Search
Search Results
-
Characterization of Process Families
This Chapter characterizes in general terms the behaviour of three outstanding classes of computational processes working with arbitrary data...
-
Complexity-theoretic aspects of expanding cellular automata
The expanding cellular automata (XCA) variant of cellular automata is investigated and characterized from a complexity-theoretical standpoint. An XCA...

-
Leśniewski’s Ontology – Proof-Theoretic Characterization
The ontology of Leśniewski is commonly regarded as the most comprehensive calculus of names and the theoretical basis of mereology. However, ontology...
-
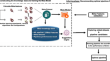
Autoencoder-kNN meta-model based data characterization approach for an automated selection of AI algorithms
The recent evolution of machine learning (ML) algorithms and the high level of expertise required to use them have fuelled the demand for non-experts...
-
A Complete Characterization of Game-Theoretically Fair, Multi-Party Coin Toss
Cleve’s celebrated lower bound (STOC’86) showed that a de facto strong fairness notion is impossible in 2-party coin toss, i.e., the corrupt party...
-
A Characterization of Functions over the Integers Computable in Polynomial Time Using Discrete Ordinary Differential Equations
This paper studies the expressive and computational power of discrete Ordinary Differential Equations (ODEs), a.k.a. (Ordinary) Difference Equations....
-
On the complexity of rational verification
Rational verification refers to the problem of checking which temporal logic properties hold of a concurrent/multiagent system, under the assumption...
-
Decision-Dominant Strategic Defense Against Lateral Movement for 5G Zero-Trust Multi-Domain Networks
Multi-domain warfare is a military doctrine that leverages capabilities from different domains, including air, land, sea, space, and cyberspace, to...
-
A novel approach based on rough set theory for analyzing information disorder
The paper presents and evaluates an approach based on Rough Set Theory, and some variants and extensions of this theory, to analyze phenomena related...

-
Reoptimization of parameterized problems
Parameterized complexity allows us to analyze the time complexity of problems with respect to a natural parameter depending on the problem....

-
Residual Wavelon Convolutional Networks for Characterization of Disease Response on MRI
Wavelets have shown significant promise for medical image decomposition and artifact pre-processing by representing inputs via shifted and scaled...
-
Empirical study on meta-feature characterization for multi-objective optimization problems
Algorithm recommendation based on meta-learning was studied previously. The research on the meta-features extraction, which is a key for the success...

-
Cryptography from Planted Graphs: Security with Logarithmic-Size Messages
We study the following broad question about cryptographic primitives: is it possible to achieve security against arbitrary...
-
Linear Properties of Functions
This chapter is focused on linear affine-invariant properties of functions...
-

-
Blockchain Participation Games
We study game-theoretic models for capturing participation in blockchain systems. Existing blockchains can be naturally viewed as games, where a set...
-
Synthesis of Elementary Cellular Automata for Targeted Cache Applications
Stephen Wolfram’s Cellular Automata (CA) is a powerful universal computing tool. It can provide design solution for various cache applications and...
-
A Uniform Framework for Language Inclusion Problems
We present a uniform approach for solving language inclusion problems. Our approach relies on a least fixpoint characterization and a quasiorder to...
-
Complexity-Theoretic Aspects of Expanding Cellular Automata
The expanding cellular automata (XCA) variant of cellular automata is investigated and characterized from a complexity-theoretical standpoint. The...
-
Algorithm selection using edge ML and case-based reasoning
In practical data mining, a wide range of classification algorithms is employed for prediction tasks. However, selecting the best algorithm poses a...

