Search
Search Results
-
A quantitative analysis of the security of PoW-based blockchains
This study analyzes the security implications of Proof-of-Work blockchains with respect to the stale block rate and the lack of a block verification...

-
A network intrusion detection system based on deep learning in the IoT
As industrial and everyday devices become increasingly interconnected, the data volume within the Internet of Things (IoT) has experienced a...

-
Intelligent and efficient task caching for mobile edge computing
Given the problems with a centralized cloud and the emergence of ultra-low latency applications, and the needs of the Internet of Things (IoT), it...

-
A fuzzy ontology-based context-aware encryption approach in IoT through device and information classification
IoT devices produce a vast amount of data ranging from personal to sensitive information. Usually, these devices remain connected to the internet so...

-
Research on satellite link allocation algorithm for Earth-Moon space information network
With ongoing advancements in space exploration and communication technology, the realization of an Earth-Moon space information network is gradually...

-
Machine learning-driven performance assessment of network-on-chip architectures
System-on-chip designs for high-performance computing systems widely use network-on-chip (NoC) technology. The critical metrics such as latency,...

-
A new integrated steganography scheme for quantum color images
In this paper, we propose a quantum steganography scheme with a color image as the cover image. In order to enhance the security of the embedded...

-
Exploring recent advances in random grid visual cryptography algorithms
Visual cryptography scheme is initiated to securely encode a secret image into multiple shares. The secret can be reconstructed by overlaying the...

-
Cost-aware workflow offloading in edge-cloud computing using a genetic algorithm
The edge-cloud computing continuum effectively uses fog and cloud servers to meet the quality of service (QoS) requirements of tasks when edge...
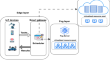
-
A principal label space transformation and ridge regression-based hybrid gorilla troops optimization and jellyfish search algorithm for multi-label classification
Classification as an essential part of Machine Learning and Data Mining has significant roles in engineering, medicine, agriculture, military, etc....

-
An adaptive service deployment algorithm for cloud-edge collaborative system based on speedup weights
In the contemporary landscape of edge computing, the deployment of services with stringent real-time requirements on edge devices is increasingly...

-
Exploring the potential of Wav2vec 2.0 for speech emotion recognition using classifier combination and attention-based feature fusion
AbstractSelf-supervised learning models, such as Wav2vec 2.0, extract efficient features for speech processing applications including speech emotion...

-
Cost-effective clonal selection and AIS-based load balancing in cloud computing environment
Cloud computing faces challenges in increasing efficiency through task scheduling and load balancing. Various load-balancing methods, including the...

-
Hyper star structure fault tolerance of half hypercube
The reliability of interconnection networks ordinarily is measured by all kinds of connectivities. The qualitative and quantitative analysis relies...

-
Natural noise management in collaborative recommender systems over time-related information
Recommender systems are currently a suitable alternative for providing easy and appropriate access to information for users in today’s digital...

-
An efficient quantum oblivious transfer protocol
Oblivious transfer (OT) is a significant two party privacy preserving cryptographic primitive. OT involves a sender having several pieces of...

-
Centrality-based and similarity-based neighborhood extension in graph neural networks
In recent years, Graph Neural Networks (GNNs) have become a key technique to address various graph-based machine learning tasks. Most of existing...

-
DEKGCI: A double-ended recommendation model for integrating knowledge graph and user–item interaction graph
User–item bipartite graphs and knowledge graphs are frequently employed in recommender systems due to their ability to provide rich information for...

-
Efficient MST-based clustering with leader node selection and outlier edge cutting
The clustering algorithm based on the minimum spanning tree (MST) can identify clusters of different shapes. However, the minimum spanning tree...

-
Multi-strategy improved sparrow search algorithm based on first definition of ellipse and group co-evolutionary mechanism for engineering optimization problems
The Sparrow Search Algorithm (SSA) is recognized for its rapid convergence and precision in engineering optimization, yet it faces the challenge of...

