Search
Search Results
-
Chosen-ciphertext secure code-based threshold public key encryptions with short ciphertext
Threshold public-key encryption (threshold PKE) has various useful applications. A lot of threshold PKE schemes are proposed based on RSA,...
-
Chosen Ciphertext Security for Blind Identity-Based Encryption with Certified Identities
Identity-based encryption (IBE) is one of the important extension of public-key encryption (PKE) which can use identities, such as email addresses or...
-
TEXCEL: text encryption with elliptic curve cryptography for enhanced security
Elliptic curve cryptography has emerged as a potent tool for safeguarding data communications. This research paper addresses the problem of...

-
Reveal the Invisible Secret: Chosen-Ciphertext Side-Channel Attacks on NTRU
NTRU is a well-known lattice-based cryptosystem that has been selected as one of the four key encapsulation mechanism finalists in Round 3 of NIST’s...
-
On improved security bounds of one block ciphers mode of operation for protection of block-oriented system storage devices
In the end of 2022 in Russian Federation recommendations for standardization were adopted defining a block ciphers mode of operation for...

-
Chosen Ciphertext Secure Keyed Two-Level Homomorphic Encryption
Homomorphic encryption (HE) is a useful variant of public key encryption (PKE), but it has a drawback that HE cannot fully achieve IND-CCA2 security,...
-
CCA Security and Trapdoor Functions via Key-Dependent-Message Security
We study the relationship among public-key encryption (PKE) satisfying indistinguishability against chosen plaintext attacks (IND-CPA security), that...

-

-
Chosen-Ciphertext Secure Dual-Receiver Encryption in the Standard Model Based on Post-quantum Assumptions
Dual-receiver encryption (DRE) is a special form of public key encryption (PKE) that allows a sender to encrypt a message for two recipients. Without...
-
A New Key Recovery Side-Channel Attack on HQC with Chosen Ciphertext
Hamming Quasi-Cyclic (HQC) is a code-based candidate of NIST post-quantum standardization procedure. The decoding steps of code-based cryptosystems...
-
Compact Selective Opening Security from LWE
Selective opening (SO) security is a security notion for public-key encryption schemes that captures security against adaptive corruptions of...
-
Fault-Enabled Chosen-Ciphertext Attacks on Kyber
NIST’s PQC standardization process is in the third round, and a first final choice between one of three remaining lattice-based key-encapsulation...
-
Fully Homomorphic Encryption Beyond IND-CCA1 Security: Integrity Through Verifiability
We focus on the problem of constructing fully homomorphic encryption (FHE) schemes that achieve some meaningful notion of adaptive chosen-ciphertext...
-
Fully Secure ABE with Outsourced Decryption against Chosen Ciphertext Attack
Attribute-based encryption (ABE) provides fine-grained access control on encrypted data, but it is not suitable for limited-resource devices due to...
-
CryptoHHO: a bio-inspired cryptosystem for data security in Fog–Cloud architecture
The exponential growth of Internet-of-Things (IoT) has raised several data security risks to the Fog–Cloud architecture. The performance and the...

-
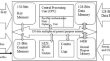
Lightweight micro-architecture for IoT & FPGA security
Cryptographic standards were created with the goal of being able to work on a wide range of systems. Small computing systems with limited capacity to...
-
Decoding the future: exploring and comparing ABE standards for cloud, IoT, blockchain security applications
Data security poses a significant challenge in cloud computing, the Internet of Things (IoT), and blockchain applications. Attribute-Based Encryption...

-
An approach to enhance the security of unmanned aerial vehicles (UAVs)
There is a significant surge in unmanned aerial vehicles’ (UAVs) popularity with an ongoing increase in demand due to their multi-functional uses....

-
Robust Channels: Handling Unreliable Networks in the Record Layers of QUIC and DTLS 1.3
The common approach in secure communication channel protocols is to rely on ciphertexts arriving in-order and to close the connection upon any rogue...

-
Predicate encryption with selective-opening security for receivers: formal definition, generic construction, and concrete instantiations for several primitives
With the rise of cloud computing, multi-user scenarios have become a common setting for data sharing nowadays. The conservative security notion might...

