Search
Search Results
-
Fault-tolerant and error-correcting 4-bit S-boxes for cryptography applications with multiple errors detection
In this paper, fault-tolerant and error-correcting 4-bit S-boxes for cryptography applications with multiple error detection and correction are...

-
An analysis and evaluation of lightweight hash functions for blockchain-based IoT devices
Blockchain is among the most promising new technologies due to its unique features, encompassing security, privacy, data integrity, and immutability....

-
Tight Preimage Resistance of the Sponge Construction
The cryptographic sponge is a popular method for hash function design. The construction is in the ideal permutation model proven to be...
-
Simplified MITM Modeling for Permutations: New (Quantum) Attacks
Meet-in-the-middle (MITM) is a general paradigm where internal states are computed along two independent paths (‘forwards’ and ‘backwards’) that are...
-
HVH: A Lightweight Hash Function Based on Dual Pseudo-Random Transformation
Along with the popularization of RFID technology and wireless sensor network, it has been more and more difficult for common hash-functions to meet...
-
The Theory and Practice of Magic Hash Based Attacks on Lightweight Cryptographic Hash Functions in Complex IoT Environments
In this paper a new type of application layer attack against complex IoT environments is presented which is based on unsafe typecasting and loose...
-
Statistical Tests for Symmetric Primitives
In this work, we show the results of the NIST statistical tests performed on different datasets generated from the output of all possible...
-
High throughput acceleration of NIST lightweight authenticated encryption schemes on GPU platform
Authenticated encryption with associated data (AEAD) has become prominent over time because it offers authenticity and confidentiality...

-
Resource-Aware Cryptography: An Analysis of Lightweight Cryptographic Primitives
With the increased use of highly constrained interconnected devices in various areas like healthcare, sensor networks, the internet of things (IoT),...

-
Blind Side Channel Analysis on the Elephant LFSR Extended Version
The National Institute of Standards and Technology (NIST) started a competition for lightweight cryptography candidates for authenticated encryption....
-
Homomorphic Evaluation of Lightweight Cipher Boolean Circuits
Motivated by a number of applications of lightweight ciphers in privacy-enhancing cryptography (PEC) techniques such as secure multiparty computation...
-
Modeling, hardware architecture, and performance analyses of an AEAD-based lightweight cipher
Ensuring data security and integrity is crucial for achieving the highest level of protection and performance in modern cyber-physical systems (CPS)....

-
Blind Side Channel Analysis Against AEAD with a Belief Propagation Approach
This paper present two new attacks on two lightweight authenticated encryption with associated data (AEAD): Sparkle and...
-
Lightweight micro-architecture for IoT & FPGA security
Cryptographic standards were created with the goal of being able to work on a wide range of systems. Small computing systems with limited capacity to...
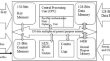
-
FSR-SPD: an efficient chaotic multi-image encryption system based on flip-shift-rotate synchronous-permutation-diffusion operation
Images are a crucial component in contemporary data transmission. Numerous images are transmitted daily through the open-source network. This paper...

-
Practical Homomorphic Evaluation of Block-Cipher-Based Hash Functions with Applications
Fully homomorphic encryption (FHE) is a powerful cryptographic technique allowing to perform computation directly over encrypted data. Motivated by...
-
Thinking Outside the Superbox
Designing a block cipher or cryptographic permutation can be approached in many different ways. One such approach, popularized by AES, consists in...
-
Authenticated Encryption Based on Lesamnta-LW Hashing Mode
Authenticated encryption refers to symmetric cryptography providing both privacy and authenticity. It is most common to construct it as a...
-
Modified lightweight cryptography scheme and its applications in IoT environment
Interconnected devices have been with us for a long time. The security of the data exchanged through these devices is a matter of grave concern....

-
Breaking LWC candidates: sESTATE and Elephant in quantum setting
The competition for lightweight cryptography (LWC) launched by the National Institute of Standards and Technology (NIST) is an ongoing project...

