Search
Search Results
-
CADS-ML/DL: efficient cloud-based multi-attack detection system
With the increasing adoption of cloud computing, securing cloud-based systems and applications has become a critical concern for almost every...

-
Valet attack on privacy: a cybersecurity threat in automotive Bluetooth infotainment systems
Modern automobiles are equipped with connectivity features to enhance the user’s comfort. Bluetooth is one such communication technology that is used...

-
Dazzle-attack: Anti-Forensic Server-side Attack via Fail-Free Dynamic State Machine
Server-side malware is one of the prevalent threats that can affect a large number of clients who visit the compromised server. In this paper, we...
-
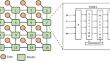
Modelling and Impact Analysis of Antipode Attack in Bufferless On-Chip Networks
With advancements in VLSI technology, Tiled Chip Multicore Processors (TCMP) with packet switching Network-on-Chip (NoC) have evolved as the backbone...
-
Attack Vectors
The first step in establishing a secure cloud environment is understanding the threats it’s likely to encounter. The attack vectors that your...
-
Application and Mitigation of the Evasion Attack against a Deep Learning Based IDS for IoT
An Internet of Things (IoT) network is characterized by ad-hoc connectivity and varying traffic patterns where the routing topology evolves over time...
-
Small-signal stability and robustness analysis for microgrids under time-constrained DoS attacks and a mitigation adaptive secondary control method
With the close integration of cyber and power systems, the consensus-based secondary frequency control in a microgrid is increasingly vulnerable to...
-
Slow Subscribers: a novel IoT-MQTT based denial of service attack
MQTT, a popular IoT messaging protocol, is frequently associated with numerous vulnerabilities, the majority of which are critical. Many IoT devices...

-
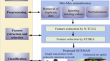
Optimized graph transformer with molecule attention network based multi class attack detection framework for enhancing privacy and security in WSN
In today's rapidly evolving network landscape, cybersecurity has become increasingly crucial. However, wireless sensor networks face unique...
-
Early web application attack detection using network traffic analysis
The number of deployed web applications and the number of web-based attacks in the last decade are constantly increasing. One group of tools that...

-
A survey on run-time packers and mitigation techniques
The battle between malware analysts and malware authors is a never-ending challenge with the advent of complex malware such as polymorphic,...

-
IRADA: integrated reinforcement learning and deep learning algorithm for attack detection in wireless sensor networks
Wireless Sensor Networks (WSNs) play a vital role in various applications, necessitating robust network security to protect sensitive data. Intrusion...

-
Intelligent Solutions for Attack Mitigation in Zero-Trust Environments
Many of today’s smart devices are rushed to market with little consideration for basic security and privacy protection, making them easy targets for...
-
Attack and anomaly prediction in networks-on-chip of multiprocessor system-on-chip-based IoT utilizing machine learning approaches
The proliferation of multiprocessor system-on-chip (MPSoC) architectures within the Internet of Things (IoT) has introduced notable security...

-
Intrinsic Weaknesses of IDSs to Malicious Adversarial Attacks and Their Mitigation
Intrusion Detection Systems (IDS) are essential tools to protect network security from malicious traffic. IDS have recently made significant...
-
A novel botnet attack detection for IoT networks based on communication graphs
AbstractIntrusion detection systems have been proposed for the detection of botnet attacks. Various types of centralized or distributed cloud-based...

-
DDoS attack detection using MLP and Random Forest Algorithms
Distributed Denial of Service (DDoS) attacks continue to be the most dangerous over the Internet. With the rapid advancement of information and...

-
Belief-DDoS: step** up DDoS attack detection model using DBN algorithm
Distributed Denial of Services (DDoS) attacks severely impact various systems. Traditional approaches like signature-based and scrubbing methods...

-
Measuring and achieving test coverage of attack simulations extended version
Designing secure and reliable systems is a difficult task. Threat modeling is a process that supports the secure design of systems by easing the...

-
Optimized Edge-cCCN Based Model for the Detection of DDoS Attack in IoT Environment
In the context of the Internet of Things (IoT), safeguarding against Distributed Denial of Service (DDoS) attacks is critical. This paper introduces...
