Search
Search Results
-
Tight Bounds on the Randomness Complexity of Secure Multiparty Computation
We revisit the question of minimizing the randomness complexity of protocols for secure multiparty computation (MPC) in the setting of perfect...
-
A novel focus encoding scheme for addressee detection in multiparty interaction using machine learning algorithms
Addressee detection is a fundamental task for seamless dialogue management and turn taking in human-agent interaction. Though addressee detection is...

-
A survey of discourse parsing
Discourse parsing is an important research area in natural language processing (NLP), which aims to parse the discourse structure of coherent...
-
Microsoft Teams Phone (Voice) Configuration and Management
Teams brings together calling, meeting, chat collaboration, and apps, thereby hel** users easily stay connected right in their workflow. Microsoft...
-
Differentially private multi-agent constraint optimization
Distributed constraint optimization (DCOP) is a framework in which multiple agents with private constraints (or preferences) cooperate to achieve a...

-
Exploring Type-Level Bisimilarity towards More Expressive Multiparty Session Types
A key open problem with multiparty session types (MPST) concerns their expressiveness: current MPST have inflexible choice, no existential...
-
Audio-video fusion strategies for active speaker detection in meetings
Meetings are a common activity in professional contexts, and it remains challenging to endow vocal assistants with advanced functionalities to...

-
Towards Multiparty Computation Withstanding Coercion of All Parties
Incoercible multi-party computation [Canetti-Gennaro’96] allows parties to engage in secure computation with the additional guarantee that the public...
-
Testing Equality Under the Local Broadcast Model
In the multiparty equality problem, each of the n nodes starts with a k-bit input. If there is a mismatch between the inputs, then at least one node...
-
Explorations in multiparty casual social talk and its relevance for social human machine dialogue
Much talk between humans is face-to-face, casual, multiparty, and of indefinite duration. Such casual conversation or social talk facilitates social...

-
Privacy-Preserving Federated Learning System (f-PPLS) for military focused area classification
Accurate classification of military-focused areas using machine learning techniques is crucial for meeting military criteria. However, preserving...

-
CAPABARA: A Combined Attack on CAPA
Physical attacks pose a substantial threat to the secure implementation of cryptographic algorithms. While considerable research efforts are...
-
Marginal Release Under Multi-party Personalized Differential Privacy
Given a set of local datasets held by multiple parties, we study the problem of learning marginals over the integrated dataset while satisfying...
-
Chunks in Multiparty Conversation—Building Blocks for Extended Social Talk
Building applications which can form a longer term social bond with a user or engage with a group of users calls for knowledge of how longer...
-
Towards privacy preserved document image classification: a comprehensive benchmark
As data-driven AI systems become increasingly integrated into industry, concerns have recently arisen regarding potential privacy breaches and the...

-
Survey on user perceived system factors influencing the QoE of audiovisual calls on smartphones
With the widespread use of applications and services supporting audiovisual calls via smartphones, both in business and leisure contexts, a key...

-
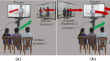
Multiparty gaze preservation through perspective switching for interactive elearning environments
Existing live tele-teaching systems enable eye-contact between interacting participants, however, they are often incomplete as they neglect finer...
-
Privacy-Preserving Data Mining
The growth of data mining has raised concerns among privacy advocates. Some of this is based on a misunderstanding of what data mining does. The...
-
The Impact of Packet Loss and Google Congestion Control on QoE for WebRTC-Based Mobile Multiparty Audiovisual Telemeetings
While previous expensive and complex desktop video conferencing solutions had a restricted reach, the emergence of the WebRTC (Web Real-Time...
-
Performance Evaluation of Multiparty Authentication in 5G IIoT Environments
With the rapid development of various emerging technologies such as the Industrial Internet of Things (IIoT), there is a need to secure...
