mistakes in a domain model: a comparison of three approaches
Domain models are a fundamental part of software engineering, thus it is important for every software engineer to know the principles of domain...

-
CSSLnO: Cat Swarm Sea Lion Optimization-based deep learning for fake news detection from social media
Social media has effectively shortened the time for the distribution of information, which sometimes carry news when compared to traditional methods....

-
A fast verifiable fully homomorphic encryption technique for secret computation on cloud data
In the domain of cloud computing, safeguarding the confidentiality and integrity of outsourced sensitive data during computational processes is of...

-
A clarity and fairness aware framework for selecting workers in competitive crowdsourcing tasks
Crowdsourcing is a powerful technique for accomplishing tasks that are difficult for machines but easy for humans. However, ensuring the quality of...

-
Modelling the quantification of requirements technical debt
Requirements Technical Debt (RTD) applies the Technical Debt (TD) metaphor to capture the consequences of sub-optimal decisions made concerning...

-
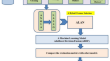
Integrated feature selection and ensemble learning for heart disease detection: a 2-tier approach with ALAN and ET-ABDF machine learning model
The findings of this investigation give a novel approach to the forecasting of heart disease. For the purpose of determining significant features, it...
-
“Solar synergy: maximizing photovoltaic power with spotted hyena method in uniform and partial-shade environmental conditions”
A novel bioinspired Spotted-Hyena Method (SH) is proposed to track the maximum power point of partially shaded photovoltaic arrays. The SH algorithm...

-
Lattice-based device-to-device authentication and key exchange protocol for IoT system
Protecting IoT environments from the increasing number of cyber threats has grown more important as the number of Internet of Things (IoT) devices...

