Search
Search Results
-
A systematic map** study on security for systems of systems
In the late twentieth century, the term “System of Systems” (SoS) became popular to describe a complex system made up of a combination of independent...

-
Speech emotion recognition systems and their security aspects
Speech emotion recognition (SER) systems leverage information derived from sound waves produced by humans to identify the concealed emotions in...

-
Framework for Modeling Security Policies of Big Data Processing Systems
AbstractThis paper studies automatizing the analysis of access control in big data management systems by modeling security policies. It analyzes...

-
On the Security of Smart Home Systems: A Survey
Among the plethora of IoT (Internet of Things) applications, the smart home is one of the fastest-growing. However, the rapid development of the...
-
A security framework for mobile agent systems
Security is a very important challenge in mobile agent systems due to the strong dependence of agents on the platform and vice versa. According to...

-
An artificial intelligence lightweight blockchain security model for security and privacy in IIoT systems
The Industrial Internet of Things (IIoT) promises to deliver innovative business models across multiple domains by providing ubiquitous connectivity,...

-
A Model-Based Systems Engineering Plugin for Cloud Security Architecture Design
Security is one of the biggest concerns for cloud infrastructures. Cloud infrastructures are susceptible to a wide range of threats, including...

-
Improving the Efficiency of Multiagent Information Security Systems by Post-Quantum Cryptography Methods
AbstractThe information security problems for open multiagent systems using access control schemes based on RSA algorithm are analyzed. It is shown...

-
Cloud data security for distributed embedded systems using machine learning and cryptography
In the growing demand for distributed embedded systems that efficiently execute complex processes and high-end applications, safeguarding sensitive...

-
Methodological Approach to Construct Models for Predicting Indicators of Properties of Information Security Systems
AbstractA methodological approach to construct models for predicting indicators of properties of information security systems at evolutionary stages...
-
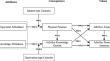
Exploring the role of gamified information security education systems on information security awareness and protection behavioral intention
This study examines the effect of a gamified information security education system (ISES) on develo** users’ information security awareness and...
-
Security establishment using deep convolutional network model in cyber-physical systems
This study develops an active security control strategy for Cyber-Physical Systems (CPSs) that are subject to attacks known as Denial-of-Service...

-
Post-quantum security design for hierarchical healthcare systems based on lattices
The need for high-quality healthcare services increases to more incredible speeds. Smart healthcare offers an ecosystem of IoT wireless networks,...

-
Maritime decision-makers and cyber security: deck officers’ perception of cyber risks towards IT and OT systems
Through a quantitative study of deck officers’ cyber risk perceptions towards information (IT) and operational (OT) systems, this paper contributes...

-
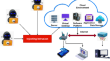
A bizarre synthesized cascaded optimized predictor (BizSCOP) model for enhancing security in cloud systems
Due to growing network data dissemination in cloud, the elasticity, pay as you go options, globally accessible facilities, and security of networks...
-
Increasing Physical Layer Security Through Hyperchaos in VLC Systems
Visible light communication (VLC) systems have relatively higher security compared with traditional radio frequency (RF) channels due to...

-
Security Algorithm for Intelligent Transport System in Cyber-Physical Systems Perceptive: Attacks, Vulnerabilities, and Countermeasures
Upcoming technological innovations and findings are immense in the field of intelligent transport systems (ITS). Cyber-physical systems (CPSs) are...

-
Recommendation-based trust computation and rating prediction model for security enhancement in cloud computing systems
The cloud service providers need to deliver cloud services based on the service level agreement to their users. The services must be secure and...

-
Dependency-based security risk assessment for cyber-physical systems
A cyber-physical attack is a security breach in cyber space that impacts on the physical environment. The number and diversity of such attacks...

-
Who is controlling whom? Reframing “meaningful human control” of AI systems in security
Decisions in security contexts, including armed conflict, law enforcement, and disaster relief, often need to be taken under circumstances of limited...

