Search
Search Results
-
On private information retrieval supporting range queries
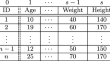
Private information retrieval (PIR) allows a client to retrieve data from a database without the database server learning what data are being...
-
On the effectiveness of differential privacy to continuous queries
Location-based services have a wide range of applications; more recent among those include monitoring virus spread and disaster management....

-
IXT: Improved searchable encryption for multi-word queries based on PSI
Oblivious Cross-Tags (OXT) [
1 ] is the first efficient searchable encryption (SE) protocol for conjunctive queries in a single-writer single-reader... -

-
Efficient searchable symmetric encryption supporting range queries
The demand for cloud storage services continuously increases putting at risk the privacy of the outsourced data. Data encryption is the obvious...

-
Local dampening: differential privacy for non-numeric queries via local sensitivity
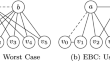
Differential privacy is the state-of-the-art formal definition for data release under strong privacy guarantees. A variety of mechanisms have been...
-
Boolean interpretation, matching, and ranking of natural language queries in product selection systems
E-commerce is a massive sector in the US economy, generating $767.7 billion in revenue in 2021. E-commerce sites maximize their revenue by hel**...

-
Differentially private tree-based redescription mining
Differential privacy provides a strong form of privacy and allows preserving most of the original characteristics of the dataset. Utilizing these...

-

-
PLQ: An Efficient Approach to Processing Pattern-Based Log Queries
As software systems grow more and more complex, extensive techniques have been proposed to analyze log data to obtain the insight of the system...
-
Verifiable searchable symmetric encryption for conjunctive keyword queries in cloud storage
Searchable symmetric encryption (SSE) has been introduced for secure outsourcing the encrypted database to cloud storage, while maintaining...
-
Improving Accuracy of Interactive Queries in Personalized Differential Privacy
Privacy-preserving data publishing has been an important research field in the era of big data. Various privacy protection schemes have been proposed...
-
Collusion-resistant protocols for private processing of aggregated queries in distributed databases
Private processing of database queries protects the confidentiality of sensitive data when queries are answered. It is important to design...

-
Differentially Private Range Query on Shortest Paths
We consider range queries on a graph under the constraints of differential privacy and query ranges are defined as the set of edges on the shortest...
-
Blockchain Technology in 5G Networks: Performance Comparison of Private and Public Blockchains
AbstractThe use of blockchain in 5G networks gives a number of opportunities to improve security, privacy, and quality of service. However, despite...

-

-
Advanced Queries
At this point, most of you will know enough about queries from what you have learned so far that you will likely not need any of the material from...
-
Private Set Operations from Multi-query Reverse Private Membership Test
Private set operations allow two parties to perform secure computation on their private sets, including intersection, union and functions of...
-
Relation representation based on private and shared features for adaptive few-shot link prediction
Although Knowledge Graphs (KGs) provide great value in many applications, they are often incomplete with many missing facts. KG Completion (KGC) is a...

-
Scaling Mobile Private Contact Discovery to Billions of Users
Mobile contact discovery is a convenience feature of messengers such as WhatsApp or Telegram that helps users to identify which of their existing...
