Search
Search Results
-
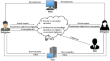
Searchable Attribute-Based Proxy Re-encryption: Keyword Privacy, Verifiable Expressive Search, and Outsourced Decryption
In this paper, we address the open problem posed by Ge et al. in 2020, which was to design a new attribute-based proxy re-encryption with keyword...
-
Cloud-decryption-assisted image compression and encryption based on compressed sensing
In this paper, we propose a new image compression and encryption scheme (ICES) based on compressed sensing (CS) and double random phase encoding...

-
Short Paper: Verifiable Decryption for BGV
In this work we present a direct construction for verifiable decryption for the BGV encryption scheme by combining existing zero-knowledge proofs for...
-
Efficient lattice-based revocable attribute-based encryption against decryption key exposure for cloud file sharing
Cloud file sharing (CFS) has become one of the important tools for enterprises to reduce technology operating costs and improve their...

-
Automated decryption of siri bhoovalaya using cryptography and natural language processing techniques
"The Siri Bhoovalaya is a seminal work of literature, believed to have been composed approximately a millennium ago, which encompasses diverse...

-
Decryption and Password Cracking
In modern computing in general, and in forensic examinationsExamination in particular, encrypted data is common. Traditionally, this has been because...
-
Payable Outsourced Decryption for Functional Encryption Using BlockChain
In many new implementations that needs data storage and exchange (such as cloud storage services), the notion of Functional Encryption...
-
Server-Supported Decryption for Mobile Devices
We propose a threshold encryption scheme with two-party decryption, where one of the keyshares may be stored and used in a device that is able to...
-
Blind Decryption and Private Information Delivery
We analyze the privacy protection scheme given by Bao, Deng and Feng which is a cryptographic protocol similar to oblivious transfer and private...
-
PrimeSwitch—Encryption and Decryption Algorithm Using RSA Key Generation
This paper proposes an encryption and decryption algorithm PrimeSwitch that secures data using a key generated using RSA Method. It provides...
-
Verifiable Decryption in the Head
In this work we present a new approach to verifiable decryption which converts a 2-party passively secure distributed decryption protocol into a...
-
Modified Playfair for Text File Encryption and Meticulous Decryption with Arbitrary Fillers by Septenary Quadrate Pattern
Cryptography secures data and serves to ensure the confidentiality of records. Playfair is a cryptographic symmetrical algorithm that encrypts...

-
Indistinguishable Obfuscated Encryption and Decryption Based on Transformer Model
To solve the problem in secure encryption in cryptography, indistinguishability Obfuscation (iO) was born. It is a crypto-complete idea, based on...
-
Complex entropy based encryption and decryption technique for securing medical images
During medical picture transmission, the most pressing concern is security. Medical images must be encrypted since they are extremely sensitive....

-
On Active Attack Detection in Messaging with Immediate Decryption
The widely used Signal protocol provides protection against state exposure attacks through forward security (protecting past messages) and...
-
Cryptanalysis of RSA with composed decryption exponent with few most significant bits of one of the primes
RSA is well known public-key cryptosystem in modern-day cryptography. Since the inception of the RSA, several attacks have been proposed on RSA. The...
-
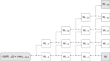
Automatic Detection and Decryption of AES Using Dynamic Analysis
In this paper we propose a set of algorithms that can automatically detect the use of AES and automatically recover both the encryption key and the...
-
Exploring Decryption Failures of BIKE: New Class of Weak Keys and Key Recovery Attacks
Code-based cryptography has received a lot of attention recently because it is considered secure under quantum computing. Among them, the QC-MDPC...
-
Encryption and Decryption Algorithms for Plain Text and Images using Fractional Calculus
This book offers an alternative for encrypting and decrypting messages using objects called integer and fractional-order estimators or observers, by...

-
On Secure Ratcheting with Immediate Decryption
Ratcheting protocols let parties securely exchange messages in environments in which state exposure attacks are anticipated. While, unavoidably, some...
