Search
Search Results
-
Improved biometric authentication using surf based variational Bayesian extreme learning machine
Over the last decade, biometric authentication systems have significantly progressed and in the upcoming years, their domain specific application is...

-
Ensemble recognition model with optimal training for multimodal biometric authentication
Biometric security methods deploy any type of biometric recognition for safety purposes. Different from unimodal biometric system that uses single...

-
A cancelable biometric authentication scheme based on geometric transformation
In digital identification technologies, fingerprint-based biometric systems are extensively utilized for authentication. Fingerprint authentication...

-
Continuous Biometric Authentication Systems An Overview
This book offers an overview of the field of continuous biometric authentication systems, which capture and continuously authenticate biometrics from...
-
Cancelable biometric authentication system based on hyperchaotic technique and fibonacci Q-Matrix
Due to the rapid growth in the field of information transmission techniques, billions of data are transmitted through variant authentication...

-
Enhancing biometric authentication security through the novel integration of graph theory encryption and chaotic logistic map**
The escalating reliance on biometric systems for identity verification underscores the imperative for robust data protection mechanisms. Biometric...

-
Deep learning-powered multimodal biometric authentication: integrating dynamic signatures and facial data for enhanced online security
The significant increase in online activities in the wake of recent global events has underlined the importance of biometric person authentication on...

-
Robust Rabin Cryptosystem Biometric Privacy Preserving Authentication Technique for IoT Enabled Devices Over Cloud
With the advent of growing technologies and digitalization, smart factories and healthcare systems in the cloud are more focused towards task-driven...

-
Authentication-based multimodal biometric system using exponential water wave optimization algorithm
The biometric system relies on a single biometric identifier which could not meet the desired performance required for personal identification....

-
Performance Evaluation of Biometric Authentication Using Fragment Jaya Optimizer-Based Deep CNN with Multi-kernel SVM
The earlier research clearly indicated that the bimodal authentication system has more efficiency than unimodal and multimodal. This is due to the...

-
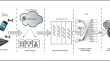
BAMCloud: a cloud based Mobile biometric authentication framework
There has been an exponential increase in the number of users switching to mobile banking. Therefore, various countries are adopting biometric...
-
Secure deep multimodal biometric authentication using online signature and face features fusion
In Indian banking systems, signatures and faces are the two traits of biometrics that are used for personal identification. The automation of this...

-
A novel technique for fingerprint template security in biometric authentication systems
The deployment of biometrics spans over almost every application that incorporates user authentication. Fingerprint biometrics in particular is by...

-
Oblivious Extractors and Improved Security in Biometric-Based Authentication Systems
We study the problem of biometric-based authentication with template privacy. Typical schemes addressing this problem, such as Fuzzy Vaults (...
-
A Novel Biometric Authentication Based on Blockchain and Watermarking
After analysing the security threats and solution of existing authentication systems, this paper proposes a biometric authentication based on...
-

-
Implementation of quaternion mathematics for biometric security
Cancellable biometrics is an important trend in biometric security systems, allowing for intentional distortions or variations in the original...

-
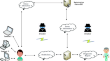
A multi-server biometric authentication scheme based on extended chaotic map for telecare medical information system
Telemedicine Information System (TMIS) is a platform for data communication and exchange between patients and medical servers via the Internet....
-
Hiding Your Signals: A Security Analysis of PPG-Based Biometric Authentication
Recently, physiological signal-based biometric systems have received wide attention. Photoplethysmogram (PPG) signal is easy to measure, making it...
-
An efficient remote user authentication with key agreement procedure based on convolution-Chebyshev chaotic maps using biometric
The study of chaotic constructions and their associated cryptographic frameworks has sparked a lot of research interest in recent years. Latest...

