Search
Search Results
-
Data-driven approaches and model-based methods for detecting and locating leaks in water distribution systems: a literature review
Water distribution systems are made up of interconnected components that should allow water systems to meet demand, but leaks can waste enough water...

-
Analyzing Memory Leaks
Before we discuss memory leaks, let’s analyze a simple case study. It will help you understand how memory leaks can hamper the smooth execution of an...
-
Case Study: Resource Leaks
In this chapter, you will use the pattern approach to diagnose and debug a common problem type in the Windows operating system: resource leaks.
-
From Whistle to Echo: Data Leaks in Web-Based Whistleblowing Channels
Whistleblowing refers to reporting misconduct to responsible authorities. With accelerating digitalization and the European Union’s new whistleblower...
-
Detecting Illicit Data Leaks on Android Smartphones Using an Artificial Intelligence Models
In today’s digital landscape, hackers and espionage agents are increasingly targeting Android, the world’s most prevalent mobile operating system. We...
-
Automatic and Incremental Repair for Speculative Information Leaks
We present CureSpec, the first model-checking based framework for automatic repair of programs with respect to information leaks in the presence of...
-
Time Will Tell: Exploiting Timing Leaks Using HTTP Response Headers
To execute timing attacks, an attacker has to collect a large number of samples to overcome network jitter. Methods to reduce such jitter, which is a...
-
Detecting Privacy Leaks Utilizing Digital Forensics and Reverse Engineering Methodologies
Most commercial iOS forensics and data acquisition tools will effectively do the job in general, but in cases of data leaks presented, we need to...
-
Frequency-Domain Generalized Phase Transform Method in Pipeline Leaks Locating
This article considers the problem of instrumental-assisted determination of the location of leaks in water pipes using acoustic correlation leak...
-
Quantitative estimation of side-channel leaks with neural networks
Information leaks via side channels remain a challenging problem to guarantee confidentiality. Static analysis is a prevalent approach for detecting...

-
Listening Between the Bits: Privacy Leaks in Audio Fingerprints
Audio content recognition is an emerging technology that forms the basis for mobile services, such as automatic song recognition, second-screen...
-
Data in Transit Security
Data in transit, or network traffic, can be eavesdropped on and potentially leak sensitive information. This information can be in the payload,...
-
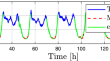
Leak detection and localization in water distribution networks by combining expert knowledge and data-driven models
Leaks represent one of the most relevant faults in water distribution networks (WDN), resulting in severe losses. Despite the growing research...
-
Data Protection and Data Privacy
In this chapter, we specify the business requirements and propose the solution concept for data protection and data privacy. ERP systems must fulfill...
-
Analysis of Information Quality and Data Security in the KPU (General Elections Commission) SIDALIH (Voter Data Information System) Application
The purpose of this study was to determine the quality of services provided and data security in the use of the KPU’s SIDALIH (Voter Data Information...
-
Data Management
The speed and accuracyAccuracy of data management are essential advantages offered by AIArtificial Intelligence (AI) systems. A further advantage...
-
FD-Leaks: Membership Inference Attacks Against Federated Distillation Learning
With the enhanced sensing and computing power of mobile devices, emerging technologies and applications generate massive amounts of data at the edge...
-
An Empirical Study on Mobile Payment Credential Leaks and Their Exploits
Recently, mobile apps increasingly integrate with payment services, enabling the user to pay orders with a third-party payment service provider,...
-
Incorporating Physics-Based Models into Data Driven Approaches for Air Leak Detection in City Buses
In this work-in-progress paper two types of physics-based models, for accessing elastic and non-elastic air leakage processes, were evaluated and...
-
Image-based random rotation for preserving the data in data mining process
The privacy and security of big data have become a major concern in recent years, necessitating privacy-preserving data mining strategies to preserve...

