Search
Search Results
-
Robust T-Loss for Medical Image Segmentation
This paper presents a new robust loss function, the T-Loss, for medical image segmentation. The proposed loss is based on the negative log-likelihood...
-
Adaptive Prototype Triplet Loss for Cross-Resolution Face Recognition
Although face recognition has achieved great success in many areas, cross-resolution face recognition (CRFR) still remains a challenging task due to...
-
Ethical Reflection on Identity of AI Digital Avatars
This article explores the impact of artificial intelligence (AI) on human identity and raises ethical concerns regarding using biometric data for...
-
INCHAIN: a cyber insurance architecture with smart contracts and self-sovereign identity on top of blockchain
Despite the rapid growth of the cyber insurance market in recent years, insurance companies in this area face several challenges, such as a lack of...

-
Identity and Access Management (IAM)
Identity and Access Management (IAM) stands as a cornerstone in cybersecurity, orchestrating the intricate dance of user identities, permissions, and...
-
Whole constraint and partial triplet-center loss for infrared-visible re-identification
In this paper, we propose a hybrid cross-dual-path feature learning network (HCDFL) to learn local discriminative characteristics and exploit a novel...

-
Deep Face Recognition with Cosine Boundary Softmax Loss
To improve the accuracy of face recognition when there are wrong-labeled samples, a new deep face recognition model with cosine boundary loss is...
-
When blockchain meets IoT: a comparison of the performance of communication protocols in a decentralized identity solution for IoT using blockchain
Internet of Things (IoT) is a rapidly expanding technology composed of devices embedded with sensors, specialized hardware, and software to connect...

-
Brain Intervention Therapy Dilemma: Functional Recovery versus Identity
Neuroethics addresses the issue of transformations in personal identity induced by brain intervention therapy. The advent of Brain-Machine Interfaces...
-
Adv-Triplet Loss for Sparse Attack on Facial Expression Recognition
The susceptibility of current Deep Neural Networks (DNNs) to adversarial examples has been a significant concern in deep learning methods. In...
-
A Bitcoin-Based Digital Identity Model for the Internet of Things
Cybersecurity in the Internet of Things (IoT), at its heart, relies on the digital identity concept to build security mechanisms such as...
-
The role of students’ relational identity and autotelic experience for their innovative and continuous use of e-learning
Over the last decades, using e-learning systems as an alternative format of education for traditional classroom has been growing in higher education...

-
An Advanced Hierarchical Identity-Based Security Mechanism by Blockchain in Named Data Networking
Named data networking (NDN) has been viewed as a promising future Internet architecture due to its data-centric design. It requires a new security...

-
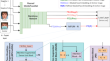
Boosting facial recognition capability for faces wearing masks using attention augmented residual model with quadruplet loss
Masked face recognition gained importance after the outbreak of COVID-19 when people started wearing facial masks to protect themselves against...
-
Single image dehazing via cycle-consistent adversarial networks with a multi-scale hybrid encoder-decoder and global correlation loss
Deep learning technologies have been resha** the research of image dehazing in recent years with superior performance. Due to the difficulty to...

-
Receiver selective opening security for identity-based encryption in the multi-challenge setting
Receiver selective opening (RSO) security requires that in a situation where there are one sender and multiple receivers, even if an adversary has...

-
Identity-Preserved Face Beauty Transformation with Conditional Generative Adversarial Networks
AbstractIdentity-preserved face beauty transformation aims to change the beauty scale of a face image while preserving the identity of the original...

-
A Tightly Secure Identity-Based Signature Scheme from Isogenies
We present a tightly secure identity-based signature (IBS) scheme based on the supersingular isogeny problems. Although Shaw and Dutta proposed an...
-
Disruption, technology and the question of (artificial) identity
The current state of human–machine interaction has set forth a process of hybridization of human identity. Technology—and most notably AI—is used as...
-
Training Parameterized Quantum Circuits with Triplet Loss
Training parameterized quantum circuits (PQCs) is a growing research area that has received a boost from the emergence of new hybrid quantum...
