Search
Search Results
-
Pre-trained non-intrusive load monitoring model for recognizing activity of daily living
Non-intrusive load monitoring (NILM) is a technology that analyzes total electricity consumption data to determine whether a specific type of...

-
A framework for low cost, ubiquitous and interactive smart refrigerator
Internet of Things (IoT) and Artificial Intelligence (AI)-enabled technologies are essential in develo** innovative environments and intelligent...

-
Nonexclusive Classification of Household Appliances by Fuzzy Deep Neural Networks
Fuzzy classification is a very useful tool for managing the uncertainty in a classification problem with non-mutually exclusive classes, whose values...
-
Towards efficient human–machine interaction for home energy management with seasonal scheduling using deep fuzzy neural optimizer
Maintaining the records of domestic consumers’ electricity consumption patterns is very complex task for the utilities, especially for extracting the...
-
Securing Workloads on VMWare Cloud on AWS
This chapter provides the basic understanding on how VMware NSX is integrated into VMware Cloud on AWS to deliver the virtual networking features...
-
On the non-intrusive extraction of residents’ privacy- and security-sensitive information from energy smart meters
Energy smart meters have become very popular in monitoring and smart energy management applications. However, the acquired measurements except the...

-
Towards effective urban region-of-interest demand modeling via graph representation learning
Identifying the region’s functionalities and what the specific Point-of-Interest (POI) needs is essential for effective urban planning. However, due...

-

-
Towards personalized control of things using Arabic voice commands for elderly and with disabilities people
Considering recent smart home solutions that automate home appliances through voice commands, elderly people and/or with special needs prefer using...

-
Demand Manipulation Attack Resilient Privacy Aware Smart Grid Using PUFs and Blockchain
In recent years, the transitioning of conventional power grid system into the smart grid infrastructure has made the power distribution network more...
-
Privacy and Tracking
In order for ubiquitous computing to realize its full potential, it is necessary for service providers to detect the presence of user devices to...
-
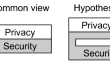
Organisational Security Dependent on Individual Privacy
The global proliferation of cloud computing, smart homes, the internet of things and machine learning requires a novel view on the flow of...
-

-
Let’s Cook: An Augmented Reality System Towards Develo** Cooking Skills for Children with Cognitive Impairments
Although activities of daily living are often difficult for individuals with cognitive impairments, their autonomy and independence can be fostered...
-
Detection of Behavioral Data Based on Recordings from Energy Usage Sensor
Monitoring of human behavior in the natural living habitat requires a hidden yet accurate measurement. Several previous attempts showed, that this...
-
Multi-Factor Authentication
Multi-Factor authentication (MFA) is a secure process of authentication which requires more than one authentication technique chosen from independent...
-
Feature Learning Architecture Taxonomy and Neuroscience Background
In many respects, computer vision practitioners are now being outpaced by neuroscientists, who are leading the way, modeling computer vision systems...
-
Ensemble Learning of Run-Time Prediction Models for Data-Intensive Scientific Workflows
Workflow applications for in-silico experimentation involve the processing of large amounts of data. One of the core issues for the efficient...
-
Non-intrusive Identification of Electrical Appliances
The aim of reducing greenhouse gases and increasing energy efficiency faces a number of challenges to date. A significant portion of overall energy...
-
Web-GIS models: accomplishing modularity with aspects
Spatial concerns of Web geographical information systems (Web-GIS) are inherently crosscutting and volatile: crosscutting because they affect...

