Search
Search Results
-
Symmetric key and polynomial-based key generation mechanism for secured data communications in 5G networks
Fifth Generation (5G) networks provide data communications through various latest technologies including Software Defined Networks (SDN), Artificial...

-
A Highly Consistent and High-speed Physical Layer Key Generation Scheme
There are some problems that the bit error rate is high but generation rate is low in existing physical layer secret key generation schemes, so we...

-
A High Consistency Wireless Key Generation Scheme for Vehicular Communication Based on Wiener Filter Extrapolation
Secret key generation from wireless channel is an emerging technology for communication network security, which exploits the reciprocity and time...
-
Power Allocation under Given Secret Key Generation Rate for Secure Wireless OFDM Systems
AbstractGenerating a secret key from the physical layer is one of the most challenging topics in cryptography. Secret key generation rate (SKGR) and...

-
Efficient Key Generation Techniques for Wireless Body Area Network
In wireless body area network health care applications, energy-constraint wearable devices are used to monitor patient physiological parameters. The...

-
A powerful adversary model and corresponding OTP time slot allocation scheme in RIS-assisted physical layer key generation
Physical layer key generation (PLKG) is a technique of information-theoretic security to tackle the problem of key distribution between...

-
Simple, secure and lightweight authentication protocol with session-key generation for IIoT device in IIoT networks
Device authentication is essential for protecting IIoT networks due to the industrial internet of things (IIoT) rise in connected devices. This work...

-
Comparative research on block design-based protocol and blowfish for secured key generation and data sharing on cloud
Confidentiality of maintaining the Electronic Health Records of patients is a major concern to both the patient and Doctor. Sharing the data on cloud...

-
Generation of high-order random key matrix for Hill Cipher encryption using the modular multiplicative inverse of triangular matrices
Hill Cipher is one of the classic symmetric encryption algorithms widely used in cloud data security. Although the hill cipher principle is...

-
Fingerprint-Based Asymmetric Bio-Cryptographic Key Generation Using Convolution Network
The asymmetric cryptography techniques use in the field of data security suffer from the challenge of maintaining the private key as secret. As a...
-
An Improvised Algorithm for a Dynamic Key Generation Model
Data may be kept private, secure, and authentic via cryptography. Computational resources and communication channel performance impede the...
-
Evaluation of cryptographic key generation performance using evolutionary algorithm
The process of key generation is at the heart of each cryptography method’s encryption and decryption. As a result, it is necessary to make the key...

-
Unveiling the energy consumption-food waste nexus in households: A focus on key predictors of food waste generation
In most cities worldwide, household food waste constitutes a significant portion of municipal solid waste (MSW). However, its management often proves...

-
Two-factor-based RSA key generation from fingerprint biometrics and password for secure communication
In an asymmetric-key cryptosystem, the secure storage of private keys is a challenging task. This paper proposes a novel approach for generating the...

-
An Enhancement in Crypto Key Generation Using Image Features with CRT
Strong cryptographic algorithms are the main sources for building security systems. However, providing security depends on the secret information...
-
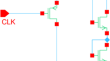
Area and Power Efficient AVLS-TSPC-Based Diffused Bit Generator for Key Generation
The diffused bit generator (DBG) is an entropy generator that generates a stream of random bits. DBG is realized using a linear feedback shift...
-
Concurring of Neural Machines for Robust Session Key Generation and Validation in Telecare Health System During COVID-19 Pandemic
In this technique, it has been proposed to agree the session keys that have been generated through dual artificial neural networks based on the...

-
Research on Key Technologies of New Generation Vehicle Wireless Network
With the continuous improvement of automobile intelligence, the delay, synchronization, reliability, security and concurrency of on-board network are...
-
Securing Communication in IoT Environment Using Lightweight Key Generation-Assisted Homomorphic Authenticated Encryption
Cryptographic key establishment is an essential component between any pairwise resource-constrained sensor nodes inside an Internet of Things (IoT)...
-
Optimizing the Key-Pair Generation Phase of McEliece Cryptosystem
Quantum computers are no longer ideas but concrete devices. They could represent a threat for public key cryptography; therefore, in 2017 NIST...
