Search
Search Results
-
Ensemble methods-based comparative study of Landsat 8 operational land imager (OLI) and sentinel 2 multi-spectral images (MSI) for smart farming crop classification
Agriculture has a significant worldwide impact in terms of generating employment opportunities and stimulating economic growth. In India, agriculture...

-
Optimizing pre-copy live virtual machine migration in cloud computing using machine learning-based prediction model
One of the preconditions for efficient cloud computing services is the continuous availability of services to clients. However, there are various...

-
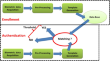
Proposed cancelable biometrics system based on hybrid optical crypto-steganography audio framework for cyber security applications
Biometric authentication systems have gained significant popularity in recent years due to their high level of security and convenience. Cancelable...
-
Adaptive context-aware access control for IoT environments leveraging fog computing
The increasing use of the Internet of Things (IoT) has driven the demand for enhanced and robust access control methods to protect resources from...

-
Using the ACE framework to enforce access and usage control with notifications of revoked access rights
The standard ACE framework provides authentication and authorization mechanisms similar to those of the standard OAuth 2.0 framework, but it is...

-
Visual saliency based maritime target detection
We present an unsupervised maritime target detection method based on visual saliency. From the perspective of maritime target detection as a salient...

-
Enhancing visual clarity in hazy media: a comprehensive approach through preprocessing and feature fusion attention-based dehazing
Particles in the atmosphere, such as dust and smoke, can cause visual clarity problems in both images and videos. Haze is the result of the...

-
A three-stage quality evaluation method for experience products: taking animation as an example
The diversity and dynamics of quality index information bring challenges to quality assessment of experience products. This paper proposes a...

-
End-to-End No-wait Scheduling for Time-Triggered Streams in Mixed Wired-Wireless Networks
Proprietary communication technologies for time-critical communication in industrial environments are being gradually replaced by Time-sensitive...

-
An efficient quantum oblivious transfer protocol
Oblivious transfer (OT) is a significant two party privacy preserving cryptographic primitive. OT involves a sender having several pieces of...

-
Automating shareable cyber threat intelligence production for closed source software vulnerabilities: a deep learning based detection system
Software can be vulnerable to various types of interference. The production of cyber threat intelligence for closed source software requires...

-
Multi-strategy improved sparrow search algorithm based on first definition of ellipse and group co-evolutionary mechanism for engineering optimization problems
The Sparrow Search Algorithm (SSA) is recognized for its rapid convergence and precision in engineering optimization, yet it faces the challenge of...

-
An improved weighted mean of vectors optimizer for multi-threshold image segmentation: case study of breast cancer
Women are commonly diagnosed with breast cancer (BC), and early detection can significantly increase the cure rate. This study suggested a...

-
Non-uniform magnetic fields for collective behavior of self-assembled magnetic pillars
Programmable and self-assembled magnetic pillars are essential to expanding the application domain of magnetic microparticle collectives. Typically,...

-
Accurate entropy modeling in learned image compression with joint enchanced SwinT and CNN
Recently, learned image compression (LIC) has shown significant research potential. Most existing LIC methods are CNN-based or transformer-based or...

-
A hybrid multi-objective algorithm based on slime mould algorithm and sine cosine algorithm for overlap** community detection in social networks
In recent years, extensive studies have been carried out in community detection for social network analysis because it plays a crucial role in social...

-
Automatic identification of Malvani dialects from audio signal based on hybrid FFO-TSO with deep neural network
Marathi language is originated from the geographical regions of Maharashtra, which include several different varieties of Malvani. The identification...

-
Ant lion optimization based inertia weight optimized KGMO for mobility Management in Heterogeneous LTE cellular networks
This study proposes a hybrid optimization-based mobility management strategy employing Kinetic Gas Molecular Optimization (KGMO) and Ant Lion...

-
TruPro: a blockchain-based decentralised prosumer electricity trading platform for electrical vehicles (EVs)
Electric vehicles (EVs) have attracted significant attention in recent years primarily due to minimal adverse impact on the environment and...

-
Leveraging large language model to generate a novel metaheuristic algorithm with CRISPE framework
In this paper, we introduce the large language model (LLM) ChatGPT-3.5 to automatically and intelligently generate a new metaheuristic algorithm (MA)...

