Search
Search Results
-
LATA: learning automata-based task assignment on heterogeneous cloud computing platform
A cloud computing environment is a distributed system where idle resources are accessible across a wide area network, such as the Internet. Due to...

-
Exploring low-level statistical features of n-grams in phishing URLs: a comparative analysis with high-level features
Phishing attacks are the biggest cybersecurity threats in the digital world. Attackers exploit users by impersonating real, authentic websites to...
-
A cloud-fog distributed trust service for wireless sensor networks
In wireless sensor networks (WSNs), data aggregation techniques are used to reduce energy consumption of the sensors and extend the network lifetime....

-
Empowering e-learning approach by the use of federated edge computing
Federated learning (FL) is a decentralized approach to training machine learning model. In the traditional architecture, the training requires...

-
Hardware architecture and memristor-crossbar implementation of type-2 fuzzy system with type reduction and in-situ training
The Type-2 fuzzy set is a fuzzy set with fuzzy membership degrees. This set is used when accurately determining the membership degree of a fuzzy set...

-
IoV security and privacy survey: issues, countermeasures, and challenges
As a growing up-and-coming branch of the Internet of Things and traditional vehicular ad hoc networks, the Internet of Vehicles (IoV) is intended to...

-
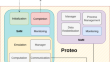
Proteo: a framework for the generation and evaluation of malleable MPI applications
Applying malleability to HPC systems can increase their productivity without degrading or even improving the performance of running applications....
-
Metaheuristic algorithms and their applications in wireless sensor networks: review, open issues, and challenges
Metaheuristic algorithms have wide applicability, particularly in wireless sensor networks (WSNs), due to their superior skill in solving and...

-
Blockchain enabled secure pharmaceutical supply chain framework with traceability: an efficient searchable pharmachain approach
The complex networks of manufacturers, suppliers, retailers, and customers that make up today’s pharmaceutical supply chain span worldwide. As it is,...

-
Enhancing 3D localization in wireless sensor network: a differential evolution method for the DV-Hop algorithm
Wireless sensor network is large-scale, self-organizing and reliable. It is widely used in the military, disaster management, environmental...

-
Service selection based on blockchain smart contracts in cloud-edge environment
The rapid integration of cloud computing and edge computing has brought the cloud-edge environment into the spotlight in information technology....

-
Energy-Constrained DAG Scheduling on Edge and Cloud Servers with Overlapped Communication and Computation
Mobile edge computing (MEC) has been widely applied to numerous areas and aspects of human life and modern society. Many such applications can be...
-
An anonymous authentication with blockchain assisted ring-based homomorphic encryption for enhancing security in cloud computing
Nowadays, the need for cloud computing has increased due to the exponential growth in information transmission. Cybercriminals are persistent in...

-
Convolutional neural network (CNN) and federated learning-based privacy preserving approach for skin disease classification
This research displays inspect a study on the classification of human skin diseases using medical imaging, with a focus on data privacy preservation....

-
SDESA: secure cloud computing with gradient deep belief network and congruential advanced encryption
With the aim to enhance cloud security with higher data confidentiality rate and integrity, we propose a novel technique called Stochastic Deep...

-
A hybrid deep learning based enhanced and reliable approach for VANET intrusion detection system
Advances in autonomous transportation technologies have profoundly influenced the evolution of daily commuting and travel. These innovations rely...

-
A survey on privacy-preserving federated learning against poisoning attacks
Federated learning (FL) is designed to protect privacy of participants by not allowing direct access to the participants’ local datasets and training...

-
Saver: a proactive microservice resource scheduling strategy based on STGCN
As container technology and microservices mature, applications increasingly shift to microservices and cloud deployment. Growing microservices scale...

-
An encrypted deduplication scheme based on files diversity
In order to improve the efficiency of cloud storage, deduplication technology has been widely used. In personal cloud storage, files are diverse....

