Search
Search Results
-
Secure communications based on sending-or-not-sending strategy
Recently, there are various schemes of quantum secure direct communications that have been studied. Most of these protocols commit themselves to...

-
Plug-and-play sending-or-not-sending twin-field quantum key distribution
Twin-field quantum key distribution (TF-QKD) is a new extraordinary QKD protocol, which can overcome the fundamental rate-distance limit without...

-
Finite-key analysis of sending-or-not-sending twin-field quantum key distribution with intensity fluctuations
Sending-or-not sending twin-field quantum key distribution (SNS TF-QKD) removes the remaining security loopholes in original TF-QKD and can tolerate...

-
1002 km twin-field quantum key distribution with finite-key analysis
Quantum key distribution (QKD) holds the potential to establish secure keys over long distances. The distance of point-to-point QKD secure key...

-
Fast nuclear-spin gates and electrons-nuclei entanglement of neutral atoms in weak magnetic fields
We present a novel class of Rydberg-mediated nuclear-spin entanglement in divalent atoms with global laser pulses. First, we show a fast nuclear-spin...

-
Twin-field quantum key distribution over a 511 km optical fibre linking two distant metropolitan areas
The basic principle of quantum mechanics
1 guarantees the unconditional security of quantum key distribution (QKD)2 –6 at the cost of forbidding the...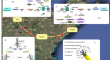
-
Genuine quantum networks with superposed tasks and addressing
We show how to make quantum networks, both standard and entanglement-based, genuine quantum by providing them with the possibility of handling...

-
Need for Cybersecurity Solutions in IoT Systems
People are living in the world where billions of IoT systems are connected to the Internet. They are sending and receiving data via network, and are...
-
Optimized protocol for twin-field quantum key distribution
Twin-field quantum key distribution (TF-QKD) and its variant protocols are highly attractive due to the advantage of overcoming the rate-loss limit...

-
SPD On-Line Filter: Workflow and Data Management Systems
AbstractThis article presents a microservice architecture and the first prototypes of the data and workflow management systems included in the “SPD...

-
Investigation of the Optimal Parameters of the Distributed Fiber Microphone Circuit Based on φ-OTDR for Speech Recognition
AbstractA study of the optimal parameters of a distributed fiber microphone circuit based on a laboratory setup of a phase-sensitive optical...
-
A QTCP/IP reference model for partially trusted-node-based quantum-key-distribution-secured optical networks
Classical encryption protocols that are currently used to secure the internet and transmission control protocol/internet protocol (TCP/IP) protocols...

-

-
AI-enhanced security demand and routing management for MANETs with optical technologies
The proliferation of Mobile Ad hoc Networks (MANETs), where nodes connect with one another to offer the required real-time entertainment services, is...

-
Design and Implementations of Pigeon’s Away Electronic System
The birds (pigeons) are greatest gift to mankind. Pigeons have been used for sending messages to loved ones. These birds are found living with human...

-
Surpassing the repeaterless bound with a photon-number encoded measurement-device-independent quantum key distribution protocol
Decoherence is detrimental to quantum key distribution (QKD) over large distances. One of the proposed solutions is to use quantum repeaters, which...

-
Improved security bounds against the Trojan-horse attack in decoy-state quantum key distribution
In a quantum Trojan-horse attack (THA), eavesdroppers learn encoded information by injecting bright light into encoded or decoded devices of quantum...

-
Rational quantum secret sharing scheme based on GHZ state
In this paper, a new rational quantum secret sharing scheme based on GHZ state is proposed. It realizes the secret sharing among n agents by encoding...

-
Parametric Optimization on HPC Clusters with Geneva
Many challenges of today’s science are parametric optimization problems that are extremely complex and computationally intensive to calculate. At the...

-
A visually secure image encryption scheme based on compressed sensing and Chebyshev-dynamics coupled map lattices in cloud environment
In this paper, a new spatiotemporal chaotic system based on Chebyshev-dynamically coupled map lattice (CDCML) is proposed. Various performance tests...

