Search
Search Results
-
Perceptions and dilemmas around cyber-security in a Spanish research center after a cyber-attack
Information and Communication Technologies and Internet networks are present in all aspects of social reality and are essential elements in research,...
-
Grou** and Determining Perceived Severity of Cyber-Attack Consequences: Gaining Information Needed to Sonify Cyber-Attacks
Cyber-attacks are a continuing problem. These attacks are problematic for users who are visually impaired and cannot rely on visual cues to indicate...

-
Enhancing attack resilience of cyber-physical systems through state dependency graph models
This paper presents a method that utilizes graph theory and state modelling algorithms to perform automatic complexity analysis of the architecture...

-
A new cloud-based cyber-attack detection architecture for hyper-automation process in industrial internet of things
With rapid development and deployment of artificial intelligence methods, the Industrial Internet of Things (IIoT) has highly developed to fast...
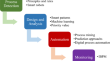
-
Next-generation cyber attack prediction for IoT systems: leveraging multi-class SVM and optimized CHAID decision tree
Billions of gadgets are already online, making the IoT an essential aspect of daily life. However, the interconnected nature of IoT devices also...

-
On specification-based cyber-attack detection in smart grids
The transformation of power grids into intelligent cyber-physical systems brings numerous benefits, but also significantly increases the surface for...
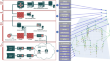
-
Extremely boosted neural network for more accurate multi-stage Cyber attack prediction in cloud computing environment
There is an increase in cyberattacks directed at the network behind firewalls. An all-inclusive approach is proposed in this assessment to deal with...
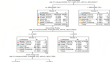
-
MDepthNet based phishing attack detection using integrated deep learning methodologies for cyber security enhancement
Develo** technologies over digitalization have become more popular and become a threat to society and cybersecurity. Generally, the phishing method...

-
Cyber-Attack Detection Using Machine Learning Technique
Cybersecurity is crucial for protecting users of the internet on various electronic devices in everyday life. It is crucial for safeguarding some...
-
Salp Swarm-Artificial Neural Network Based Cyber-Attack Detection in Smart Grid
Smart Grid (SG) can be easily attacked by smart hackers who try to corrupt the data aggregated by the acquisition system and supervisory control. The...

-
Cyber-Attack Analysis Using Vulnerability Assessment and Penetration Testing
Networks and systems like computers and mobile devices are not secure enough and are vulnerable to numerous types of cyber-threats. The frequency of...
-
URSID: Automatically Refining a Single Attack Scenario into Multiple Cyber Range Architectures
Contrary to intuition, insecure computer network architectures are valuable assets in IT security. Indeed, such architectures (referred to as...
-
Locating collaborative attack targets based on physical invariants toward cyber-physical systems
Various studies have demonstrated that the collaborative false command injection (FCI) and false sensory data injection (FDI) attacks can go...

-
Deep-Learning Based Detection for Cyber-Attacks in IoT Networks: A Distributed Attack Detection Framework
The widespread use of smart devices and the numerous security weaknesses of networks has dramatically increased the number of cyber-attacks in the...

-
Trust and Blame in Self-driving Cars Following a Successful Cyber Attack
Even as our ability to counter cyber attacks improves, it is inevitable that threat actors may compromise a system through either exploited...
-
Cyber-Attack Detection in Cyber-Physical Systems Using Supervised Machine Learning
Cyber-Physical Systems (CPS) are where the physical processes are controlled by computation and other technology components. Although, the...
-
Cyber-attack Proactive Defense Using Multivariate Time Series and Machine Learning with Fuzzy Inference-based Decision System
Cybersecurity incidents have dramatically increased in the recent years. The number of cyber-attack variants is also increasing, thus traditional...
-

