Search
Search Results
-
Cloud data security for distributed embedded systems using machine learning and cryptography
In the growing demand for distributed embedded systems that efficiently execute complex processes and high-end applications, safeguarding sensitive...

-
A survey on IoT & embedded device firmware security: architecture, extraction techniques, and vulnerability analysis frameworks
IoT and Embedded devices grow at an exponential rate, however, without adequate security mechanisms in place. One of the key challenges in the cyber...

-
Unboxing fog security: a review of fog security and authentication mechanisms
Due to the massive advancement of the Internet of Things in our day-to-day lives, there is a strong need to bring connectivity to a very accessible...

-
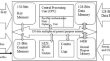
Lightweight micro-architecture for IoT & FPGA security
Cryptographic standards were created with the goal of being able to work on a wide range of systems. Small computing systems with limited capacity to...
-
A novel trusted hardware-based scalable security framework for IoT edge devices
The Internet of Things (IoT) devices are pervasively deployed and embedded into our daily lives. Over several years, the massive assimilation of IoT...

-
Intelligent detection for sustainable agriculture: A review of IoT-based embedded systems, cloud platforms, DL, and ML for plant disease detection
Plant diseases pose a significant threat to the sustainability of the environment and global food security. With an increasing population density and...

-
A Haskell-Embedded DSL for Secure Information-Flow
This paper presents a domain specific language, embedded in Haskell (EDSL), for enforcing the information flow policy Delimited Release. To build...
-
SDK4ED: a platform for building energy efficient, dependable, and maintainable embedded software
Develo** embedded software applications is a challenging task, chiefly due to the limitations that are imposed by the hardware devices or platforms...

-
A survey on counting-based secret sharing schemes for resource-constrained environments: techniques, security, challenges, and future directions
Secret sharing schemes play a vital role in securely distributing a secret among multiple participants, ensuring confidentiality and access control....

-
Embedded 3D reconstruction of dynamic objects in real time for maritime situational awareness pictures
Assessing the security status of maritime infrastructures is a key factor for maritime safety and security. Facilities such as ports and harbors are...

-
Authenticable medical image-sharing scheme based on embedded small shadow QR code and blockchain framework
In the field of medical image content protection and security sharing, the introduction of blockchain technology has a problem in that the secret key...

-
Security enhanced random grid visual cryptography scheme using master share and embedding method
Visual cryptography scheme is one of the main branches of secret sharing. The image is converted into various shares and then recouped by overlap**...

-
Winternitz stack protocols for embedded systems and IoT
This paper proposes and evaluates a new bipartite post-quantum digital signature protocol based on Winternitz chains and an oracle. Mutually...

-
Ontology-based security modeling in ArchiMate
Enterprise Risk Management involves the process of identification, evaluation, treatment, and communication regarding risks throughout the...

-
The current state and future of mobile security in the light of the recent mobile security threat reports
Smartphones have become small computers that meet many of our needs, from e-mail and banking transactions to communication and social media use. In...
-
Rest security framework for event streaming bus architecture
Businesses are confronted with a massive influx of real-time data originating from various sources such as application logs, website clickstreams,...

-
Effect of Data Sampling on Cone Shaped Embedded Normalization in Just in Time Software Defect Prediction
Just-in-Time (JIT) defect prediction represents a software engineering approach that seeks to detect potential defects in software code at the...

-
Beyond traditional steganography: enhancing security and performance with spread spectrum image steganography
This study investigates the innovative application of Direct Sequence Spread Spectrum (DSSS) technology in the realm of image steganography, known as...

-
TSEE: a novel knowledge embedding framework for cyberspace security
Knowledge representation models have been extensively studied and they provide an important foundation for artificial intelligence. However, the...

-
On the Security of Smart Home Systems: A Survey
Among the plethora of IoT (Internet of Things) applications, the smart home is one of the fastest-growing. However, the rapid development of the...
