Search
Search Results
-
Resource allocation for UAV-enabled multi-access edge computing
In Ultrareliable and Low Latency Communications (URLLC), balancing trade-offs between energy consumption, service availability, and strict...

-
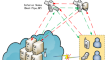
Dynamic game based task offloading and resource pricing in LEO-multi-access edge computing
Driven by the demand for ubiquitous connection in the Internet of everything era, this paper introduces a new low earth orbit (LEO) satellite-based...
-
Resource Allocation Using Deep Deterministic Policy Gradient-Based Federated Learning for Multi-Access Edge Computing
The study focuses on utilizing the computational resources present in vehicles to enhance the performance of multi-access edge computing (MEC)...
-
Session-Based Resource Access
This segment describes how web site keep uses logged in between requests by sending session IDs or access tokens. It also explains the advantages of...
-
Priority-based concurrency and shared resource access mechanisms for nested intercomponent requests in CAmkES
Component-based design encapsulates and isolates state and the operations on it, but timing semantics cross-cut these boundaries when a real-time...

-
Radio Resource Management of WLAN Hotspot Access Points in Next Generation Wireless Networks
The proliferation of the IEEE wireless local area network (WLAN), due to its flexibility, mobility, and support for billions of smart mobile devices,...

-
Using the ACE framework to enforce access and usage control with notifications of revoked access rights
The standard ACE framework provides authentication and authorization mechanisms similar to those of the standard OAuth 2.0 framework, but it is...

-
Resource management and switch migration in SDN-based multi-access edge computing environments
As the growing of data volumes due to the successive development of new mobile devices and the creation of new applications, the emergence of...

-
Joint uplink and downlink resource allocation for low-latency mobile virtual reality delivery in fog radio access networks
Fog radio access networks (F-RANs), in which the fog access points are equipped with communication, caching, and computing functionalities, have been...
-
Joint energy and latency-sensitive computation and communication resource allocation for multi-access edge computing in a two-tier 5G HetNet
Multi-access edge computing (MEC) and heterogeneous networks (HetNets) are two significant separately perceptible but complementary innovations....

-
Model division multiple access for semantic communications
In a multi-user system, system resources should be allocated to different users. In traditional communication systems, system resources generally...
-
User-trust centric lightweight access control for smart IoT crowd sensing applications in healthcare systems
The Internet of Things (IoT) enables healthcare systems to handle emergencies, where multiple authorities interact to perform tasks. Prevention of...

-
Access Control and Authorization
Access control is a process to determine “Who does what to what,” based on a policy. One of the system administrator’s biggest problems, which can...
-
MOOCs as a massive learning resource for a Higher Education Community. The Universitat Politècnica de València experience using the EdX remote access program
During the 2020 COVID-19 lockdown, edX launched an initiative, called the Remote Access Program, to give access to free certificates for its Massive...

-
Adaptive context-aware access control for IoT environments leveraging fog computing
The increasing use of the Internet of Things (IoT) has driven the demand for enhanced and robust access control methods to protect resources from...

-
Resource Allocation in Massive Non-Orthogonal Multiple Access System
With the popularity of large-scale communication scenarios, massive multiple access technology has attracted academic attention. In this paper, a...
-
End-to-end slicing of RAN based on next-generation optical access network
Given their widespread use, optical access networks are suitable as a practical infrastructure for mobile networks and services. The diverse range of...

-
Non-orthogonal multiple access-based MEC for energy-efficient task offloading in e-commerce systems
Mobile edge computing (MEC) reduces the latency for end users to access applications deployed at the edge by offloading tasks to the edge. With the...

-
Enhancing resource utilization and privacy in IoT data placement through fuzzy logic and PSO optimization
The exponential growth of Internet of Things (IoT) devices has ushered in an era of vast data generation, necessitating abundant resources for data...

-
A heterogeneous graph-based semi-supervised learning framework for access control decision-making
For modern information systems, robust access control mechanisms are vital in safeguarding data integrity and ensuring the entire system’s security....

