Search
Search Results
-
Existence versus exploitation: the opacity of backdoors and backbones
Boolean formulas often have what are known as hidden structures. We study the complexity of whether such structures (of certain sizes) exist in a...
-
U.S. Security Policy: The Dual-Use Regulation of Cryptography and its Effects on Surveillance
Cryptography has become ubiquitous in communication technology and is considered a necessary part of information security. However, the regulation to...
-
Embedding asymmetric backdoors into the RSA key generator
This article describes the class of asymmetric backdoors in the RSA key generator. The algorithms are based on the classical Anderson’s backdoor, but...
-
Mathematical Foundation for Classical and Modern Cryptography
The design of public-key cyphers prevents knowledge of the encryption key from revealing the identity of the decryption key. Making advantage of a...
-
Blockchain-based immunization against kleptographic attacks
Adversarial implementations of cryptographic primitives called kleptographic attacks cause the leakage of secret information. Subliminal channel...
-
How to Backdoor (Classic) McEliece and How to Guard Against Backdoors
We show how to backdoor the McEliece cryptosystem such that a backdoored public key is indistinguishable from a usual public key, but allows to...
-
Detection of non-trivial preservable quotient spaces in S-Box(es)
Substitution Box (S-Box) is employed in block ciphers to ensure non-linearity. An n -bit bijective S-Box is a member of the Symmetric Group
... 
-
Specifying a principle of cryptographic justice as a response to the problem of going dark
Over the past decade, the Five Eyes Intelligence community has argued cryptosystems with end-to-end encryption (E2EE) are disrupting the acquisition...
-
Heterogeneous IoT (HetIoT) security: techniques, challenges and open issues
The HetIoT is a new emergent technology widely used to offer QoS to applications such as health monitoring systems, agriculture 4.0, traffic...

-
Patent Landscape in the field of Hash-Based Post-Quantum Signatures
Post-Quantum Cryptography (PQC) is one of the most fascinating topics of recent developments in cryptography. Following the ongoing standardization...
-
Security Risks from Vulnerabilities and Backdoors
It is well-known that Alan Mathison Turing, a mathematician, put forward an abstract computing model, Turing Machine, and provided a solution to the...
-
The MALICIOUS Framework: Embedding Backdoors into Tweakable Block Ciphers
Inserting backdoors in encryption algorithms has long seemed like a very interesting, yet difficult problem. Most attempts have been unsuccessful for...
-
On the Possibility of a Backdoor in the Micali-Schnorr Generator
In this paper, we study both the implications and potential impact of backdoored parameters for two RSA-based pseudorandom number generators: the...
-
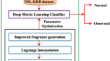
mLBOA-DML: modified butterfly optimized deep metric learning for enhancing accuracy in intrusion detection system
Intrusion detection is a prominent factor in the cybersecurity domain that prevents the network from malicious attacks. Cloud security is not...
-
A Medium-Length History of Digital Cryptography
Having taken a look at the basics of digital cryptography in the previous chapter, we'll now move on to some specifics of the topic. We'll take a...
-
Security Architecture and Engineering
Security Architecture and Engineering is one of the eight domains of the CISSP Common Body of Knowledge. This domain focuses on designing,...
-
Quantum Computing, Digital Constitutionalism, and the Right to Encryption: Perspectives from Brazil
This article examines how the debates on a right to encryption, understood within the framework of digital constitutionalism, may be impacted by the...
-
Development of the RISC-V entropy source interface
The RISC-V true random number generator (TRNG) architecture breaks with previous ISA TRNG practice by splitting the entropy source (ES) component...

-
A Survey on Security in Data Transmission in IoT: Layered Architecture
The Internet of Things (IoT) is the communications technology where, physical objects, which are basically not designed for connection, will be able...
-
A Combination Reduction Algorithm and Its Application
After the Snowden incident, cryptographic subversion attack has attracted widespread attentions. Subversion attack is an unconventional attack inside...
