Search
Search Results
-
Receiver selective opening security for identity-based encryption in the multi-challenge setting
Receiver selective opening (RSO) security requires that in a situation where there are one sender and multiple receivers, even if an adversary has...

-
Digital Identity Infrastructures: a Critical Approach of Self-Sovereign Identity
The shift from electronic identification to digital identity is indicative of a broader evolution towards datafication of identity at large. As...
-
MMUIL: enhancing multi-platform user identity linkage with multi-information
User identity linkage (UIL) aims to link identities belonging to the same individual across various platforms. While numerous methods have been...

-
Fault-tolerant identity-based encryption from SM9
This paper initiates the formal study of attribute-based encryption within the framework of SM9, the Chinese National Cryptography Standard for...
-
Decentralized Digital Identity
The importance of secure and private identity management cannot be overstated. Identity data breaches have had far-reaching consequences, impacting...
-
Secure SSI framework using the optimized Orkey identity schema
In the era of digital transformation and increasing concerns regarding data privacy, the concept of Self-Sovereign Identity (SSI) has attained...

-
Decentralised identity federations using blockchain
Federated Identity Management offers numerous economic benefits and convenience to Service Providers and users alike. In such federations, the...

-
Leakage-resilient identity-based cryptography from minimal assumptions
Identity-based hash proof system (IB-HPS), a variant of hash proof system (HPS) in the identity-based setting, is a useful building block in...

-
Facial mask attention network for identity-aware face super-resolution
Face Super-Resolution (FSR) is a crucial research topic in image restoration field, which is a fundamental task for subsequent face applications,...

-
Self-Sovereign Identity Model: Ethics and Legal Principles
The emergence of Self-Sovereign Identity (SSI) as a new digital identity paradigm has gained significant attention due to its potential to...

-
Age-invariant face recognition based on identity-age shared features
Decoupling the mixed face features to obtain identity features that are not disturbed by age information is the key to achieving cross-age face...

-
Identity-Preserving Adversarial Training for Robust Network Embedding
Network embedding, as an approach to learning low-dimensional representations of nodes, has been proved extremely useful in many applications, e.g.,...
-
High similarity controllable face anonymization based on dynamic identity perception
In the meta-universe scenario, with the development of personalized social networks, interactive behaviors such as uploading and sharing personal and...

-
Topic and knowledge-enhanced modeling for edge-enabled IoT user identity linkage across social networks
The Internet of Things (IoT) devices spawn growing diverse social platforms and online data at the network edge, propelling the development of...

-
Identity Provisioning
The first step in the life of an identity is its creation. If Descartes had lived in the time of Internet identity, he might have quipped, “Ego...
-
Identity-based remote data integrity auditing from lattices for secure cloud storage
In recent years, cloud storage services have risen widely, and how to ensure the integrity of outsourced data in cloud setting catches more and more...

-
Identity verifiable ring signature scheme for privacy protection in blockchain
The revolutionary technology blockchain is spreading into many applications because of its features like immutability, decentralization,...

-
A lightweight identity based generalized signcryption scheme for secure communication in standard model
The implementation of secure communication in the Industrial Internet of Things (IIoT) has made and it is a significant security concern....
-
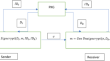
Hierarchical Identity-Based Authenticated Encryption with Keyword Search over encrypted cloud data
With the rapid development of cloud computing technology, cloud storage services are becoming more and more mature. However, the storage of sensitive...

-
Identity-based proof of retrievability meets with identity-based network coding
Network coding and cloud storage are two quite different areas in their nature and were studied independently in the past years. In recent years,...

