Search
Search Results
-
Recognition Algorithms Based on the Selection of 2D Representative Pseudo-objects
Building of a recognition algorithms (RA) based on the selection of representative pseudo-objects and providing a solution to the problem of...
-
Direct sequence spread spectrum (DSSS) signal detection based on eigenvalues local binary pattern residual network (EL-ResNet)
Direct sequence spread spectrum (DSSS) communications are highly significant in military and civilian wireless communications because of its ability...

-
Pseudo-mixing Time of Random Walks
We introduce the notion of pseudo-mixing time of a graph, defined as the number of steps in a random walk that suffices for generating a vertex that...
-
Pseudo-labeling and clustering-based active learning for imbalanced classification of wafer bin map defects
Wafer bin map (WBM) defect patterns play a crucial role in identifying the root cause of manufacturing defects in the semiconductor industry....

-
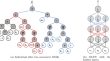
Geometric semantic genetic programming with normalized and standardized random programs
Geometric semantic genetic programming (GSGP) represents one of the most promising developments in the area of evolutionary computation (EC) in the...
-
An ultrahigh-resolution image encryption algorithm using random super-pixel strategy
Almost all existing image encryption algorithms are only suitable for low-resolution images in the standard image library. When they are used to...

-
Image encryption algorithm with 2D coupled discrete chaos
A two-dimensional coupled discrete chaotic system is constructed by combining a two-dimensional coupled map lattice with a dynamic discrete tent map....

-
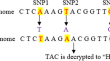
Develo** a novel DNA-based steganography algorithm using random table generation with segmentation
Genome steganography has emerged as a promising field for transmitting large amounts of data over an untrusted channel in the last two decades. DNA...
-
Random Numbers and Simulation
A random number or a random variable is a result of a random process where the result is not deterministic. We can only know the exact value of the...
-
Ascent Guidance for Airbreathing Hypersonic Vehicle Based on Deep Neural Network and Pseudo-spectral Method
The hypersonic vehicle has received wide attention because of its high speed and large flight domain. However, the ascent guidance is quite...
-
A JAYA algorithm based on normal clouds for DNA sequence optimization
DNA computing is one of the more popular computational methods currently studied, but the requirements for nucleic acid molecules in DNA sequences...

-
Image encryption with one-time password mechanism and pseudo-features
An image encryption algorithm based on chaotic sequence and permutation matrix is presented in this paper, with the ability to create pseudo-features...

-
Image encryption algorithm based on face recognition, facial features recognition and bitonic sequence
Traditional scrambling algorithms frequently rely on static and fixed scrambling modes, which lack the involvement of chaotic sequences during the...

-
A True Random Number Generator Based on ADC Random Interval Sampling
This paper presents a true random number generator (TRNG) based on traditional Microcontroller Unit (MCU) with analog-to-digital converter (ADC)....
-
Triplet encoded sequence based membrane protein classification using BiLSTM
Membrane proteins provide a significant part in cellular activities. The role of membrane proteins is inevitable in drug interactions and in all...

-
Connectionist Temporal Sequence Decoding: M-ary Hopfield Neural-Network with Multi-limit Cycle Formulation
Recently, we have proposed a novel M-ary (multi-level) Hopfield neural-network (MHNN) based auto-associative memory formulation for storage and...
-
A computational model to identify fertility-related proteins using sequence information
Fertility is the most crucial step in the development process, which is controlled by many fertility-related proteins, including spermatogenesis-,...
-
A novel and Fast hybrid design of cryptosystems for Image via 5-D chaos based random keys and DNA
The greatest issue in the age of information technology is safeguarding the real-time colour digital image. In this work, a colour image encryption...

-
The Cost of Randomness in Evolutionary Algorithms: Crossover can Save Random Bits
Evolutionary algorithms make countless random decisions during selection, mutation and crossover operations. These random decisions require a steady...
-
A secure image encryption scheme based on genetic operations and a new hybrid pseudo random number generator
This paper presents an encryption scheme based on genetic operations and a new hybrid pseudo random number generator (HPRNG). The new HPRNG is...

