Search
Search Results
-
Are Micro-Credentials Valuable for Students? Perspective on Verifiable Digital Credentials
Higher education institutions are investing more and investigating digital credentials as proof of learning upon completion of learning offerings,...
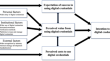
-
Novel blockchain-based framework to publish, verify, and store digital academic credentials of universities
Blockchain is the technology of choice to create cryptocurrency and bitcoins through the maintenance of immutable distributed ledgers in multiple...

-
Blockchain-cloud privacy-enhanced distributed industrial data trading based on verifiable credentials
Industrial data trading can considerably enhance the economic and social value of abundant data resources. However, traditional data trading models...

-
Micro-credentials in leveraging emergency remote teaching: the relationship between novice users’ insights and identity in Malaysia
Micro-credentials have gained much popularity in recent years, and their popularity has skyrocketed due to emergency remote teaching instigated by...

-
A systematic review of the opportunities and challenges of micro-credentials for multiple stakeholders: learners, employers, higher education institutions and government
Micro-credentials are gaining traction as viable vehicles for rapid upskilling of the workforce in the twenty-first century and potential pathways...

-
Privacy-Preserving Post-quantum Credentials for Digital Payments
Digital payments and decentralized systems enable new financial products and services for users. A core challenge stems from the need to protect...
-
Toward just and equitable micro-credentials: an Australian perspective
The current historic COVID-19 Pandemic moment has thrown into sharp relief the need for flexible and rigorous higher education that meets upskilling...
-
SoK: Anonymous Credentials
Anonymous credentials are a powerful tool for making assertions about identity while maintaining privacy and have been the subject of study for many...
-
Distributed access control for information-centric networking architectures using verifiable credentials
Information-Centric Networking (ICN) is an emerging paradigm that allows users to retrieve content items securely, independently of their location....

-
Alternative Digital Credentials—UAE’s First Adopters’ Quality Assurance Model and Case Study
As the leading applied higher education institution in the United Arab Emirates, the Higher Colleges of Technology is engaging Alternative Digital...
-
Implementation of micro-credentials in higher education: A systematic literature review
Micro-credential (MC) is an innovative and disruptive technology-based learning model. In higher education (HE), MCs are typically certified in the...

-

-
Selective Delegation of Attributes in Mercurial Signature Credentials
Anonymous credential schemes enable service providers to verify information that a credential holder willingly discloses, without needing any further...
-
Privacy-Preserving Educational Credentials Management Based on Decentralized Identity and Zero-Knowledge Proof
Educational credentials are an important part of the education ecosystem. However, these credentials often exist in the form of traditional paper...
-
Unlinkable Delegation of WebAuthn Credentials
The W3C’s WebAuthn standard employs digital signatures to offer phishing protection and unlinkability on the web using authenticators which manage...
-
Blockchain in E-Learning Platform to Enhance Trustworthy and Sharing of Micro-credentials
Blockchain is a disruptive technology and interest in its adoption is growing across many market sectors in Industry 4.0. However, the blockchain...
-
Towards Smart Contract-Based Verification of Anonymous Credentials
Smart contracts often need to verify identity-related information of their users. However, such information is typically confidential, and its...
-
Auditable Attribute-Based Credentials Scheme and Its Application in Contact Tracing
During the pandemic, the limited functionality of existing privacy-preserving contact tracing systems highlights the need for new designs. Wang et...
-
When the push and pull factors in digital educational resources backfire: the role of digital leader in digital educational resources usage
The study investigated the impact of digital leadership on teachers’ usage of digital educational resources (DERs). The study collected data from...

