Search
Search Results
-
Hulls of cyclic codes with respect to the regular permutation inner product
In this paper, we introduce regular permutation inner products which contain the Euclidean inner product. And we generalize some properties of the...
-
Regular Memory Structures and Operation Domains of Intelligent Systems
AbstractThe concept of a regular memory area for an intelligent system (IS) is considered. The formalized description of the memory of a separate IS...

-
Special LCD codes from products of graphs
We examine the binary codes from the adjacency matrices of various products of graphs, and show that if the binary codes of a set of graphs have the...
-
Self-dual bent sequences for complex Hadamard matrices
A new notion of bent sequence related to Hadamard matrices was introduced recently, motivated by a security application (Solé et al. 2021). In this...

-
Properties of Lattice Isomorphism as a Cryptographic Group Action
In recent years, the Lattice Isomorphism Problem (LIP) has served as an underlying assumption to construct quantum-resistant cryptographic...
-
On Projections to Linear Subspaces
The merit of projecting data onto linear subspaces is well known from, e.g., dimension reduction. One key aspect of subspace projections, the maximum...
-
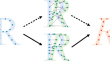
Unsupervised non-rigid point cloud registration based on point-wise displacement learning
Registration of deformable objects is a fundamental prerequisite for many modern virtual reality and computer vision applications. However, due to...
-
Asymptotic Analysis of Regular Sequences
In this article, q -regular sequences in the sense of Allouche and Shallit are analysed asymptotically. It is shown that the summatory function of a...

-
Frames over finite fields and self-dual codes
Modular strongly regular graphs have been introduced by Greaves et al. (Linear Algebra Appl 639:50–80, 2022). We show that a related class of isodual...
-
DIPSAUCE: Efficient Private Stream Aggregation Without Trusted Parties
Private Stream Aggregation (PSA) schemes are efficient protocols for distributed data analytics. In a PSA scheme, a set of data producers can encrypt...
-
Lattice-Based Zero-Knowledge Proofs and Applications: Shorter, Simpler, and More General
We present a much-improved practical protocol, based on the hardness of Module-SIS and Module-LWE problems, for proving knowledge of a short vector...
-
The Data Encryption Standard (DES) and Alternatives
The Data Encryption Standard, or DES, was conceived in the early 1970s and can arguably be considered the first modern encryption algorithm. It was...
-
MDS codes with l-Galois hulls of arbitrary dimensions
The hull of a linear code is defined to be the intersection of the code and its dual, and was originally introduced to classify finite projective...
-
Optimization of the Storage Location Assignment Problem Using Nested Annealing
The Storage Location Assignment Problem (SLAP) has a significant impact on the efficiency of warehouse operations. We propose a multi-phase optimizer...
-
Decomposition of a Finite Quantum System into Subsystems: Symbolic–Numerical Approach
AbstractAny Hilbert space with composite dimension can be represented as a tensor product of Hilbert spaces of lower dimensions. This factorization...

-
Moderate Examples
This chapter is focused on the importance of moderate examples in the learning curve of programming with MATLAB. Situated between basic tutorials and...
-
The seriation problem in the presence of a double Fiedler value
Seriation is a problem consisting of seeking the best enumeration order of a set of units whose interrelationship is described by a bipartite graph....

