Search
Search Results
-
A gapless code-based hash proof system based on RQC and its applications
Cramer and Shoup introduced at Eurocrypt’02 the concept of hash proof system, also designated as smooth projective hash functions. Since then, they...

-
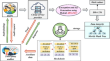
Secure and efficient public auditing system of user data using hybrid AES-ECC crypto system with Merkle hash tree in blockchain
Data auditing permits data owners to confirm the reliability of their personal information without obtaining it from an unsafe cloud. Advertising...
-
A Gapless Post-quantum Hash Proof System in the Hamming Metric
A hash proof system (HPS) is a form of implicit proof of membership to a language. Out of the very few existing post-quantum HPS, most are based on...
-
Decentralization System Using Smart Blockchain with Secure Hash
Blockchain decentralization is a reference to decision making and transferring of data control. It is derived as a distributed network from a...

-
Lattice-Based Programmable Hash Functions and Applications
Driven by the open problem raised by Hofheinz and Kiltz (J Cryptol 25(3):484–527, 2012), we study the formalization of lattice-based programmable...

-
Hash Functions
Hash functions are an important primitive in cryptography and are widely used in practice. They compute a digest of a message, which is a short,...
-
Hash-based signature revisited
The current development toward quantum attack has shocked our confidence on classical digital signature schemes. As one of the mainstreams of post...

-
Proof of location based delivery system using multi-party virtual state channel: a blockchain model
Supply chain management speeds up the delivery system and product flow towards customers. It is required to update the delivery system and fulfill...

-
Block chain-based security and authentication for forensics application using consensus proof of work and zero knowledge protocol
The technique that checks the origin, integrity, Zero-Knowledge authenticity of photographs is known as image authentication. Numerous studies on...

-
Formalizing Hash-then-Sign Signatures
Many practical signature schemes follow the Hash-then-Sign (HtS) paradigm: Instead of signing messages directly, messages are first hashed and then...
-
Tagged Chameleon Hash from Lattices and Application to Redactable Blockchain
Chameleon hash (CH) is a trapdoor hash function. Generally it is hard to find collisions, but with the help of a trapdoor, finding collisions becomes...
-
Verifying a Realistic Mutable Hash Table
In this work, we verify, using the Stainless program verifier, the mutable LongMap from the Scala standard library, a hash table using open...
-
Probabilistic Hash-and-Sign with Retry in the Quantum Random Oracle Model
A hash-and-sign signature based on a preimage-sampleable function (Gentry et al., STOC 2008) is secure in the quantum random oracle model if the...
-
Blockchain-based tamper-proof and transparent investigation model for cloud VMs
In cloud forensics, ensuring the integrity of the evidence such that it is admissible in a court of law is essential. There is always a possibility...

-
An efficient quantum non-interactive zero knowledge proof for confidential transaction and quantum range proof
This paper investigated the Bitcoin blockchain and other crypto currencies confidential transaction techniques for cryptographic commitment in a...

-
On the correctness of a lock-free compression-based elastic mechanism for a hash trie design
A key aspect of any hash map design is the problem of dynamically resizing it in order to deal with hash collisions. Compression in tree-based hash...

-
SNACKs for Proof-of-Space Blockchains
SNACKs are succinct non-interactive arguments of chain knowledge. They allow for efficient and generic solutions to blockchain light-client...
-
Hash-Based Direct Anonymous Attestation
Direct Anonymous Attestation (DAA) was designed for the Trusted Platform Module (TPM) and versions using RSA and elliptic curve cryptography have...
-
BAHS: A Blockchain-Aided Hash-Based Signature Scheme
Hash-based one-time signatures are becoming increasingly important as they are post-quantum safe and have been used in multi-cast communication and...
-
Light weight hash function using secured key distribution technique for MANET
Mobile adhoc network has stringent requirements of light weight computations with aid of kee** track with the processing power and speed, without...

