Search
Search Results
-
Restricted near collision attack on Plantlet
Plantlet is a recent lightweight stream cipher designed by Mikhalev, Armknecht and Müller in IACR ToSC 2017. This design paradigm receives attention...
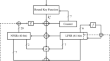
-
Near Collision Attack Against Grain V1
A near collision attack against the Grain v1 stream cipher was proposed by Zhang et al. in Eurocrypt 18. The attack uses the fact that two internal...
-
High-Order Collision Attack Vulnerabilities in Montgomery Ladder Implementations of RSA
This paper describes a straightforward methodology which allows mounting a specific kind of single-trace attacks called collision attacks. We first...
-
ARGo: augmented reality-based mobile Go stone collision game
In this study, we present a mobile Go stone collision game based on augmented reality, which we call ARGo, inspired by the traditional Korean board...

-
New Records in Collision Attacks on SHA-2
The SHA-2 family including SHA-224, SHA-256, SHA-384, SHA-512, SHA-512/224 and SHA512/256 is a U.S. federal standard published by NIST. Especially,...
-
Collision-Based Attacks on White-Box Implementations of the AES Block Cipher
Since Chow et al. introduced white-box cryptography with a white-box implementation of the AES block cipher in 2002, a few attacks and improvements...
-
Collision Attacks on Round-Reduced SHA-3 Using Conditional Internal Differentials
The KECCAK hash function was selected by NIST as the winner of the $$\texttt...
-
Same Values Analysis Attack on Weierstrass Binary Elliptic Curves
Public key Crystosystems based on Elliptic Curves are increasingly recommended, due to their small key size. However, they are vulnerable to a type...
-
VANET Cluster Based Gray Hole Attack Detection and Prevention
VANET is an emerging technology for intelligent transportation systems in smart cities. Vehicle communication raises many challenges, notably in the...

-
Bringing Order to Chaos: The Case of Collision-Resistant Chameleon-Hashes
Chameleon-hash functions, introduced by Krawczyk and Rabin (NDSS’00), are trapdoor collision-resistant hash functions parametrized by a public key....

-
Multimodal Biometric Fusion Algorithm Based on Ranking Partition Collision Theory
Score-based multimodal biometric fusion has been shown to be successful in addressing the problem of unimodal techniques’ vulnerability to attack and...
-
The NISQ Complexity of Collision Finding
Collision-resistant hashing, a fundamental primitive in modern cryptography, ensures that there is no efficient way to find distinct inputs that...
-
Collision Detection Method Based on Improved Whale Optimization Algorithm
Collision detection is an important problem in the field of computer graphics. In order to achieve efficient collision detection in large-scale...
-
Evicting and filling attack for linking multiple network addresses of Bitcoin nodes
Bitcoin is a decentralized P2P cryptocurrency. It supports users to use pseudonyms instead of network addresses to send and receive transactions at...

-
Automated Meet-in-the-Middle Attack Goes to Feistel
Feistel network and its generalizations (GFN) are another important building blocks for constructing hash functions, e.g., Simpira v2, Areion, and...
-
Guide to develo** case-based attack scenarios and establishing defense strategies for cybersecurity exercise in ICS environment
Critical infrastructure mainly performs its role through an industrial control system (ICS). Organizations conduct cyber exercises between red and...

-
Collision Provenance Using Decentralized Ledger
The coverage and communication lag has been worked on in swarms of drones with different formation patterns, however; decentralization of the...
-
Intelligent blockchain based attack detection framework for cross-chain transaction
The online trading market has been greatly improved by the significance of Cross-Chain (CC) transactions. However, malicious events are the chief...

-
Analysis of RIPEMD-160: New Collision Attacks and Finding Characteristics with MILP
The hash function RIPEMD-160 is an ISO/IEC standard and is being used to generate the bitcoin address together with SHA-256. Despite the fact that...
-
Meet-in-the-middle attack with splice-and-cut technique and a general automatic framework
Computer aided cryptanalysis has been popular for recent several years, however, most of these automations are semi-automations which leave...

