Search
Search Results
-
The right to audit and power asymmetries in algorithm auditing
In this paper, we engage with and expand on the keynote talk about the “Right to Audit” given by Prof. Christian Sandvig at the International...
-
Practical cloud storage auditing using serverless computing
Cloud storage auditing research is dedicated to solving the data integrity problem of outsourced storage on the cloud. In recent years, researchers...
-
Legal Auditing
In this chapter, we specify the business requirements and propose the solution concept for legal auditing. Artificial intelligence training and...
-
Block chain-based decentralized public auditing for cloud storage with improved EIGAMAL encryption model
With the growing relevance of data integrity, public auditing mechanisms for cloud storage models are intensively researched. In public auditing...

-
Cloud auditing and authentication scheme for establishing privacy preservation
Data outsourcing to cloud servers is increased with the development of cloud storage. While increasing the amount of cloud storage, it leads to data...

-
Auditing of AI: Legal, Ethical and Technical Approaches
AI auditing is a rapidly growing field of research and practice. This review article, which doubles as an editorial to Digital Society’s topical...

-
General construction of compressive integrity auditing protocol from strong homomorphic encryption scheme
In the applications of cloud storage, ensuring data’s integrity is an important research problem and kinds of remote integrity auditing protocols...

-
A generic framework for blockchain-assisted on-chain auditing for off-chain storage
In recent times, blockchain-based data auditing protocols have emerged as a cutting-edge area of study. Nevertheless, a conspicuous dearth of a...

-
Identity-based remote data integrity auditing from lattices for secure cloud storage
In recent years, cloud storage services have risen widely, and how to ensure the integrity of outsourced data in cloud setting catches more and more...

-
Black-Box Testing and Auditing of Bias in ADM Systems
For years, the number of opaque algorithmic decision-making systems (ADM systems) with a large impact on society has been increasing: e.g., systems...

-
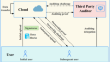
Secure cloud storage auditing with deduplication and efficient data transfer
To guarantee the integrity of cloud data, plenty of cloud storage auditing schemes are proposed. In cloud storage, when a company is purchased by...
-
Blockchain-assisted post-quantum privacy-preserving public auditing scheme to secure multimedia data in cloud storage
With the escalation of multimedia data, cloud technology has played a very important role in its management with its promising computing and storage...

-
Auditing large language models: a three-layered approach
Large language models (LLMs) represent a major advance in artificial intelligence (AI) research. However, the widespread use of LLMs is also coupled...

-
A blockchain assisted public auditing scheme for cloud-based digital twin healthcare services
The convergence with the emerging digital twin technology has been envisaged as the looming of a smart cloud-based healthcare system. Precision clone...

-
They shall be fair, transparent, and robust: auditing learning analytics systems
In the near future, systems, that use Artificial Intelligence (AI) methods, such as machine learning, are required to be certified or audited for...

-
More or less discrimination? Practical feasibility of fairness auditing of technologies for personnel selection
The use of technologies in personnel selection has come under increased scrutiny in recent years, revealing their potential to amplify existing...
-
Distributional constraint discovery for intelligent auditing
Constraint discovery in relational databases aims to find constraints that express dependency relationships among a set of attributes and has...

-
Survey on Cloud Auditing by Using Integrity Checking Algorithm and Key Validation Mechanism
Cloud computing can be used to access and storing data and delivery of different services over the internet. Using cloud storage, users can remotely...
-
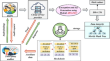
Secure and efficient public auditing system of user data using hybrid AES-ECC crypto system with Merkle hash tree in blockchain
Data auditing permits data owners to confirm the reliability of their personal information without obtaining it from an unsafe cloud. Advertising...
-
Continuous Auditing of Artificial Intelligence: a Conceptualization and Assessment of Tools and Frameworks
Artificial intelligence (AI), which refers to both a research field and a set of technologies, is rapidly growing and has already spread to...

